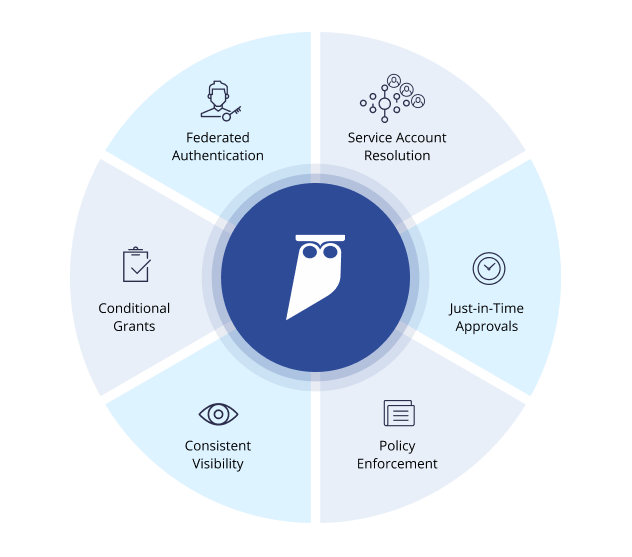
Data Access Governance
Data Access Governance for All Users
Cyral’s Data Access Governance (DAG) solution provides comprehensive and consistent policies for a variety of databases and data lakes, across all channels. Use data security contracts to manage policies for who is allowed to access which data and with what constraints. Enforce policies consistently across all privileged users, applications, BI tools and services.
Benefits of Cyral’s DAG
- Extend existing network policies to database accounts
- Use IAM policies to manage access to database roles
- Implement field-level policies for governance and privacy
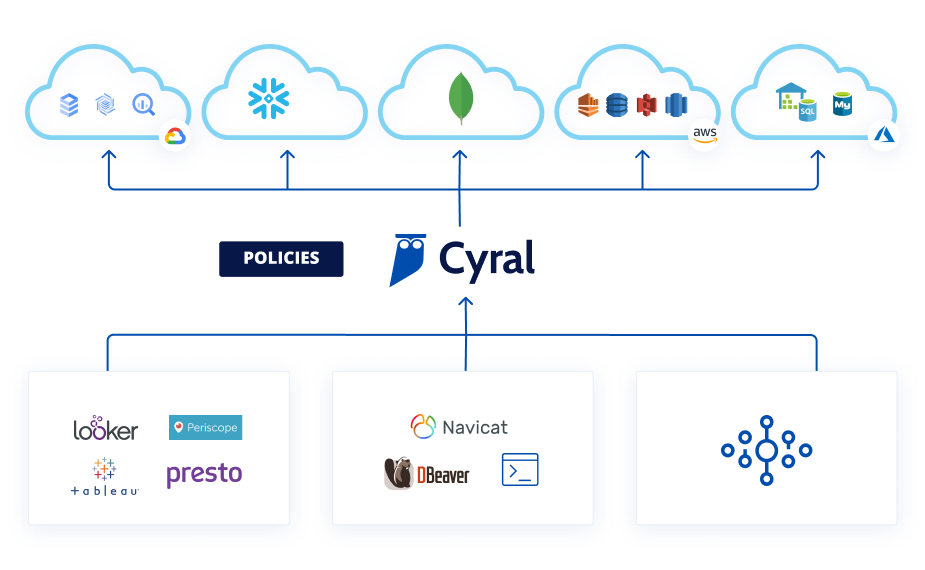
- All policies managed centrally, enforced externally
- No reliance on database policies with different behaviors
- Eliminate the need to manage role permissions

- Ensure policies for all privileged and business users
- Right-size privileges for users of BI tools and apps
- Policies can be implemented for ETL jobs and services
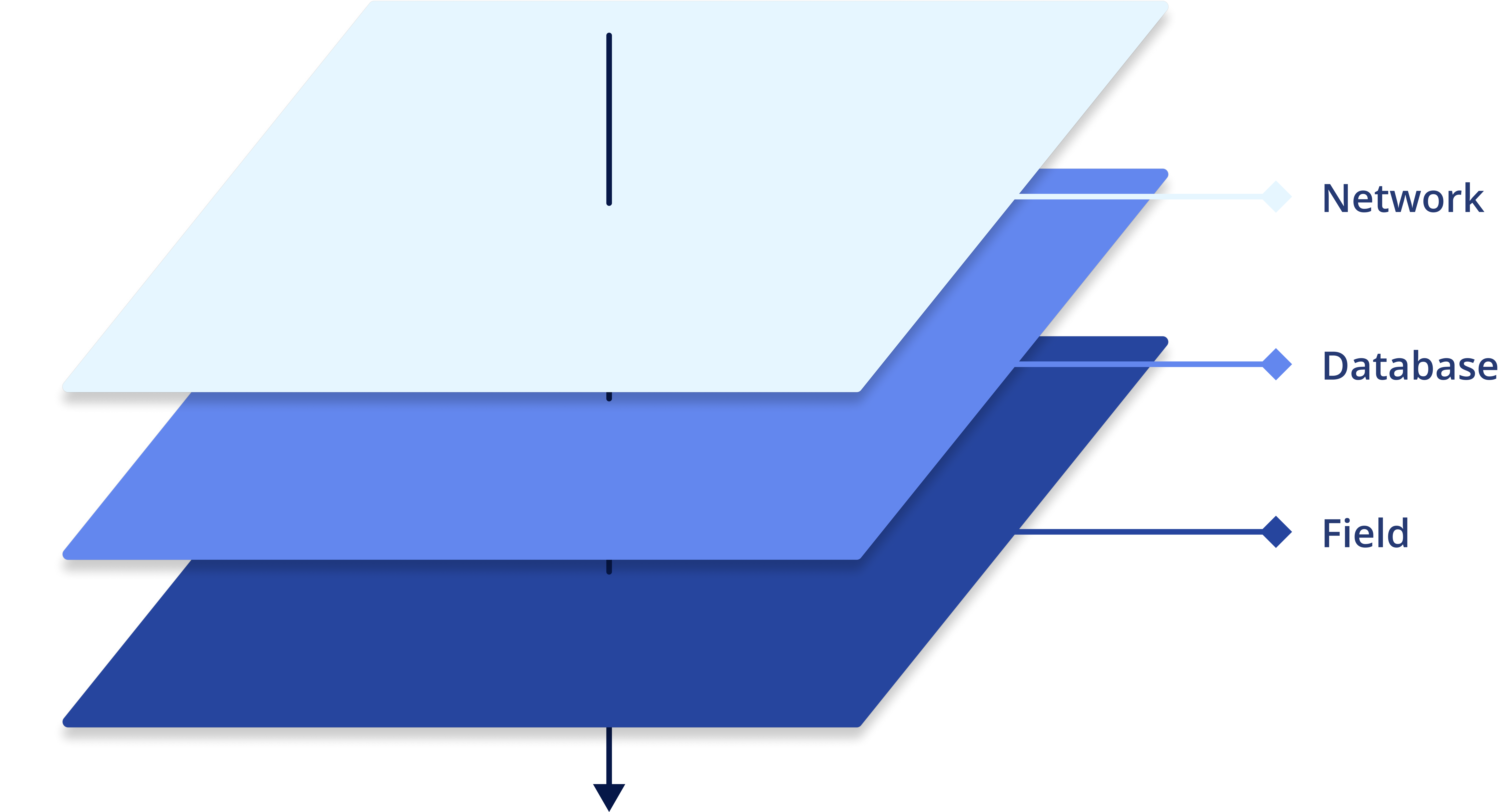
DAG at the network-level
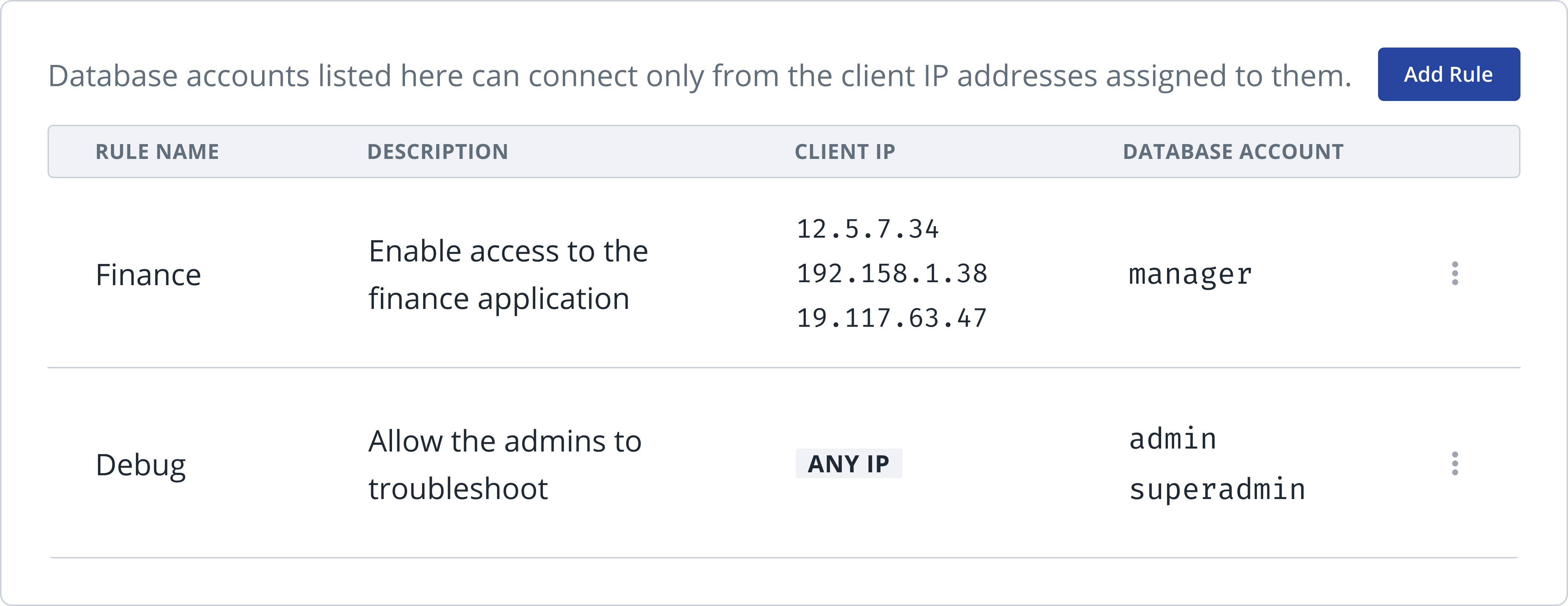
- Restrict access to certain accounts from trusted networks
- Leverage network governance to manage privileged access
- Learn more about our Network Shield
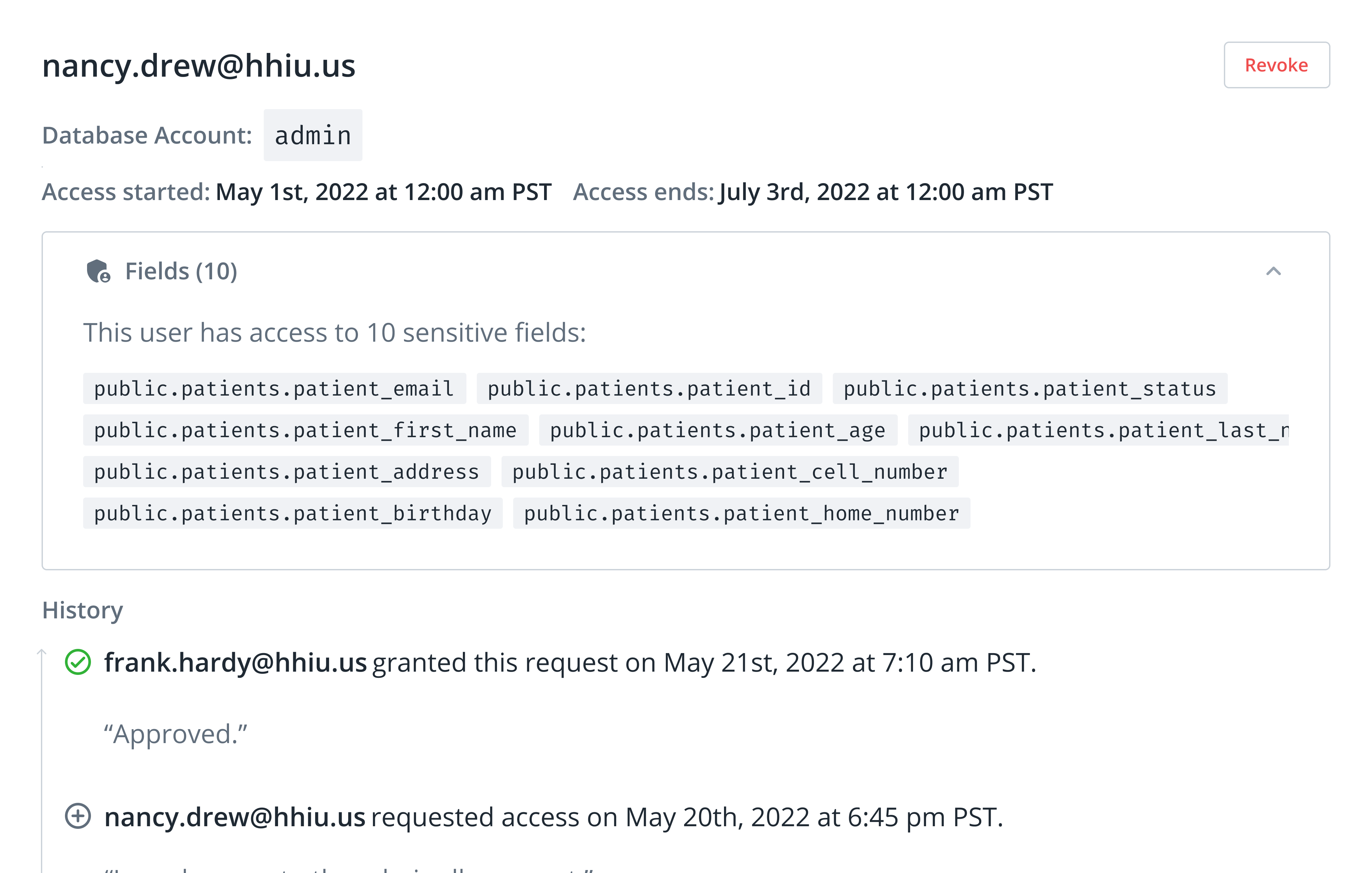
DAG at the database-level
- Restrict access to database roles based on IAM entitlements
- Leverage IAM governance to manage access to databases
- Learn more about our data access governance management
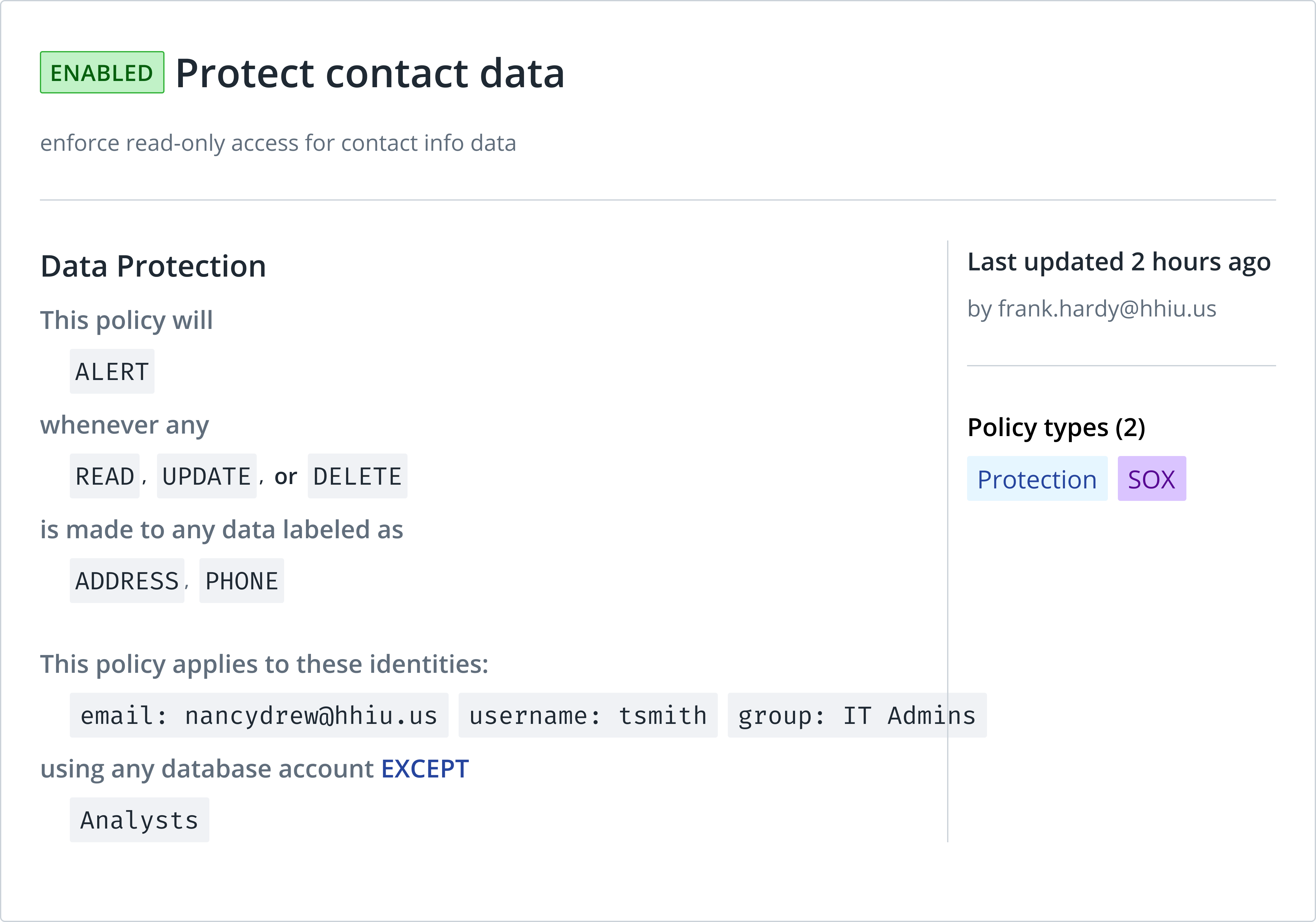
DAG at the field-level
- Restrict access to sensitive fields based on policies
- Use data security contracts to apply fine-grain governance
- Learn about privilege managemement using database roles
Ready to Get Started?
Get started in minutes and explore how Cyral’s database activity monitoring solutions can protect your data. Learn more about Cyral’s Database Activity Monitoring. You can also contact us to see a live demo.




