Data Access Control
Data Access Control Definition
Data access control is the ongoing and continuous practice of implementing robust policies, tools, and technologies to restrict access to data in a computing environment. Data access control is a fundamental tool in data security with an overarching goal of minimizing risk to the organization by defining and controlling who has access to which data.
Data Access Control FAQs
What is Data Access Control?
Data access control consists of the logical tools, technologies, and methodologies implemented in an organization to regulate who can access or use different classes of data. The two main components of data access control are multi-factor authentication, which involves verifying the identity of a user, and authorization, which uses predefined policies to determine the level of access as well as the types of activities a user can perform. In order to be successful, authentication and authorization must be an ongoing and continuous implementation across every level of every department in an organization.
Data Access Control Methods
Various access control methods exist to regulate resource access, each offering unique approaches to address specific security requirements:
- Discretionary Access Control (DAC): In this model, the data owner decides who is able to access their data. The owner sets policies that determine which companies and people are authorized to access different types of data. This flexibility makes it ideal for smaller organizations. This is the least restrictive model as there is no central authority over where and how the content can be accessed.
- Mandatory Access Control (MAC): This model is based on a central authority. Employees are able to access company resources according to the level of risk they present and their access requirements. The administrator classifies available resources and users into different risk levels and assigns users based on privileges they possess.
- Role-Based Access Control (RBAC): Regulating access based on roles is the most widely used model as it conforms to the roles and needs of every individual in an organization. It ensures that any user with the least privilege possible can only access data they need to do their job. If unauthorized individuals attempt to access sensitive information, they are restricted.
- Attribute-Based Access Control (ABAC): Granted access in an attribute-based model is based on a set of attributes and environmental conditions, which include factors such as time and location, assigned to both users and data resources. This provides flexibility as the attributes and their values can be modified without needing to change the relationship between object and subject.
- Policy-Based Access Control (PBAC): Provides fine grain access control to resources based on predefined policies, granting or denying access according to specific rules which enhances security. PBAC allows for more granular control than RBAC by considering dynamic factors like user attributes and environmental conditions.
How to Implement Data Access Control
Access control protects data on a computer against a variety of security threats, such as breaches, unauthorized access, unauthorized activities, unauthorized movement, and more. Keeping track of every point of data, how it is used, and by whom, is impractical without implementing modern data access control solutions. Implementing data access controls into an organization typically involves leveraging data access control tools like identity management and access management platforms. These tools provide software for access control, a database for all authorized users, and management tools for data access control policy, audits, and enforcement.
Automated identity and data access management solutions provide centralized, unified control over data across the organization; automate tasks such as provisioning; and ensure compliance with regulations like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA).
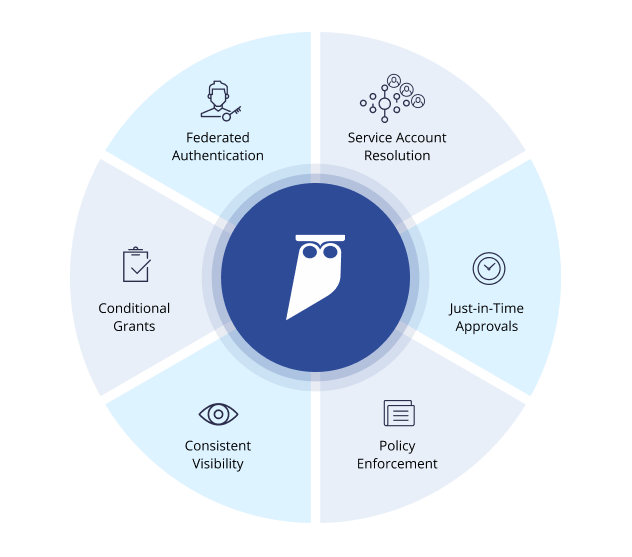
Advanced modern data access control systems provide consistent visibility into all data activity, automated alerts for suspicious events, Just-In-Time access approvals, dynamic access management, and the ability to eliminate shared accounts for databases.

Why is Data Access Control Important?
Access control data security is a critical investment to any organization that wants to make sure that data does not end up being taken from the organization or in unauthorized hands. It is vital that sensitive data, such as personal data related to clients or customers, classified documents, and more, are protected by the organizations that store them with a robust big data access control system that will help reduce the chance of a data leak.
With the increased use of diversified cloud architectures, the modern data landscape presents more access points than ever before. This presents a major challenge for businesses striving to effectively implement cloud data access control and monitor database activity in real-time. It is crucial for enterprises to adopt increasingly sophisticated tools and technologies to implement a proactive data security strategy that can maintain control of individual data sources residing in cloud repositories, as well as maintain regulatory compliance.
Does Cyral Offer a Data Access Control Solution?

The Cyral platform provides a robust data access control solution that simplifies data management and security processes by providing streamlined tools that help users easily control who has access to what data. Cyral’s intuitive account administration capabilities enable administrators to quickly and easily authenticate users into databases and data lakes using their SSO credentials.
Cyral’s services are transparent to databases and help users leverage a wide variety of tools, such as DBeaver, pgAdmin, Toad, Jupyter, and more, to securely access data. Featherweight, stateless interception services can be easily deployed in cloud-native or on-premises environments. With Cyral, users can confidently observe, control, and protect their data endpoints without sacrificing on performance and scalability.
Streamline Reports & Feedback: System admins need to be able to quickly report their findings to the right people in a concise manner. To achieve this, a feedback loop should exist between observability systems and the help desk. Issue reports should be delivered to IT in real-time, and business impact reporting should be simple and easily communicate the bottom line to anyone.


