Access Management for Data Teams
Easily Manage Access to your Data for Analytics and Modeling
Safely enable your data teams to access your data at scale. Eliminate the insecure use of shared service account credentials when accessing databases. Log every action to improve auditability.
Simplify and Broaden Data Access for all Users
- Eliminate complicated access workflows to S3, RDS and more for technology users
- Enable SSO to Redshift, Snowflake and other data repositories using AD
- Manage access across all data on an individualized basis

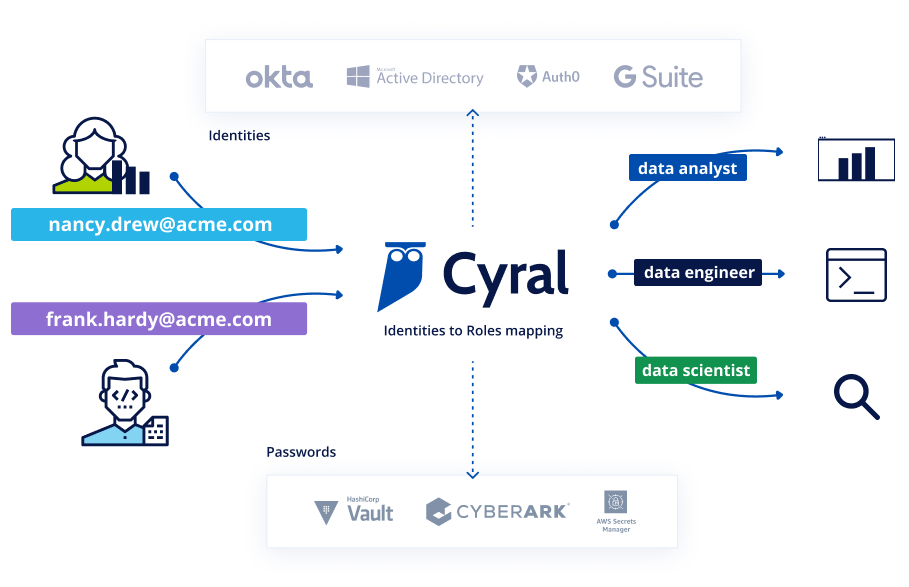
Eliminate Shared Credentials from Access Workflows
- Centralize authentication on your Identity Provider when connecting to any data repository
- Secure passwords in your secrets manager and enable automatic rotation
- Minimize your attack surface by removing standing privileges
Enrich Data Activity Trails with User Identity
- Enrich all data activity with information from your identity provider, including SSO user, group, and user attributes
- Leverage the tools of your choice for consuming and analyzing your logs
- Speed up forensics, audits and troubleshooting
Admin Setup Workflow

Gather all your permissions:
- Administrative access to your Cyral Control Plane
- IdP permissions to add a new application integration
- Access to your secrets manager
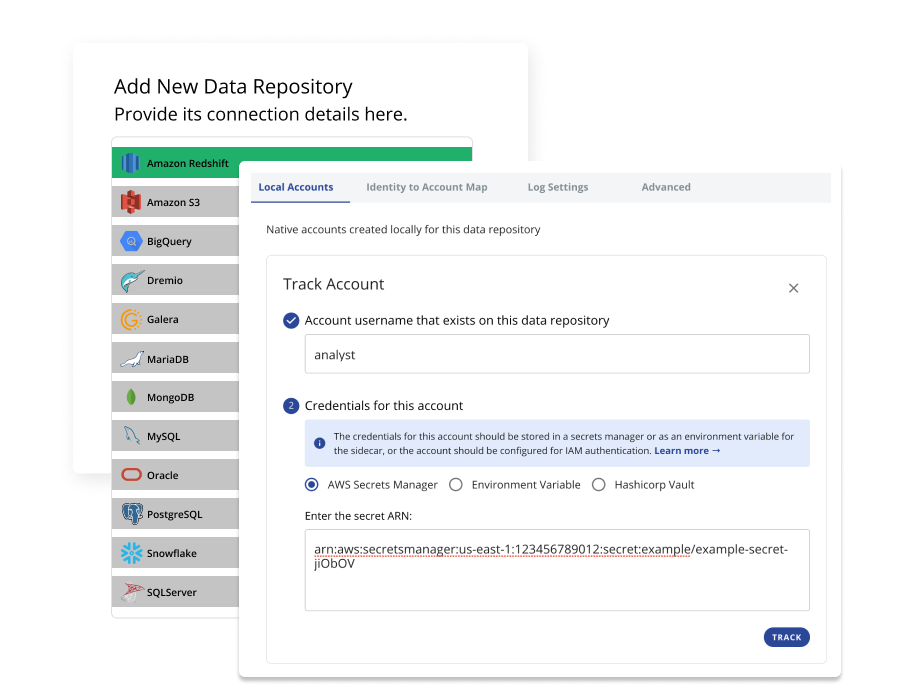
Set up the database for secure access
- Track it as a data repository in your Cyral Control Plane
- Provide Cyral with location of local account credentials for the repository

Enable users to authenticate with their IdP credentials
- Map users in IdP to the local accounts on your database
- Set a time-based expiration on the mapping(s) or allow unlimited access

Require all repository access go through the Cyral sidecar
- Rotate passwords from your local database accounts
- Distribute your Cyral Control Plane link for users to retrieve their access tokens

Users authenticate with their corporate credentials. Cyral generates activity logs with detailed context and identity information.
Terminology
Terminology
Data Activity Monitoring
Database Activity Monitoring (DAM) refers to any solution that is used to actively monitor and analyze database activity. This technology is multipurpose, typically being used by organizations both to fulfill specific compliance criteria, as well as protect their most sensitive data from external hackers and malicious insiders.
Data Cloud
The Data Cloud is an ecosystem of cloud-based services to store, process and analyze operational, business intelligence, and other data from systems of records spanning databases, data warehouses, and data pipelines. Examples of such services include Snowflake, BigQuery, Atlas, RedShift, Looker, Tableau, FiveTran, Kafka, S3, and others.
Data Privacy vs. Security
Data security and data privacy may seem similar, but the two represent distinct practices that work in concert together to protect the data we care about. The key to data privacy lies in the proper use and protection of controls that govern what data is shared with whom. Data security meanwhile is the fundamental protection of that data and all associated metadata from external entities. For example, if you choose to share photos with your best friend on a new app, but by doing so, you allow the company to resell those photos, that would be a breach of privacy. If on the other hand, you choose to share photos with your best friend, and the app suffers an incident whereby someone is allowed to access all of your details, that would be a breach of data security.
Access Management
On-call access management or incident access management is the set of procedures and policies that provide necessary access to those employees who are on-call and/or responding to an incident. For companies operating according to the Principle of Least Privilege (PoLP), managing access for on-call teams presents a challenge: the on-call rotation needs fast, privileged access so they can handle incidents, but PoLP demands that each employee only has minimal rights, by default. Today’s API-driven environment offers ways to overcome this challenge: companies can use Security as Code and Policy as Code to grant access in an emergency situation without having to worry about latent excess permission for all employees.
SSO
A Single Sign On (SSO) system uses a separate identity provider (IdP) to validate a user’s identity. Given this external identity (provided usually via SAML or ODIC), the application can make authorization decisions without needing to store a user’s credentials or verify the user’s identity.
IdP
An identity provider (IdP) authenticates a user and provides identity and access tokens for accessing other services. It uses SAML and OIDC protocols to interact with clients and is backed by a directory service storing user information.
Get Started with a
Free Trial
Get started in minutes: Explore how Cyral can protect your Data Mesh with our free trial. You can also contact us to see a live demo.

