Attribute-Based Access Control
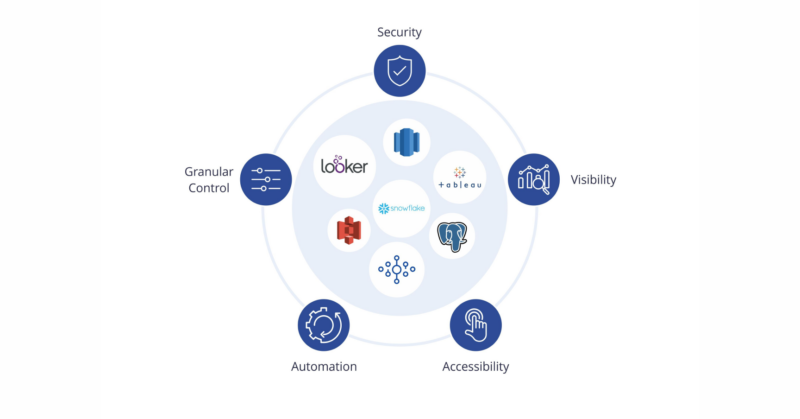
Granular Authorization for Databases and Data Lakes
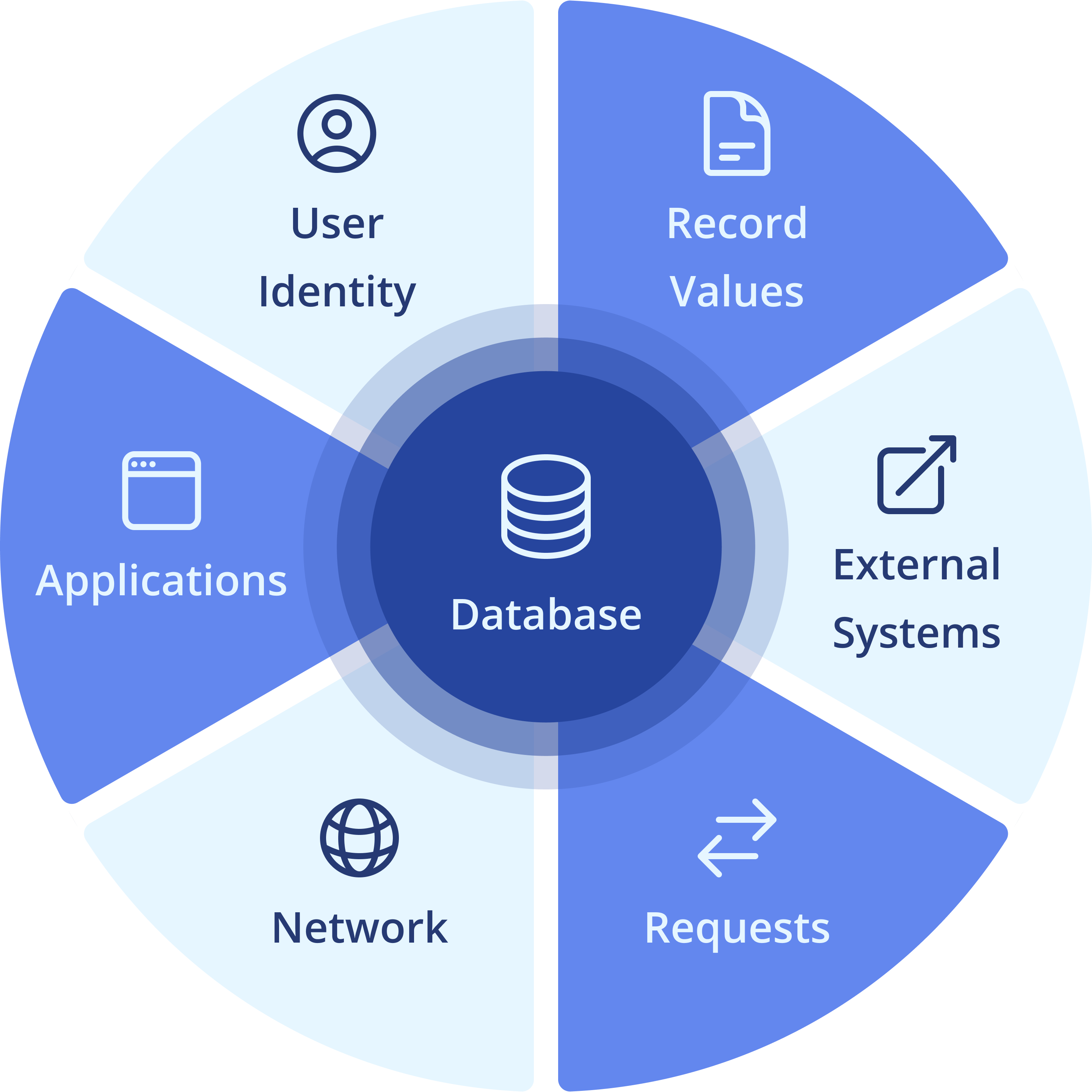
Attribute-based access control (ABAC) utilizes user and system attributes to provide fine-grained control over who can access specific datasets. It involves granting or denying access based on attributes such as user identity, time, location, and other contextual information to safeguard sensitive information, meet compliance requirements, and fortify against unauthorized access.
Elevate ABAC with Data Security Contracts
IAM based policy specification
Record-level access control
Simplified permissions management
Manual, decentralized remediation
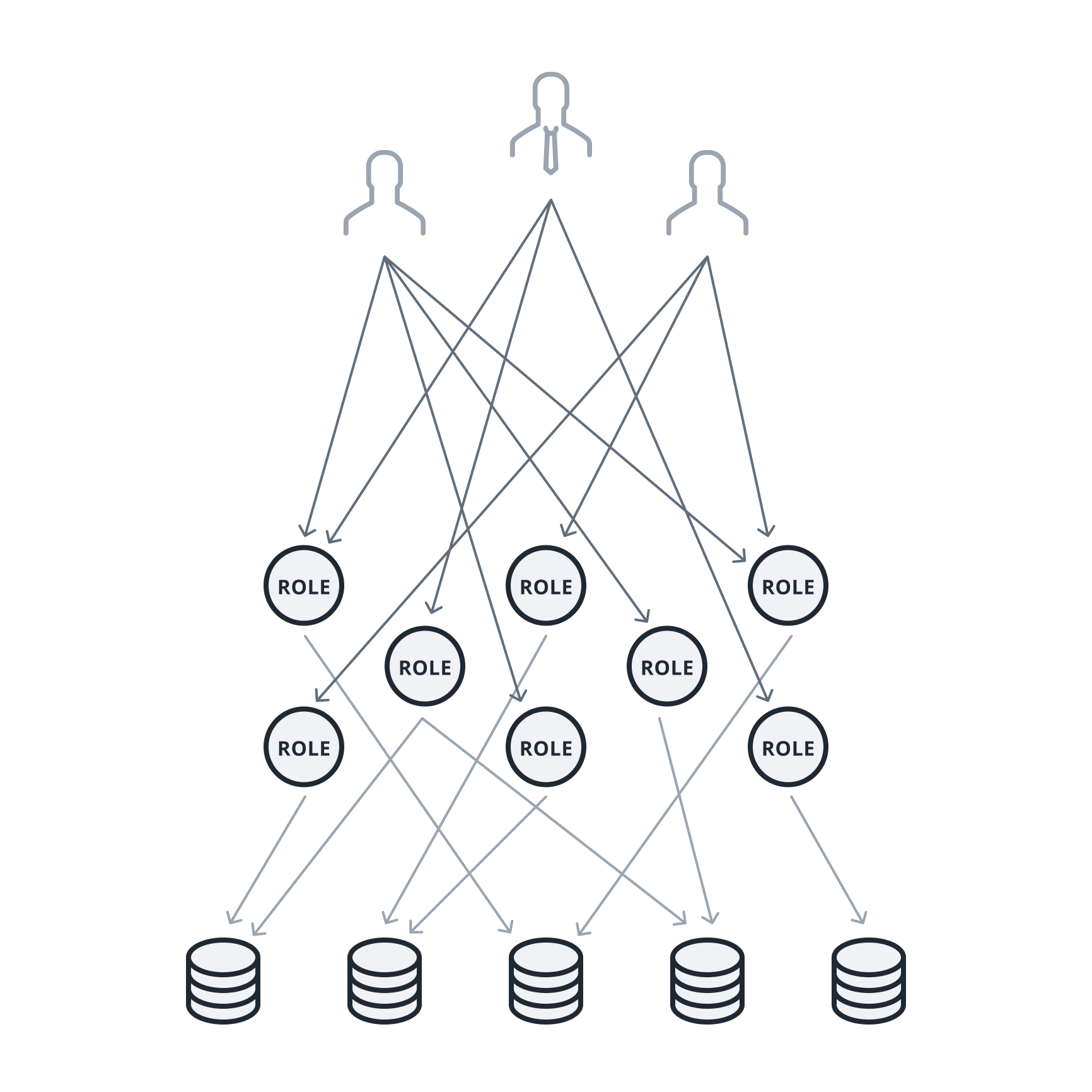

Manual, decentralized remediation
Access managed using database roles and permissions, which are disjointed from IAM entitlements, managed ad-hoc by data teams. Multiple application users share the same role.
- Limited, coarse-grained privileges
- Complex, ad-hoc policy management
- Lack of separation of duties and assurance
- Shadow access by service accounts
Automatic, centralized remediation
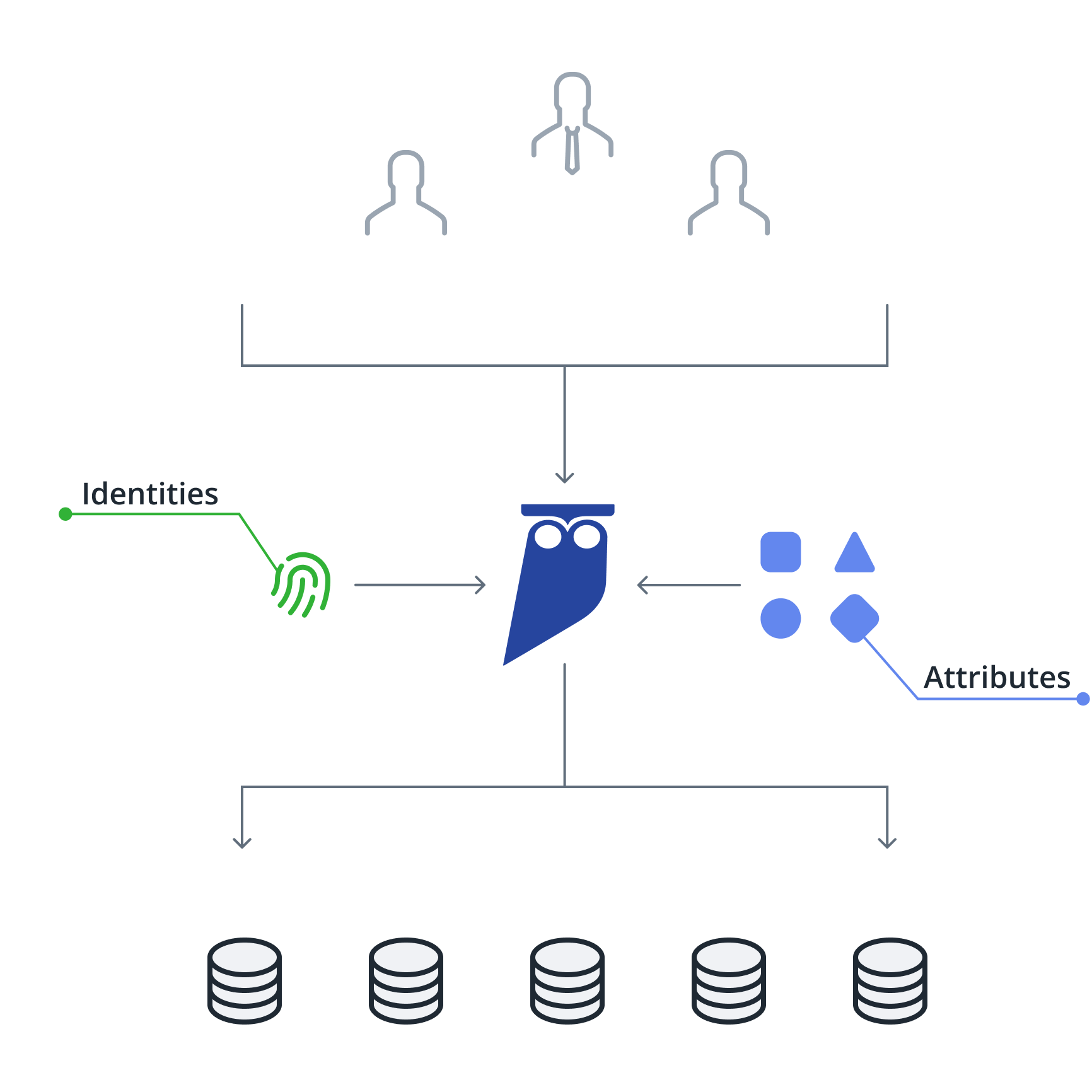


Automatic, centralized remediation
Access managed using central identities and entitlements. Policies managed centrally with no impact to data users. Policies applied consistently to direct and apps.
- Simplify policy creation and management
- Apply policies to rows, columns and objects
- Wide range of constraints supported
- Identify and govern service account users
An End-To-End ABAC Solution
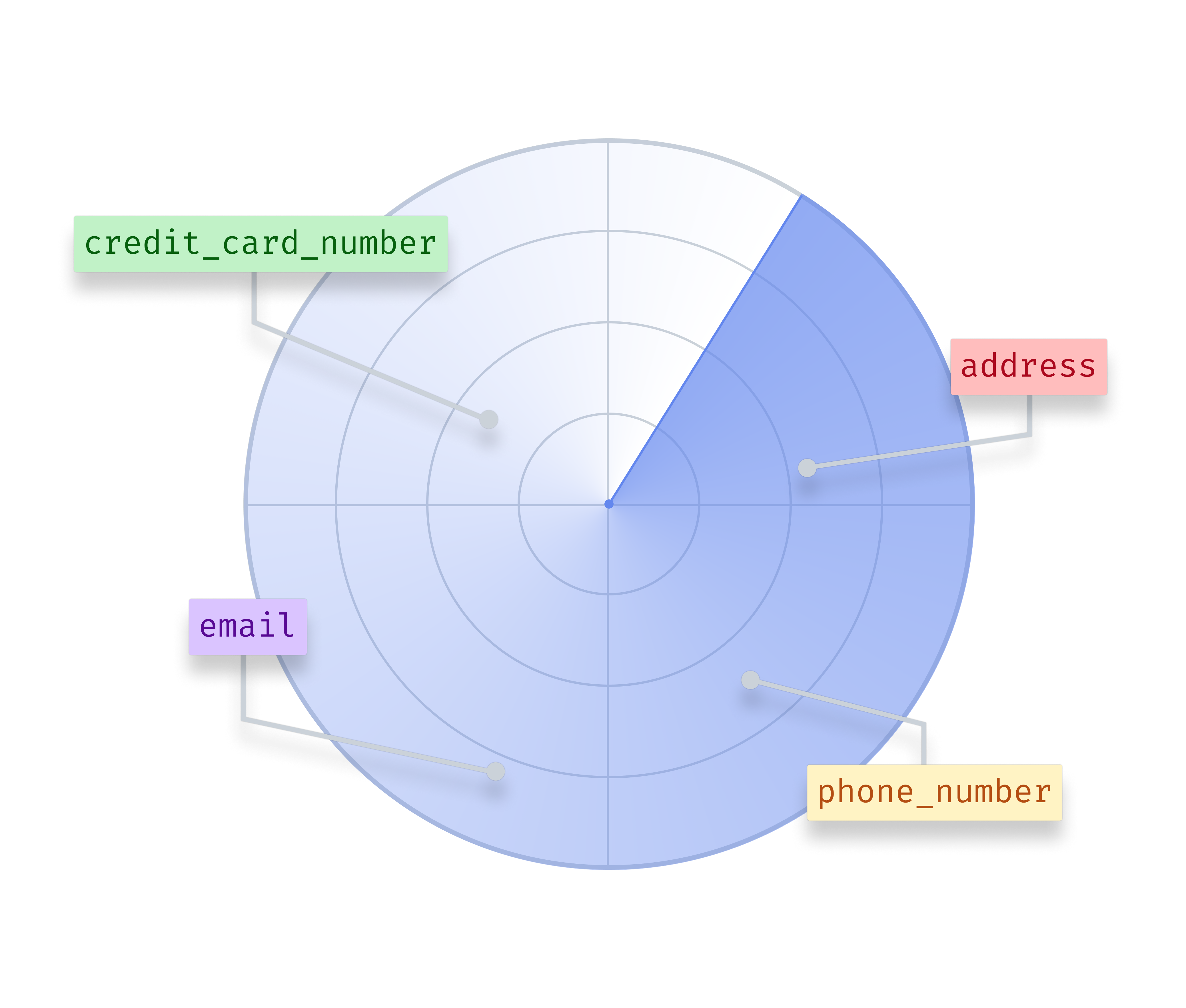
- Identify sensitive data and classify according to risk
- Prioritize policies for sensitive and at-risk data
- Ensure that policies follow the data across the data layer
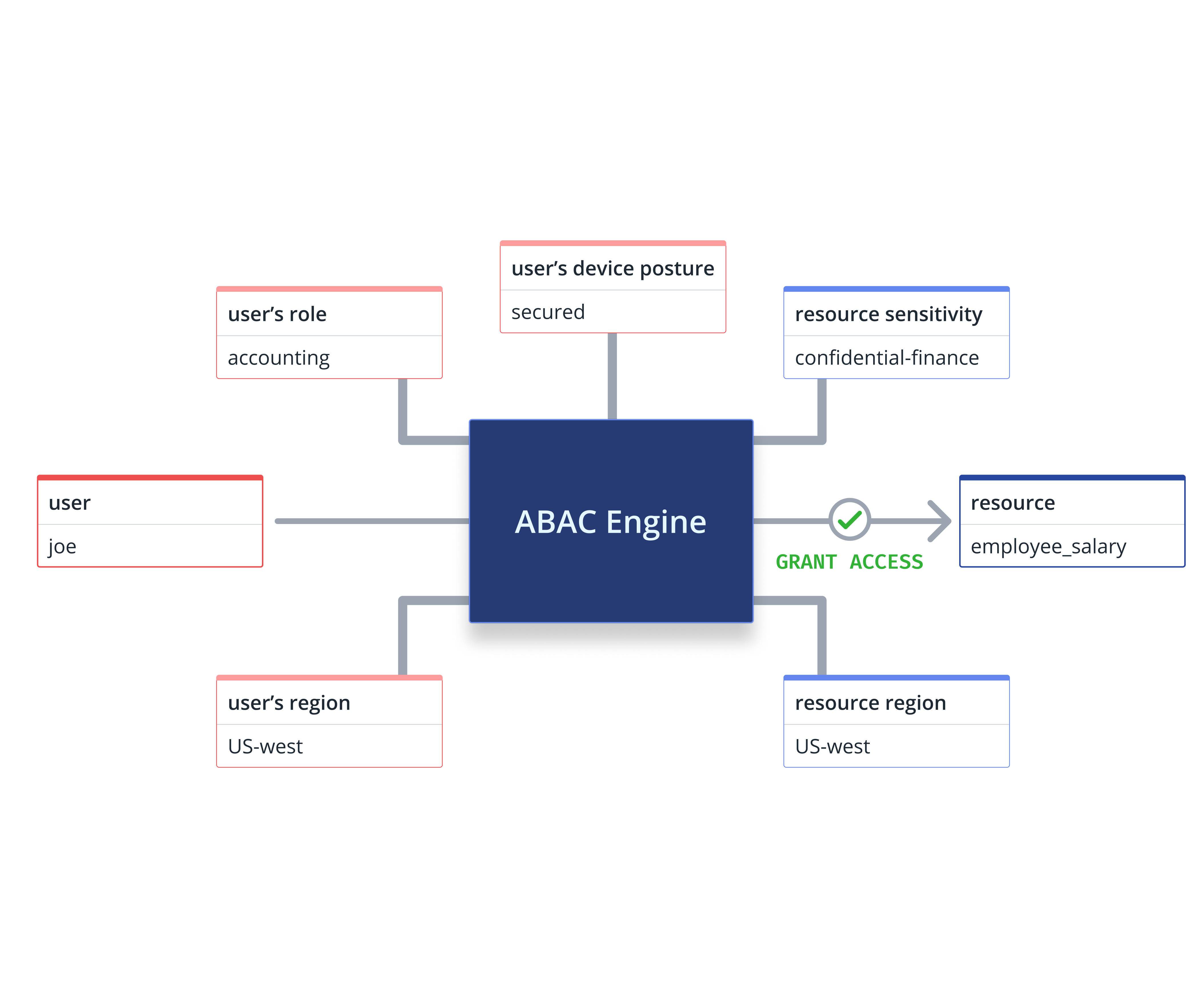
- Mask, obfuscate and de-identify data
- Prevent accidental and malicious tampering of data
- Prevent data spillage across environments
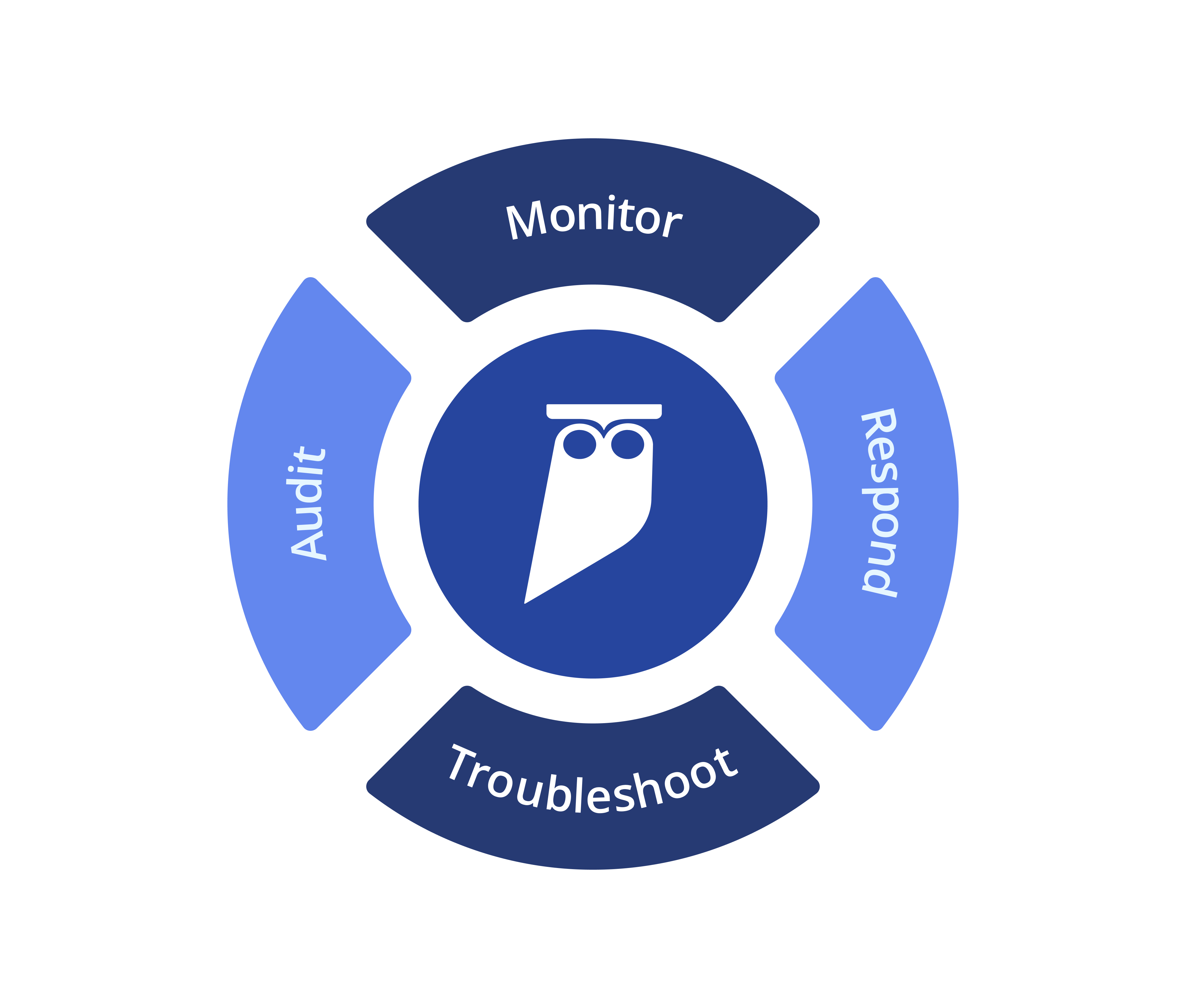
- Real-time, unified visibility into all data access
- Granular reporting on who is allowed to access what
- Alerting and response on unexpected activity