Network Shield
Network security for database accounts
Restrict access to sensitive database accounts from known, authorized locations. Easily specify policies for both users and applications.
Before
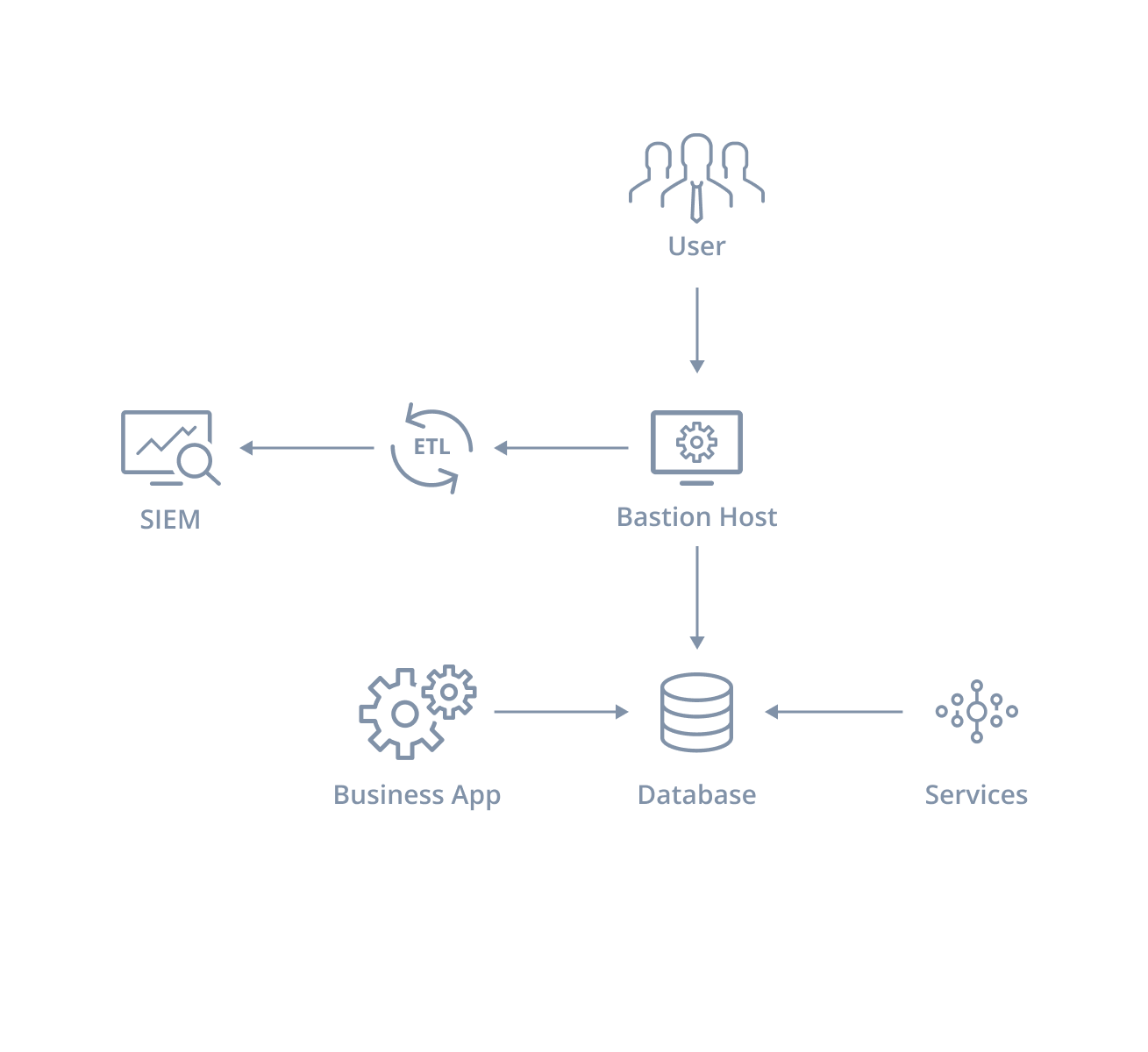

Before
Users connect to cloud databases by first logging into a bastion host within a trusted network, with voluminous keylogging implemented. Applications connect directly.
- Awkward user workflows with multiple authentication steps
- Does not work for applications and external users
- Multiple logs needing cleaning and synthesis
After
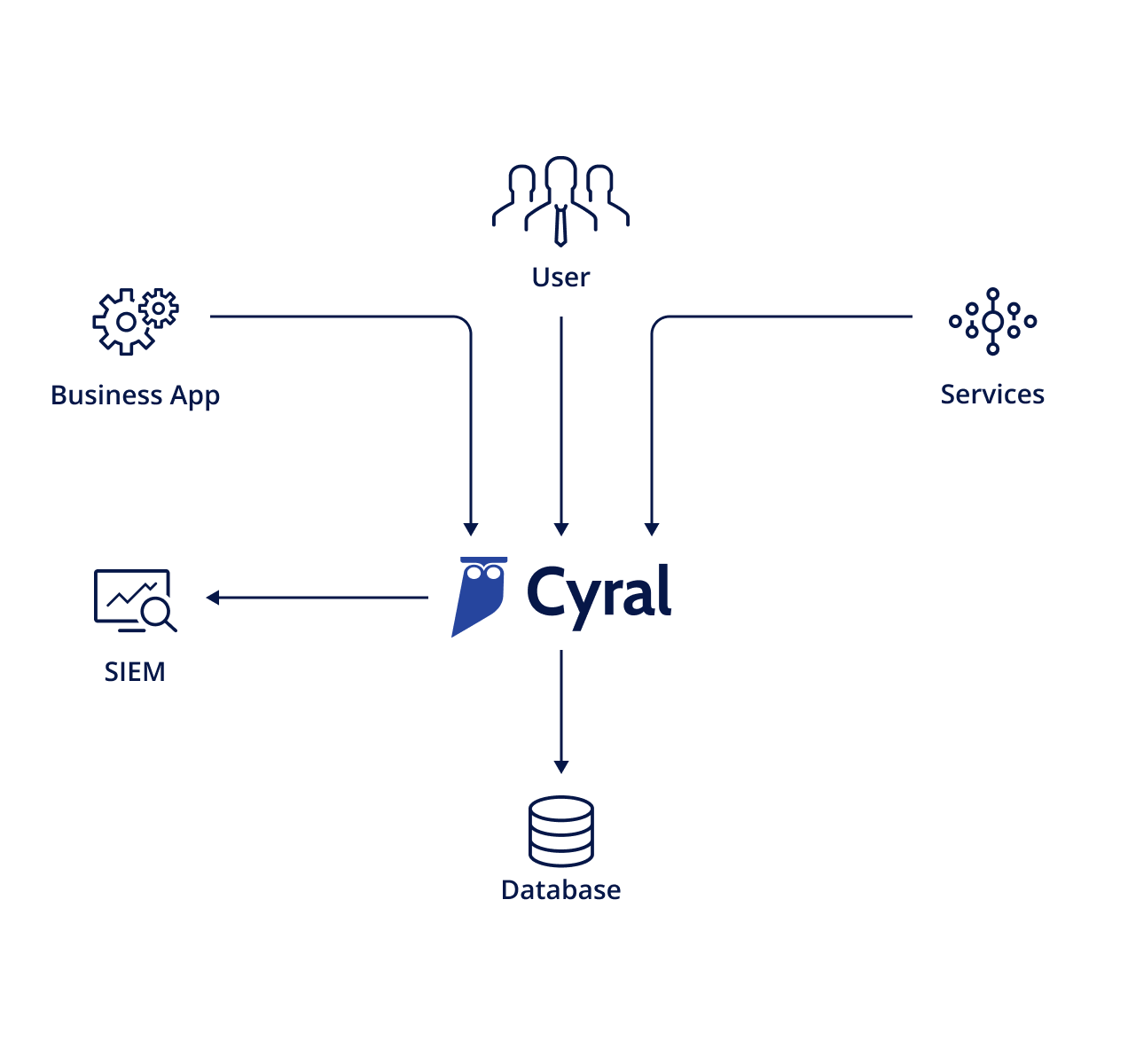


After
All users and applications connect to the database, routed transparently through Cyral. In a single place all checks are enforced, and clear audit trails are generated.
- Works easily for all users and applications
- Self-contained logs, no data cleansing needed
- Unified controls for implemented database access
Advantage of Cyral over traditional network controls
| Security Groups | ACL | |
|---|---|---|
| Controls access at database account level | Controls access at instance level | Controls access at network level |
| Operates at Layer 7 | Operates at Layer 4 | Operates at Layer 4 |
| Supports allow rules only | Supports allow rules only | Supports allow and deny rules |
| Request results are automatically allowed | Request results are automatically allowed | Request results must be explicitly allowed |
Benefits of Network Shield
Implement defense-in-depth
Simplify troubleshooting and forensics
Centralize all database controls
Prevent credential abuse
Improve database performance
Get Started with a
Free Trial
Get started in minutes: Explore how Cyral can protect your Data Mesh with our free trial. You can also contact us to schedule a live demo for a custom production security definition. Discover data privacy in production today.




