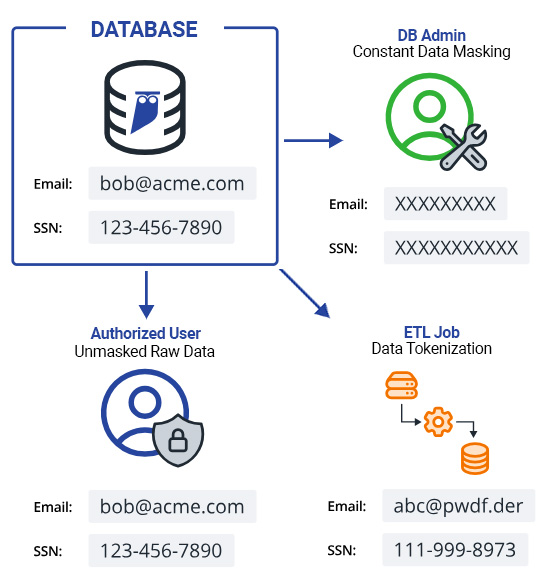
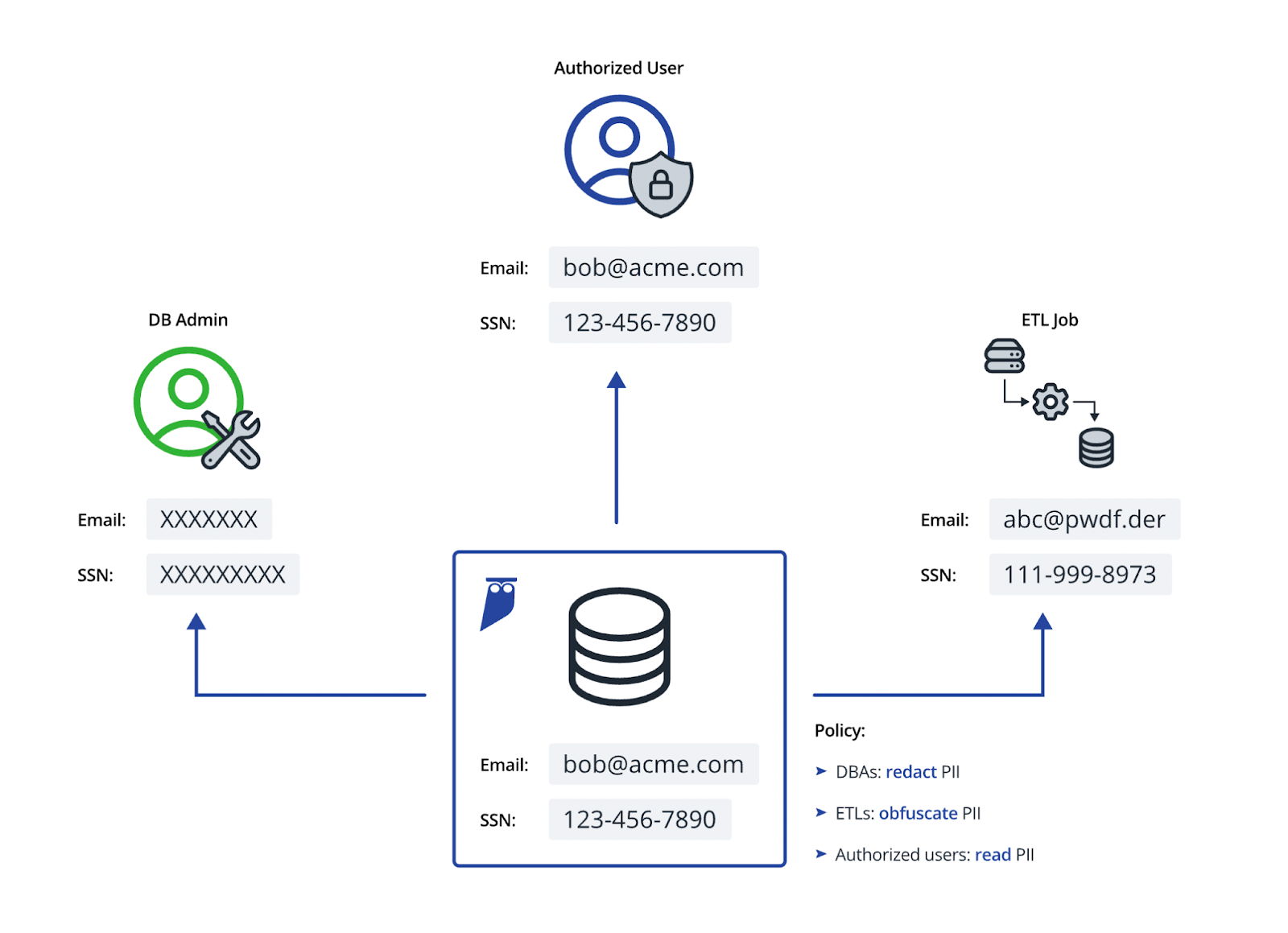
Implementing an effective data masking strategy requires a practical framework that addresses the complexities of different data environments. Here is a structured approach to achieve robust data masking.
Adaptive Strategy:
Adopting an adaptive masking strategy ensures that the appropriate masking techniques are applied based on the type of data asset. For production databases and any replicas, dynamic data masking can be used to mask data in real-time, providing on-the-fly obfuscation without altering the underlying data. For ETL jobs and other data processing tasks, on-the-fly masking can be employed to ensure that data is masked as it is being transferred or processed. This adaptive approach ensures that data is protected in various scenarios while maintaining operational efficiency.
Centralized Policies:
Implementing centralized masking policies across the entire data stack enhances consistency and control. Using an external authorization service to manage these policies decouples policy management from database administration, simplifying oversight and reducing the risk of inconsistencies. Centralized policy management allows for uniform enforcement of masking rules across different databases and applications, ensuring that sensitive data is consistently protected regardless of its location or usage context.
Identity Federation:
Specifying data masking policies in terms of federated identities allows for more precise and context-aware enforcement. Policies can be invoked based on a user’s IAM entitlements, ensuring that masking rules are applied dynamically based on the user’s role and permissions. This approach also involves ensuring that queries from service accounts are annotated with the actual user identity, maintaining the effectiveness of masking policies even in environments where service accounts are used. Identity federation helps in maintaining a fine-grained control over who can see what data.
Automated Coverage:
Ensuring that data masking policies follow the data requires automated and comprehensive coverage. Policies should be specified based on the type of data (e.g., PII) rather than specific fields, allowing them to adapt to changes in data schemas and new data sources. Implementing discovery and classification tools helps in keeping the data labeling updated, ensuring that all sensitive data is identified and appropriately masked. Automated tools can scan databases to detect sensitive information and apply masking policies automatically, reducing the administrative burden and enhancing security.
By following this practical framework, organizations can implement effective data masking strategies that protect sensitive information across various environments and use cases. This approach not only enhances security but also ensures compliance with data privacy regulations and supports efficient data management practices.