Enriched Activity Logs for SIEM Integration
Deep Visibility with User Identity Enrichment
Collect identity-enriched logs and metrics for all activity against your databases, pipelines and data lakes. Get the real-time visibility and actionable context you need using your existing SIEM tools. Speed up troubleshooting and simplify audits.
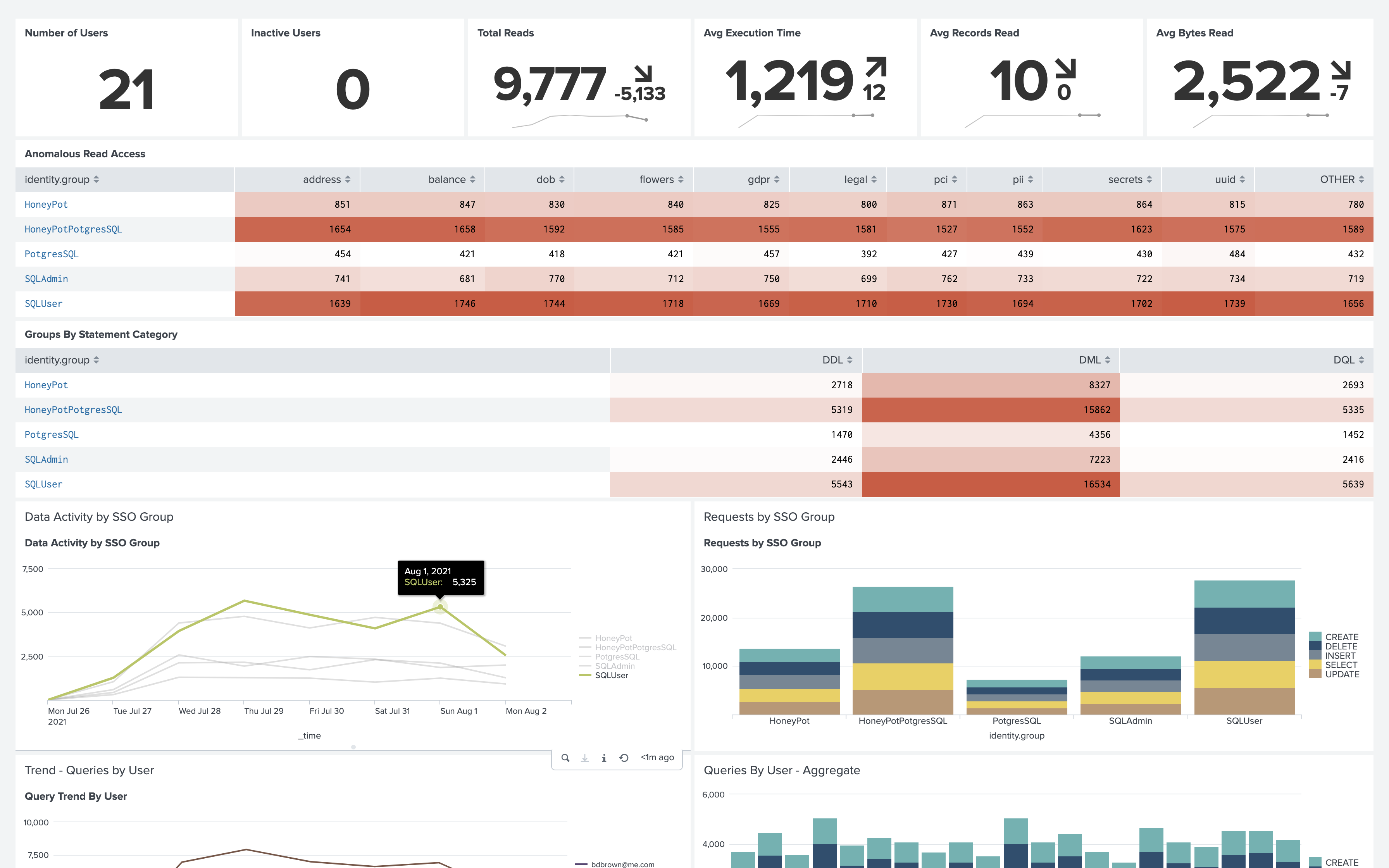
Detect Anomalies Faster
- Gain actionable context including user, SSO group, and query
- Drill into user-specific query activity over time
- See who is reading more data and detect exfiltration
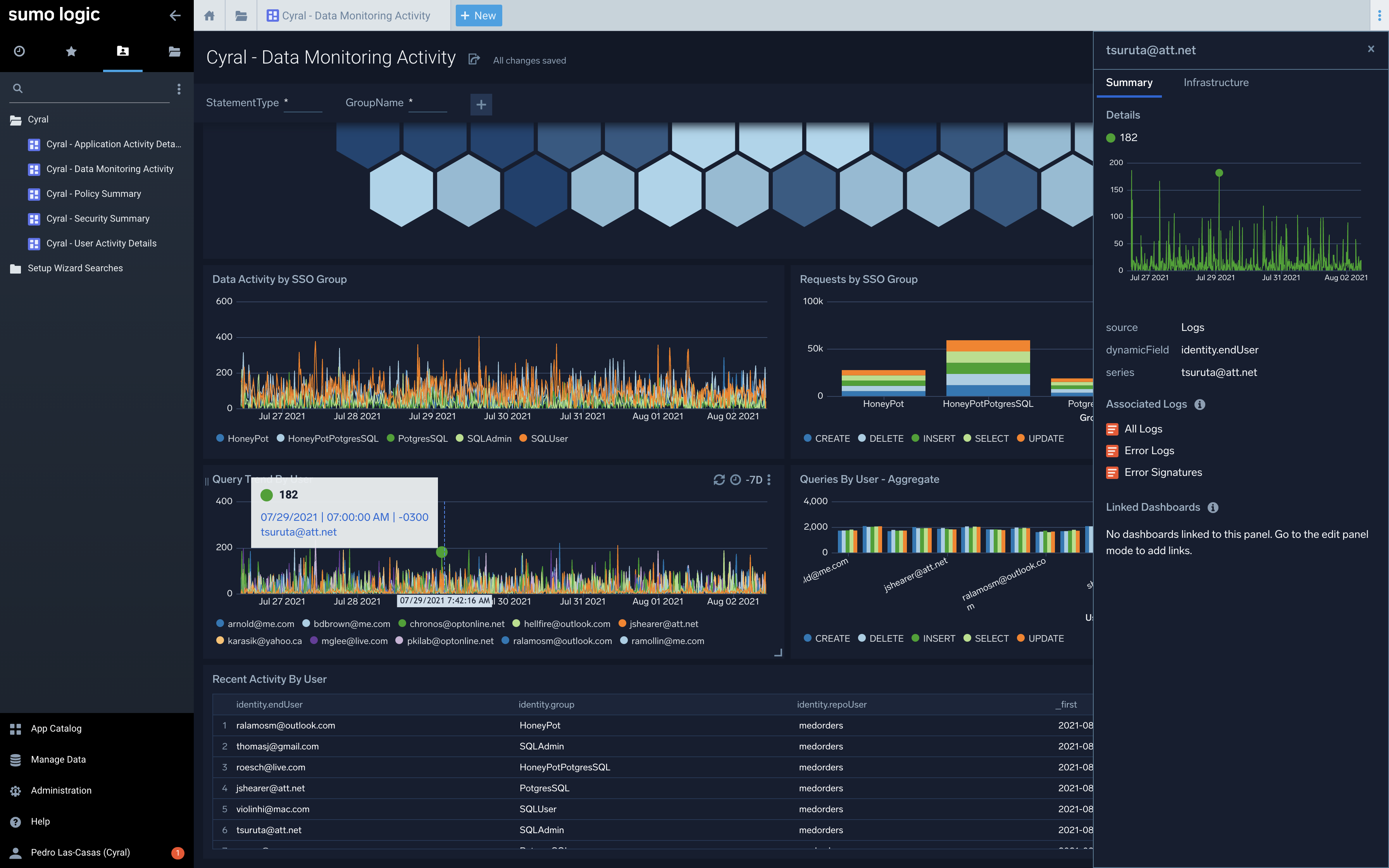
Accelerate Troubleshooting
- Plug metrics directly into your favorite monitoring tool
- Eliminate need to run expensive plans to graph query performance
- Enable teams to trace requests end-to-end
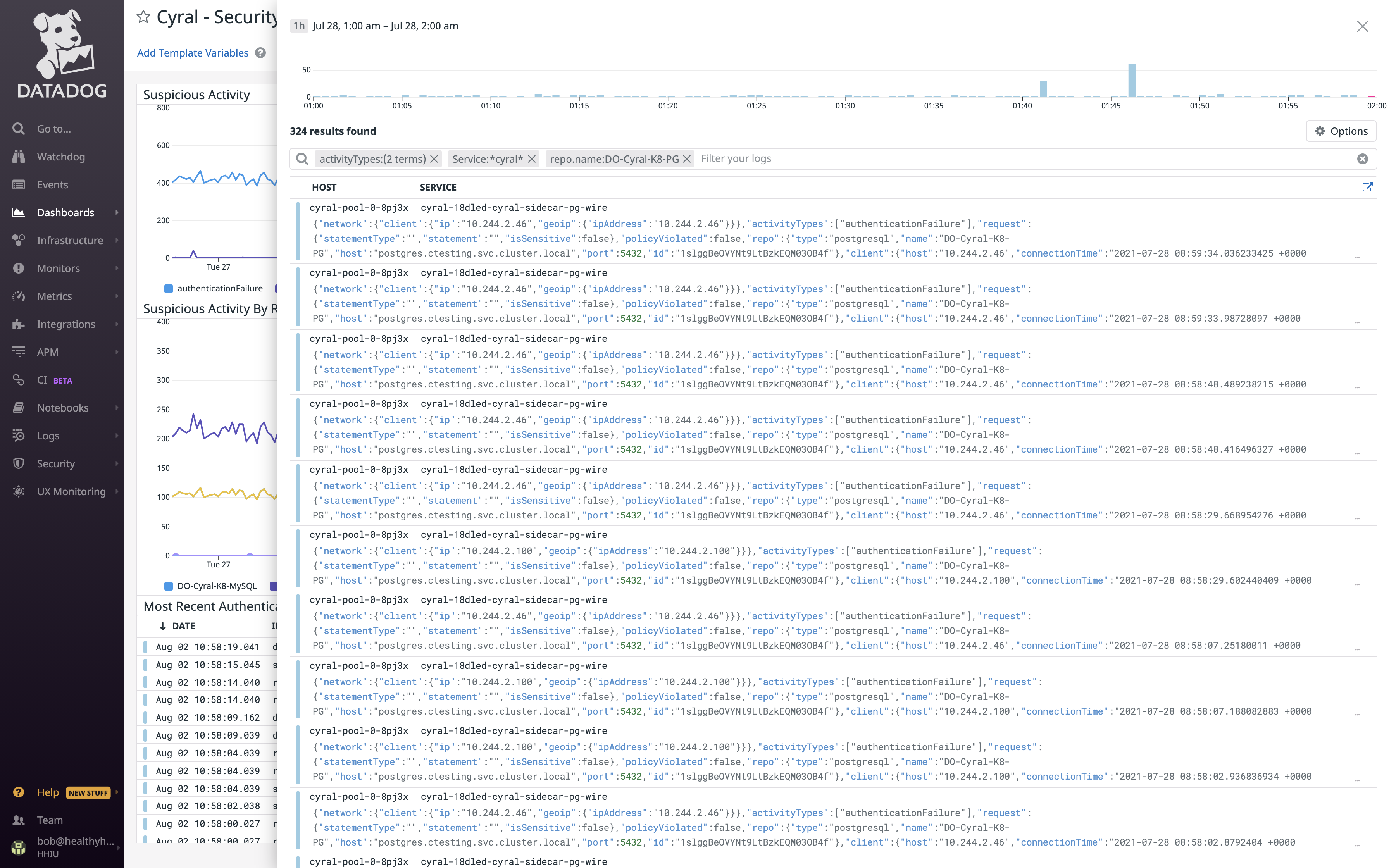
Simplify Auditability
- Eliminate engineering work needed to integrate different query formats
- Drill down all queries by specific user or SSO group to view SQL query rows returned and other context
- Guarantee that logs don’t contain PII or other sensitive information
Eliminate Privilege Creep
- Detect access rights abuse
- Leverage activity information to enforce least privileges
- Identify last-use to enable access recertifications
“Cyral was the missing piece for us in data access governance.”

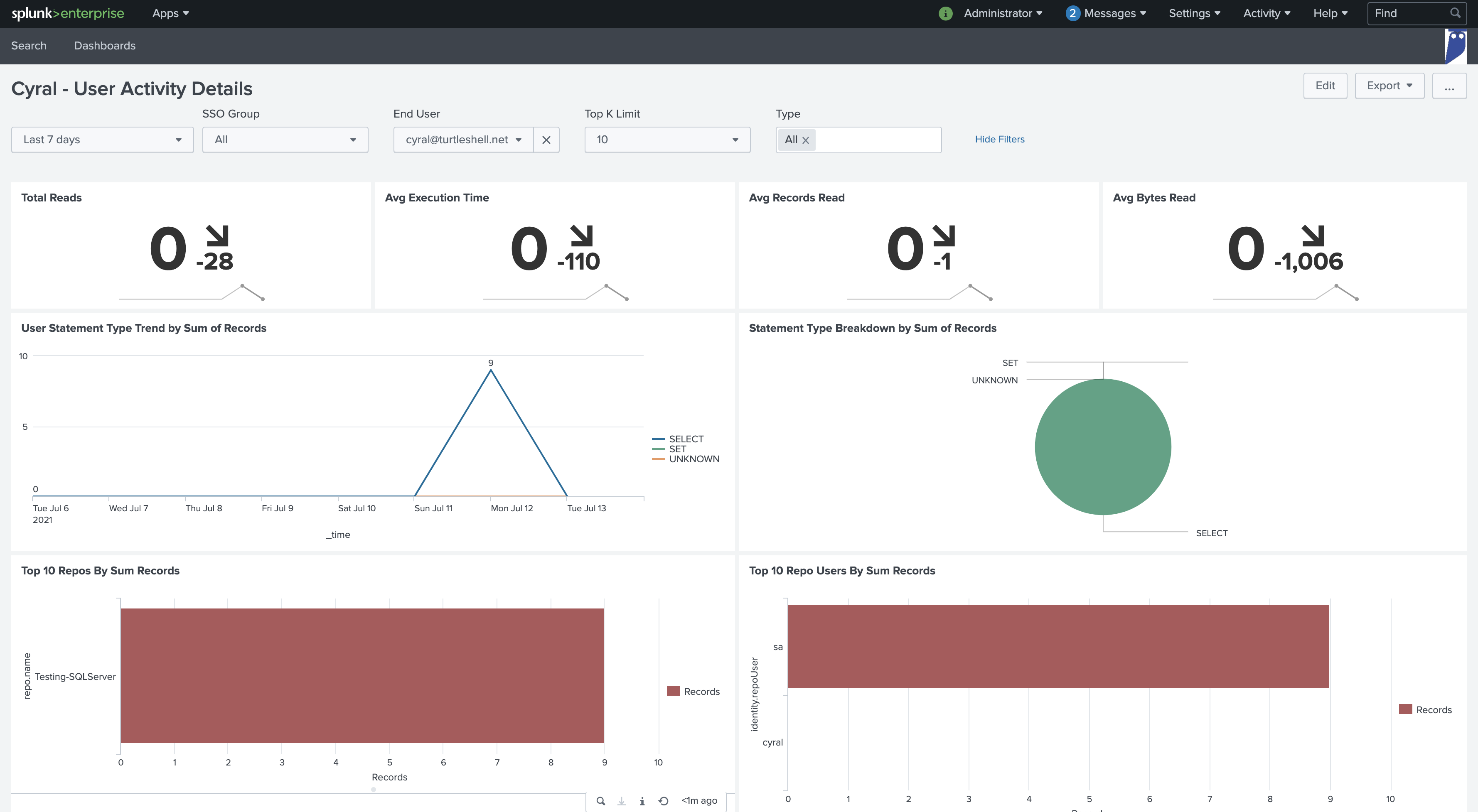
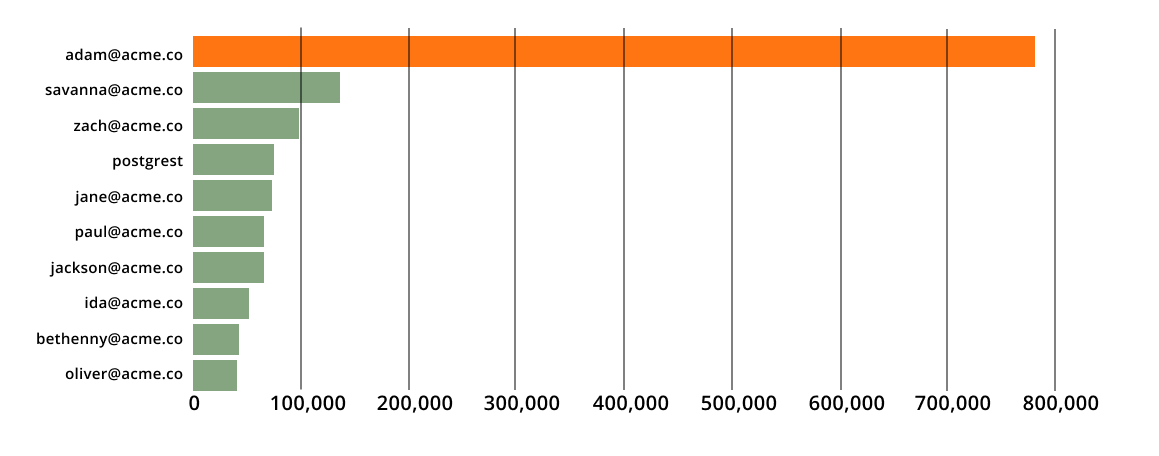
Top 10 End Users by Sum Records
One user consuming more data. Is the account compromised?
Admin Workflow Setup

You will need:
- A Cyral account
- A database
- In the Cyral dashboard, a repository configured to use the database and a SSO provider
- An administrative account in your SIEM (This example uses Splunk)
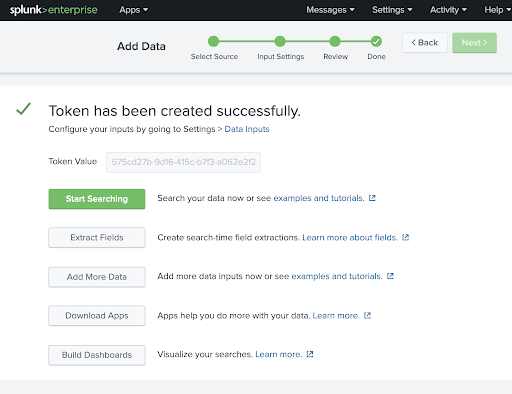
Add a new data source in your SIEM to accept pushed Cyral logs:
- Create an HTTP event collector that accepts JSON data
- Copy the SIEM’s input token and URL
See the docs for SIEM-specific setup.
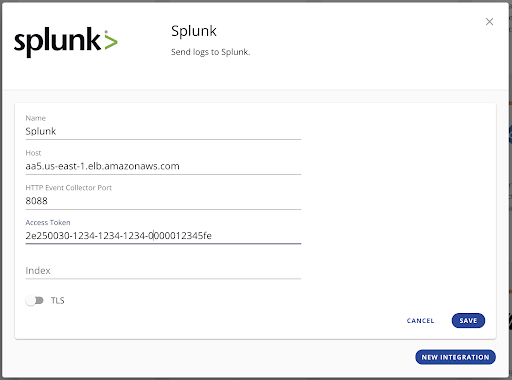
Connect Cyral to your SIEM:
- In the Cyral Portal, choose Integrations, select your SIEM, and click configure
- Enter the URL and token from your SIEM
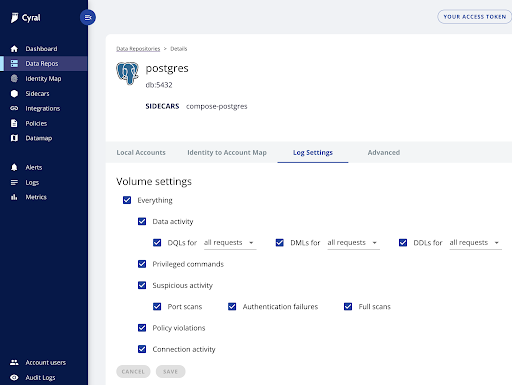
In the Cyral portal, for each database, identify events to log according to your preferences and business goals.

Install pre-built Cyral dashboards:
- Install the Cyral app in your SIEM
- Or contact your friendly Cyral support agent to get the files
Once installed, modify the event types to match Cyral’s JSON schema.
Or create your own dashboards to visualize critical business metrics and user activities.
Either with the Cyral dashboards or your custom dashboards, you can now combine SQL queries and SSO user context to visualize and understand how your data is used to:
- Enumerate and compare SSO user or group query counts
- Filter by application or database
- Aggregate across time to detect trickle exfiltration attacks
- Enumerate policy failures to stop unwanted traffic
- Visualize blocked queries to debug and unblock users’ work
- Configure alerting on critical business metrics
Terminology
Terminology
SIEM
Security Information and Event Management systems enable the collection, transformation and analysis of data activity from various sources to help security teams detect threats, investigate events and pinpoint breaches.
Trickle Data Exfiltration Attack
Unlike a typical data exfiltration attack that seeks to capture all data in a single download, a trickle data exfiltration attack is aware of temporal limits like the maximum rows returned per query or the maximum queries per minute or per hour. The attack limits queries to lots of small batches, exfiltrating large collections of data slowly to stay “under the radar.”
SSO
A Single Sign On (SSO) system uses a separate identity provider (IdP) to validate a user’s identity. Given this external identity (provided usually via SAML or ODIC), the application can make authorization decisions without needing to store a user’s credentials or verify the user’s identity.
IdP
An identity provider (IdP) authenticates a user and provides identity and access tokens for accessing other services. It uses SAML and OIDC protocols to interact with clients and is backed by a directory service storing user information.
Database Activity Monitoring
Database Activity Monitoring (DAM) refers to any solution that is used to actively monitor and analyze database activity. This technology is multipurpose, typically being used by organizations both to fulfill specific compliance criteria, as well as protect their most sensitive data from external hackers and malicious insiders.
Attribute-based Policy
Attribute-based Control Policies implemented by a database system allow a database administrator to specify privileges for certain operations for authenticated users to specific database content.
Get Started with a
Free Trial
Get started in minutes: Explore how Cyral can protect your Data Mesh with our free trial. You can also contact us to see a live demo.

