Policy Engine
Enable field-level access control through rich policies
Dynamically enforce field level authorization policies, based on the attributes of the data set, subject, action type, environment and cardinality. Implement policies as code, enabling security, governance, compliance and protection.
Disallow “customer_portal” service from reading more than 10 emails or addresses at a time, or updating more than 1 address at a time, while running on the “98.0.0.0/12” range of trusted IP addresses.
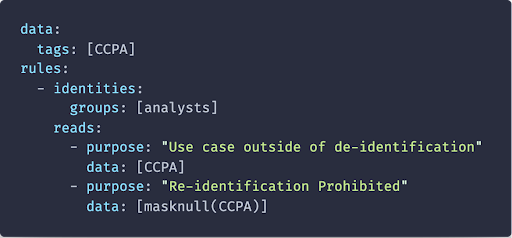
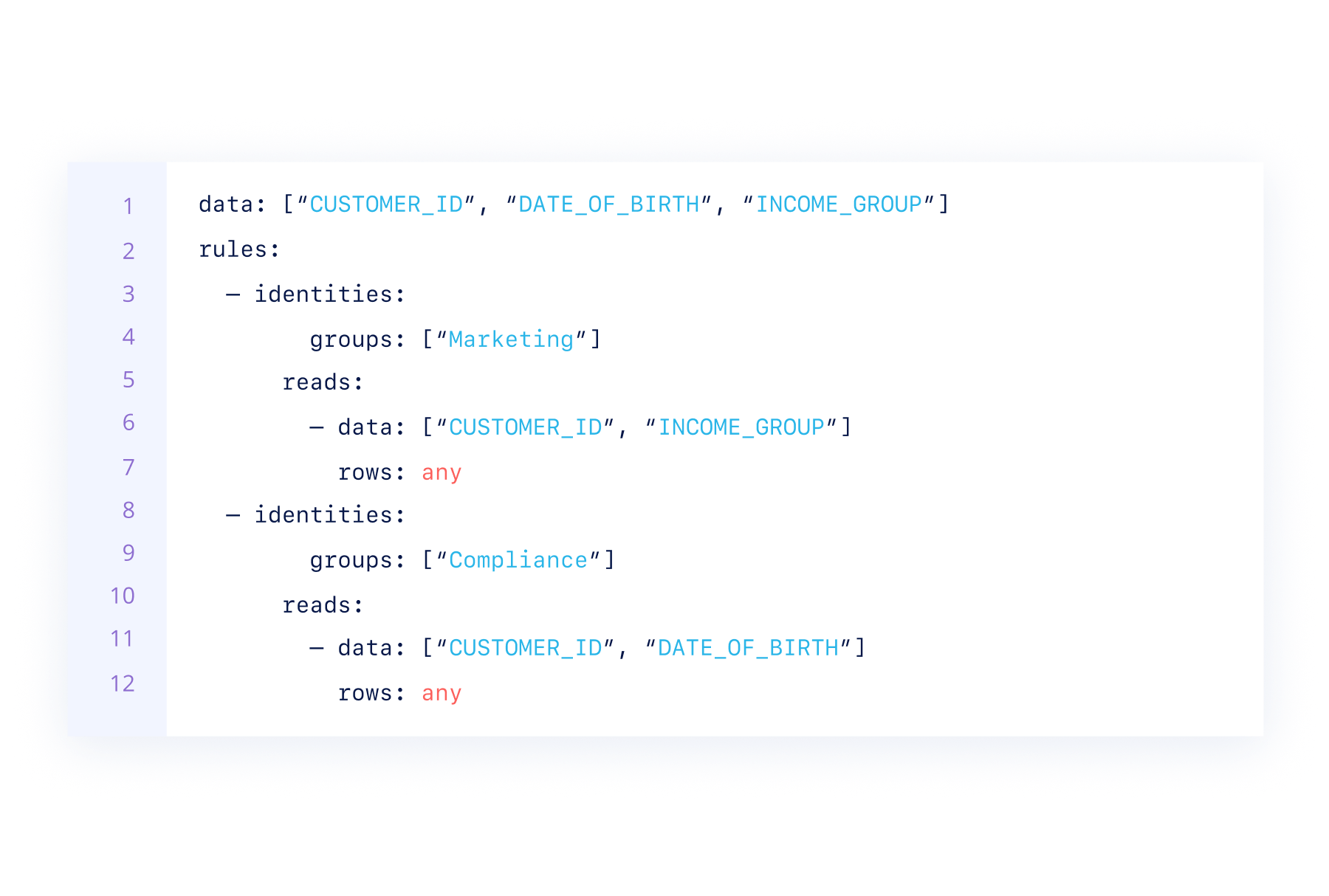
Give anyone in the “Marketing” SSO group read-only access to customer engagement data except dates of birth. Only Compliance team members can see dates of birth.
Ensure a doctor can only see data of their patient in an app by including a constraint on the user identity making the request.
Before

Before
Coarse role-based Access Control policies across individual data repositories. Policies hard-coded in application, kept in sync manually.
- Complicated and error-prone policy management
- Ineffective for users behind service accounts
- Coarse policies that do not capture identities or other attributes
After


After
Granular Attribute-based Access Policies unified across all data endpoints. Service accounts enriched with user identity to make policies effective for apps and tools.
- Centralized and unified policies, managed as code
- Policies enforced even for shared tools and apps
- Fine grained policies, configured on a rich set of attributes
What People are Saying
“At Uplift, data is a key asset and its security is paramount. For us, a security solution must strike the right balance between agility and effectiveness. We needed efficient access controls that allow us to do more with our data while simultaneously eliminating risk and enabling teams to move forward with the greatest speed. With Cyral, we found a solution that does just that.”

Policies as Code
- Keep policies up-to-date with app and infrastructure changes
- Generate audit log of all policy changes and approvals
- Use APIs to easily update data segmentation policies for new applications
Compliance
- Bring your own tags, or ask us to tag data automatically
- Enforce privacy policies by masking data at the field-level
- No data engineering or change to workflows required
Least Privilege
- Strip away any unneeded or overprovisioned privileges
- Reduce the attack surface for attackers
- Implement an “Allow List” for your most sensitive data, limiting the blast radius from hacks
Segregation of Duties
- Ensure admins cannot read data from production databases
- Limit who can update or delete customer engagement data
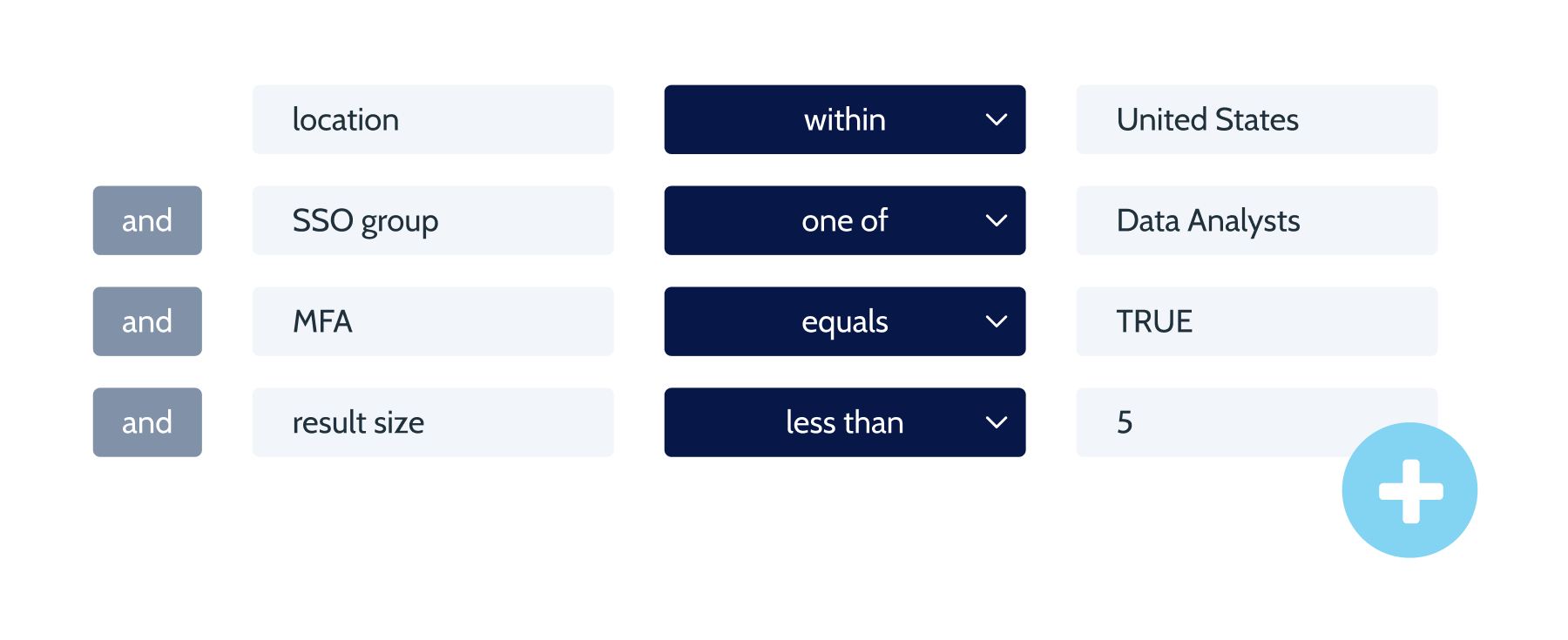
- Enforce regional constraints on analysts so that data never crosses regional boundaries
Data Spillage Prevention
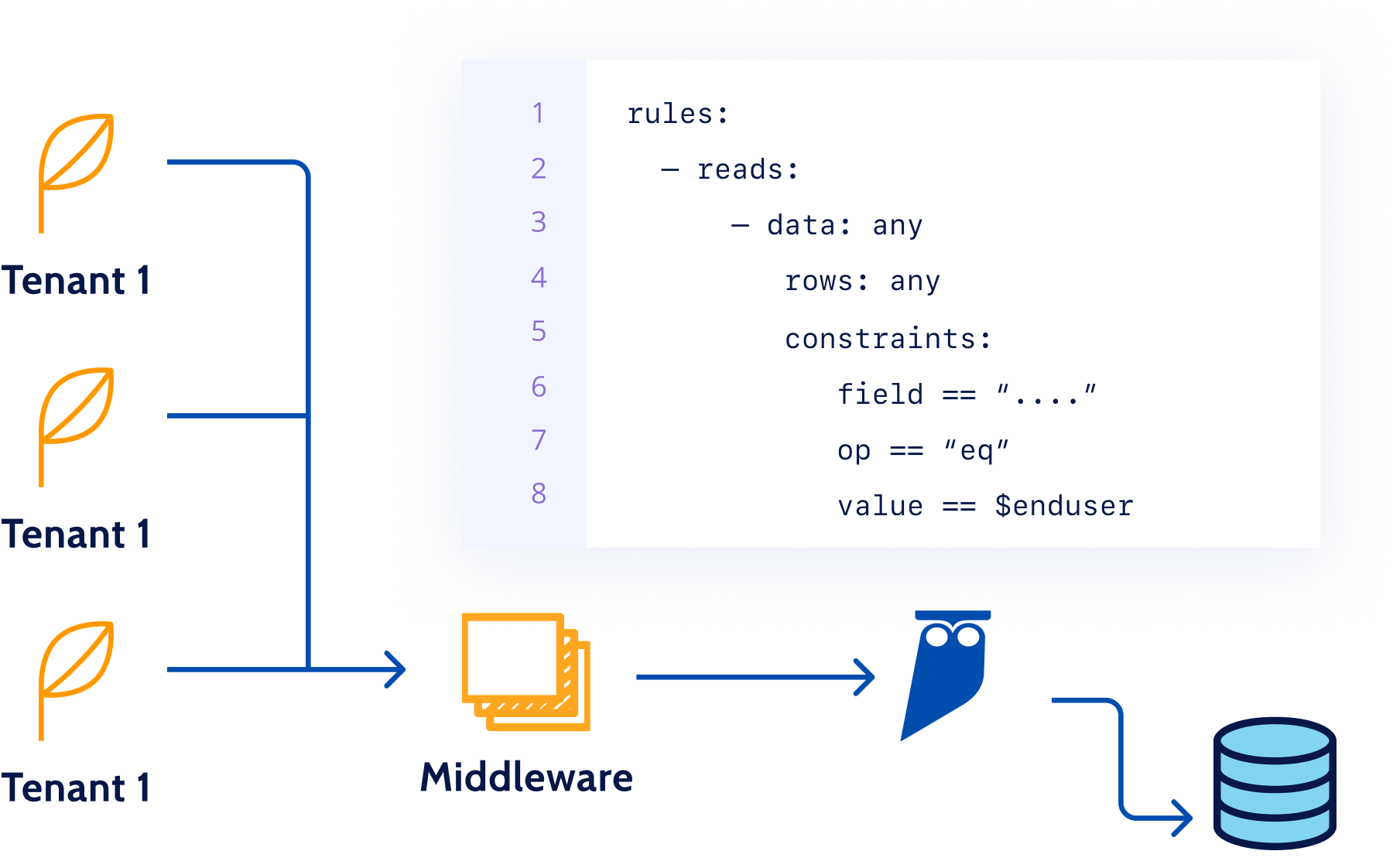
Database is always a shared resource for application tenants, which use a shared service account to access data. Cyral helps protect against logical errors by preventing data spillage from one tenant of an application to another. Cyral’s ability to disambiguate users behind the various tools and applications means the policies get applied uniformly and without exception.
Integrations
Terminology
Terminology
Rest API Client
A REST API client is used to execute REST APIs either from the command line or using a UI.
Version Control Service
A version control service hosts source code repositories (predominantly git-based) and provides services for code review, collaboration and versioning of policies.
IaC Tool
An infrastructure as code tool makes it possible to manage (create, update, delete) infrastructure (compute, storage, network, load balancers, etc.) as well as configuration data (init files, environment variables, policies, etc.) using a declarative model, and allows DevOps teams to use the same versioning and collaboration tools for their infrastructure and configuration as for their source code.
Identity Providers
An identity provider authenticates a user and provides information about the user’s device, location, SSO group, department, and any other attributes that are available in the corporate directory.
Incident Response
An Incident Response system helps an organization with the process of handling security events for alerting, diagnosis, forensics and remediation, and provides information about the on-call schedules of SRE and support staff members.
Get Started with a
Free Trial
Get started in minutes: Explore how Cyral can protect your Data Mesh with our free trial. You can also contact us to see a live demo.



