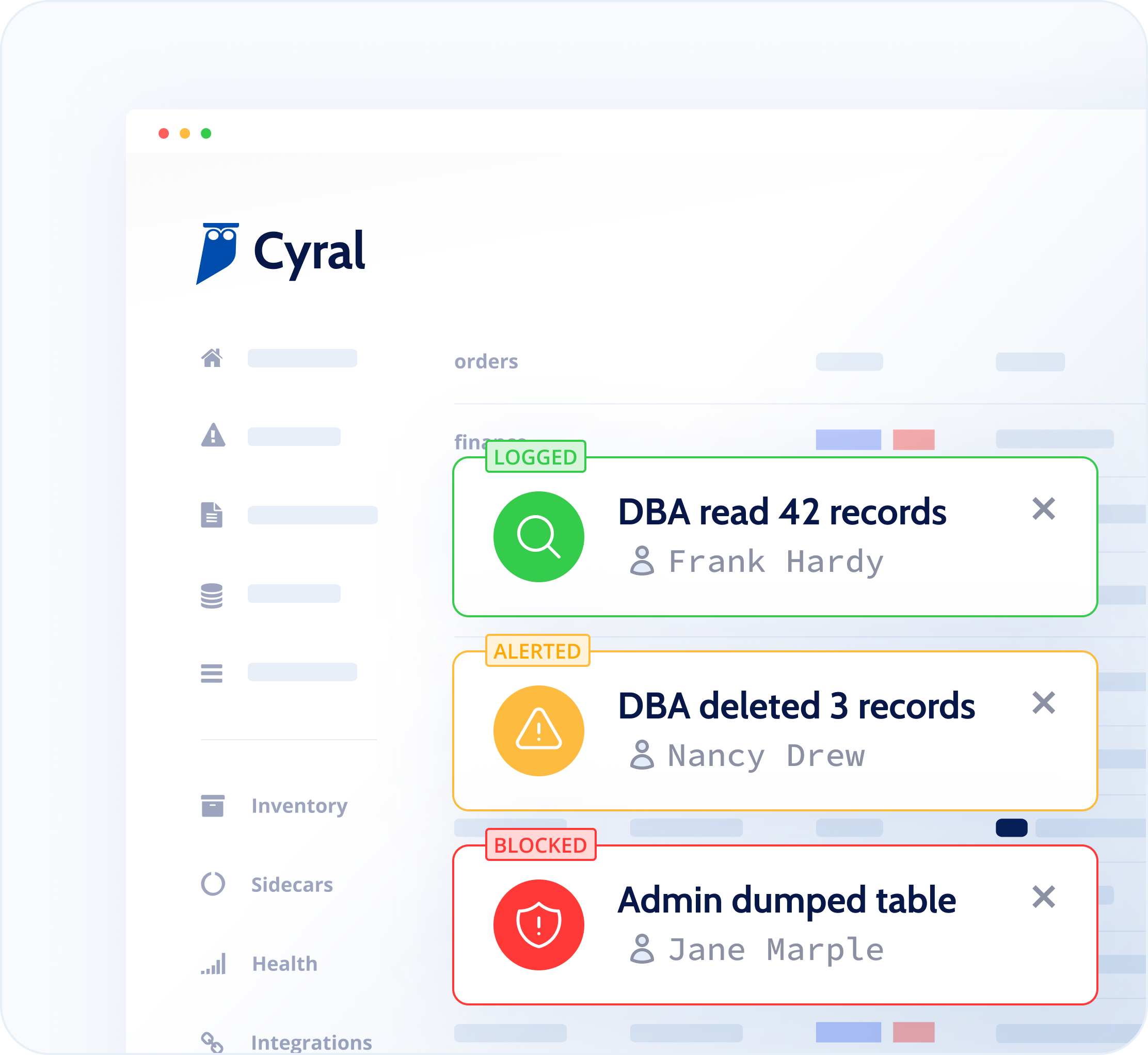
Solving the #1 Data Security Challenge: Shadow Access
Cyral eliminates unmonitored, unauthorized or over-privileged activity in your data stack.
Database Activity Monitoring with no blind spots
Data Security Posture Management with access control
Data Access Governance for all users
“With Cyral we can easily federate the identity of data consumers, including shadow users, to the company’s central IAM services.”
Head of Cloud Security, Informatica
“Cyral was the missing piece for us in access governance. It helps us tell a clear story of why a piece of data is protected, who accessed it, how they authenticated and what queries they ran.”
CEO, Human Interest
“We needed controls to make sure people only see the data that is appropriate for their use case and their job. This is what Cyral helps us with, in creating and enforcing policies that block access to data you’re not supposed to see.”
CISO, Cedar
Data Security that Works
Identity Federation
Integrate with central IAM services to eliminate shadow access
Data Security Contracts
Eliminate manual permissions management, deploy policies as code
Complete Visibility
Real-time visibility into all data activity, enriched with user identity
Use Cases for Cyral
-
No impact to performance and availability
-
Enriched user and session information
-
Enforce policies, instead of just alerting
-
Consistent implementation for cloud & on-prem
-
Enforce policies across apps and BI tools users
-
Protect data from malicious or accidental corruption
-
Eliminate the need to manage custom VIEWs
-
Provide field-level audit trail for compliance
-
Standardize data security for cloud & on-prem
-
Expand security posture to applications and tools
-
Automate privilege management with data security contracts
-
Eliminate the need for manual remediation
-
Secure internet-facing database endpoints
-
Restrict privileged access from trusted locations
-
Eliminate the expense and complexity of VPN clients
-
Enables teams to safely use SaaS based BI tools

“We use Cyral to seamlessly extend Active Directory-based authentication to our production databases. This helps implement data access governance and eliminate shadow access.”
CIO, Belcorp

“We use Cyral for data access governance for our data visualization tool. Our experience with Cyral team and the product has been incredible. The product was easy to set up and the sophistication was beyond our expectation.”

