The Data Security Governance Platform
Automate discovery, access management, authorization, and assurance for all your structured data.
Trusted by leading security experts at:
Data Security Governance for the Modern Data Stack
Cyral provides
Data Activity Monitoring
Governance
Discovery
Micro-segmentation
Zero trust
Compliance
for
Azure Database
PostgreSQL
GCP CloudSQL
AWS RDS
MySQL
Galera
Azure SQL
MongoDB Atlas
AWS Aurora
AWS DynamoDB
MariaDB
AWS Redshift
SQL Server
Snowflake
MongoDB
Oracle
AWS S3
Continuously scan all your databases to discover all database accounts, their permissions, and any sensitive data that may be accessible to them.
Discover data within your environments, identify sensitive datasets, and apply field-level access controls to protect the data.
Restrict access to database accounts to known, authorized IP addresses. Easily specify policies for both users and applications.
Extend your enterprise single sign-on (SSO) platform to your databases. Grant access based on a user’s group memberships in the SSO platform.
Require multi-factor authentication (MFA) for database access. Add an access condition to require users to complete Duo authentication each time they access the repository.
Grant approval-based access and Just-in-Time (JIT) access to databases.
Simplify password rotation for accounts used by apps, and uncover the identities behind the apps and BI tools connected to a database.
Mask the results of queries to protect information and comply with privacy regulations.
Enforce data governance with row-level filtering policies across all databases, pipelines, and BI tools.
Limit the number of data objects a user is allowed to read, update, or delete within a given period of time.
Field-level visibility enriched with identity information for all users, tools, and applications, which can be used for monitoring, auditing, and forensics.
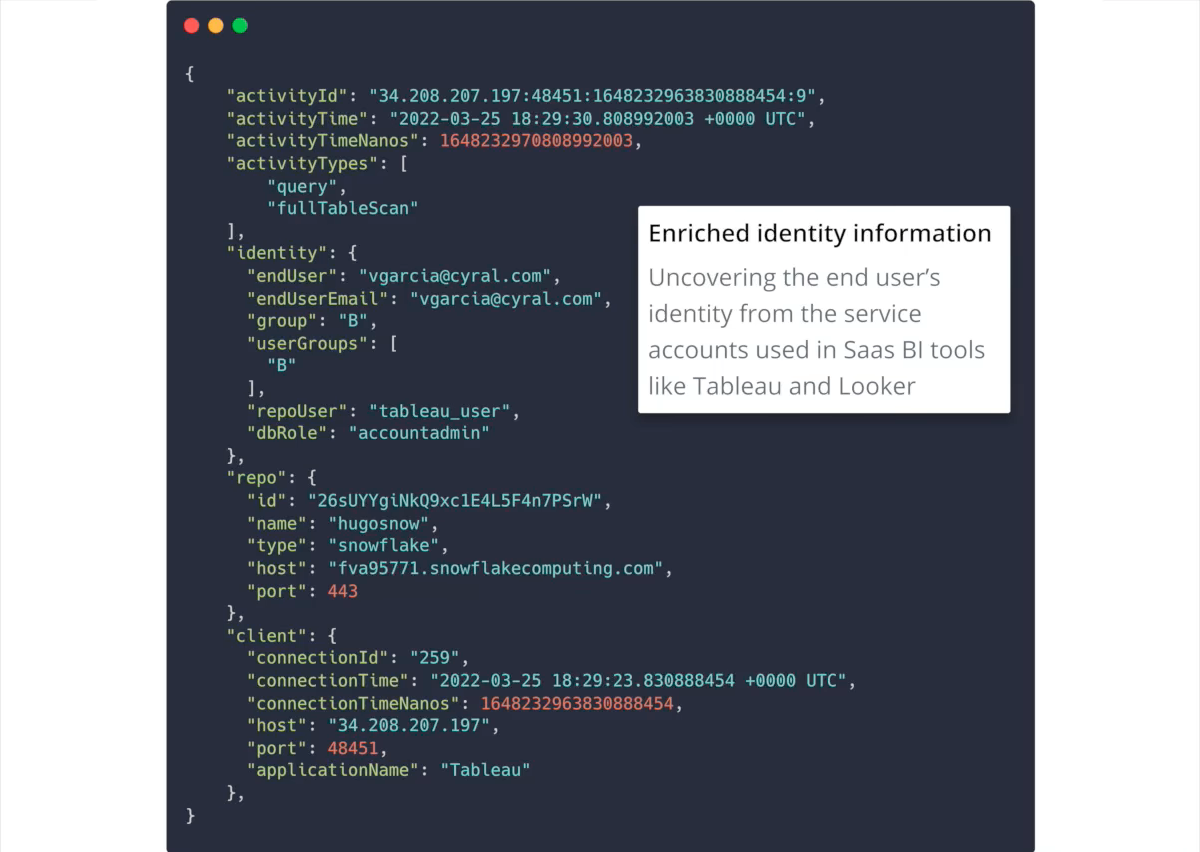
Uncover the identity of users of the tools and applications. Streamline audits, access control, and forensics.
Collect identity-enriched logs and metrics for all activity against your databases. Get the real-time visibility and actionable context to speed up troubleshooting and simplify audits.
Integrate Data Security Governance With Your Data Stack

What People are Saying
“Anything that affects throughput matters to our business and what we like about Cyral is that it’s lightweight and runs in parallel with the data traffic, with no impact on performance.”


