Database Access Management Made Simple
Configure access management for your database in 30 minutes.
Modern, fine-grained database access management
Cyral provides a modern database access management solution, designed to seamlessly integrate with your existing tools, infrastructure, and processes. From real-time database activity monitoring to just-in-time access management, Cyral’s capabilities are engineered to enable teams to easily meet compliance standards while ensuring operational efficiency.
Infrastructure Agnostic
Flexible deployment, compatible with both on-premises and cloud environments
Seamless
Easily clicks with all your tools with no changes to your applications
Fully Automated
Automated policy management and dynamic scaling enabled by an API-first platform
One Platform for All
Database Access Management Needs
Session Recording and Audit Logs
- Comprehensive activity logs simplify compliance with regulations such as PCI, SOX, HIPAA, and more.
- Identify suspicious activity and prevent unauthorized data access in real-time.
SSO and MFA for Databases
- Seamless access management based on zero trust principles and federated identity.
- SSO and MFA secure and simplify access to databases.
Just-in-time Access Management
- Use just-in-time access to minimize long term privileged access and reduce attack surface.
- Manage approvals using existing ChatOps and ITSM tools.
Data Obfuscation and Masking
- Data masking and obfuscation capabilities simplify compliance with GDPR, CCPA, and other privacy regulations
- Ensure PII and customer data is handled safely without disrupting business processes.
What People are Saying
“Anything that affects throughput matters to our business and what we like about Cyral is that it’s lightweight and runs in parallel with the data traffic, with no impact on performance.”
Cyral’s Data Security Governance Platform
Cyral’s platform is engineered to meet the complex demands of today’s data ecosystems. To enable effective data security governance programs, Cyral’s capabilities are built upon four pillars: Data Layer Abstraction, Identity Federation, Attribute-Based Access Control (ABAC) for least privilege, and Modern GRC controls.
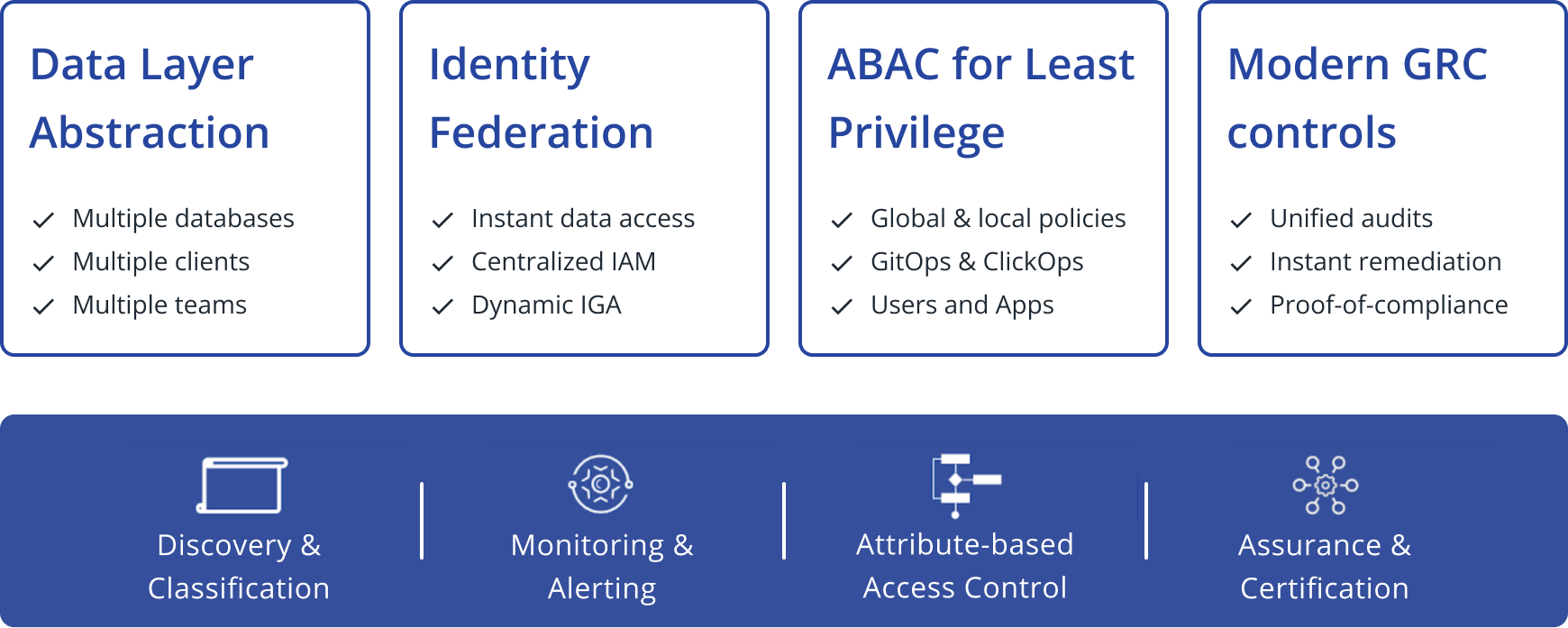
Data Layer Abstraction
Cyral offers a layer of abstraction over your data assets, enabling simple access control across diverse data stores, be it SQL, NoSQL, or hybrid setups. This abstraction eliminates the need to write different access control policies for each database, simplifying your workflow and making data access management more efficient.
Identity Federation
Our platform integrates with your existing Identity and Access Management (IAM) systems. This means you can centralize and reuse your existing entitlements, making access management less cumbersome and more secure. Furthermore, allowing data users to access databases using credentials they’re familiar with alleviates them of the burden of tracking various sets of database credentials.
ABAC for Least Privilege
Cyral enables teams to maintain powerful policies leveraging Attribute-Based Access Control (ABAC) to ensure the principle of Least Privilege. By using various attributes collected both at the time of connection and the moment the request is made, our platform enables fine-grained access policies that not only meet but exceed industry standards for database protection.
Modern GRC Controls
Navigating the intricate web of Governance, Risk, and Compliance (GRC) is simplified with Cyral. Our platform comes equipped with modern GRC controls that enable you to generate comprehensive reports on data access, user activity, and security incidents. This removes the need for database access reviews, simplifies compliance reporting, and demonstrates a strong governance
program to auditors and stakeholders.
Built upon these four pillars, Cyral’s platform represents a true end-to-end database security governance platform.




