NSO’s Pegasus is in the spotlight after many, many reports. Update your Apple devices for the 12th and 13th zero days. Read more on SIM swapping, and Kaseya. A new study points to a way for spotted owls and finally a proof of concept project using OPA and cosign to sign and verify images.
- If you haven’t been keeping up with all of the NSO’s Pegasus spyware news and the back and forth, The Verge has a great rundown of what is known at this point with a ton of links. If you’re concerned about your phone, Amnesty International has released MVT on GitHub to search for it.
- Keep updating your Mac’s and iPhones as Apple has patched actively exploited vulnerabilities in both culminating in the 13th zero day patched this year alone via Security Week.
- One of the people allegedly involved with the massive Twitter hack and many other SIM swapping extortions primarily for unique social media handles has been indicted. Read more at KrebsOnSecurity
- John Hammond at Huntress digs into the Kaseya ransomware attack and asks why wasn’t it worse?
- Finally, ethically concerning Clearview AI raised $30 million and “that new investors have asked not to be publicly identified” via Yahoo News.
Owl fun and facts:

The spotted owl is back in the news as a 17 year study was recently released that showed the best chance of survival for the spotted owl was to remove the invasive barred owl originally found on the East Coast. Read more at OSU news.
A Shout Out:
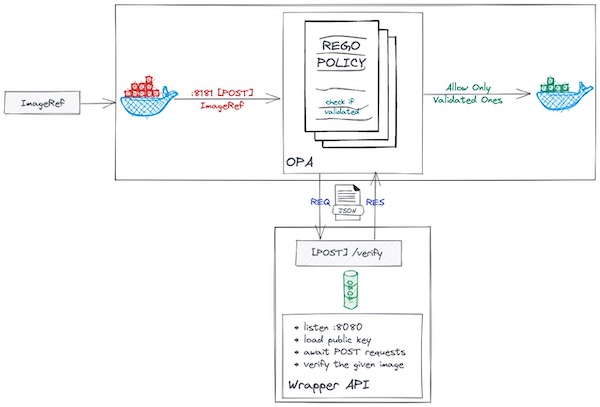
This is another really interesting use case of policy as code to sign and verify images using 2 major CNCF projects.
“This project is just a proof-of-concept project that shows people how they can use cosign and OPA (Open Policy Agent) together to implement the signing and verifying container image process together.
In most basic form, cosign is a container signing tool; it helps us to sign and verify container images by using the signature algorithm (ECDSA-P256) and payload format”
Read more about the project on GitHub
About:
TSD began as an internal newsletter that our Security Lead, Daniel Tobin, would circulate to the team each Tuesday. It proved to be a great resource for all of us so we thought, why not share it with all of you? Our hope is that it helps make you just a bit more secure.
Check back here every Tuesday for more TSD or sign up below to stay in the loop!
Please reach out to us directly, via security@cyral.com or on Twitter at @dant24 if you have any questions, concerns, tips or anything else!
That’s owl for now!


