Hello and welcome to TSD, your weekly blog post with top of mind security issues. TSD began as an internal newsletter that our Security Lead, Daniel Tobin, would circulate to the team each Tuesday. It proved to be a great resource for all of us so we thought, why not share it with all of you? Our hope is that it helps make you just a bit more secure.
Check back here every Tuesday for more TSD or sign up below to stay in the loop!
Please reach out to us directly, via security@cyral.com or on Twitter at @dant24 if you have any questions, concerns, tips or anything else!
- Following up on the Zerologon vulnerability from last week: turns out not everyone has patched as Microsoft has publicly warned that they are seeing active attacks via KrebsOnSecurity.
- Alien is one of the most advanced pieces of malware yet for Android phones. It is based on previously leaked source for another piece of malware known as Cerberus. Both have been deployed via a Malware as a Service (MaaS) model. (Everything as a service!) The malware was analyzed by ThreatFabric and they found that it can steal credentials from 226 applications, sniff 2 factor codes and much much more. Luckily they found that it is very rarely distributed by app stores and usually requires users to click through extra security screens. Read more about it on ZDNet.
- It’s been a busy week in healthcare. Ransomware accidentally hit a hospital in Germany which meant a woman had to go farther to a different hospital and subsequently died via ZDNet. The police later reached out to the ransomware gang who sent decryption keys for the hospital. On a separate note, this week Universal Health Services, one of the largest US providers, was hit by ransomware reportedly related to Ryuk. Reports are coming in that it started Saturday and patients are being turned away or asked to go to different facilities. Read more at ZDNet. Way back in TSD-02, we mentioned that some ransomware operators put out press releases stating that they would not attack hospitals, the operators of Ryuk were not one of those.
- Town Sports International, operator of New York / Philadelphia / Boston Washington Sports Clubs, Lucille Roberts and more left a server unsecured on the Internet for almost a year which contained nearly a terabyte of spreadsheets on 600,000+ members until they were alerted by researchers. Number 1 rule for securing your data, know what assets you own at all times. Read more at TechCrunch.
- The Cybersecurity and Infrastructure Security Agency (CISA) published an in depth report on a federal agency’s enterprise network using the MITRE ATT&CK framework. They detail everything from initial access through to command and control. This a great primer on how you could use the framework. Read the full report at CISA.
- The Government Accountability Office (GAO) released a report faulting the current administration for cybersecurity. The title, “Clarity of Leadership Urgently Needed to Fully Implement the National Strategy” covers the major points. They point to a lack of direction with leadership being scattered among many different areas of government. This is not terribly surprising as the current administrations removed the White House cybersecurity coordinator in 2018. This follows a bipartisan congressional committee called Solarium Commission releasing a similar report in March of this year. Read more at The Hill.
- In the ongoing “security” saga related to TikTok, a judge granted a temporary restraining order against the latest ban by the Trump administration. Therefore, you can still continue to download it from app stores. The judge unsealed the documents which revealed that they believed the administration over stepped legal boundaries. Read more at Axios. Meanwhile CNET looks into recent filings and finds that all of the information on why TikTok is dangerous is [REDACTED]. As for WeChat, the administration asked that ban be put into place immediately on Friday via AP.
Owl fun and facts:

“A medium-sized, chocolate brown owl with dark eyes, the northern spotted owl is a nocturnal “perch-and-pounce” predator that captures its prey (primarily small forest mammals) with its claws…Parental care of the juveniles generally lasts into September when the young owls finally take off on their own…The spotted owl’s first critical habitat designation came in 1992 and was revised in 2008. A new final rule designating critical habitat was published in December 2012″ from the Oregon Fish and Wildlife Office of the US Fish and Wildlife Service. The “same” US Fish and Wildlife Service is also seeking comments on a proposal to reduce the critical habitat by over 200,000 acres. Read more about the proposal at KOIN. Leave your comments on the proposal here.
A Shout Out:
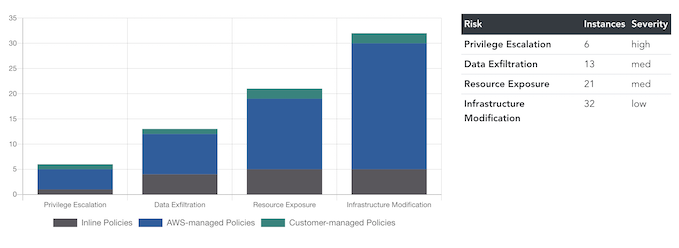
We’re big fans of Security as Code, so super excited to the v0.2.0 of Salesforce’s Cloudsplaining with a major UI uplift and refactor.
“Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report.”
Check out Cloudsplaining on GitHub.
That’s owl for now!


