Hello and welcome to TSD, your regular blog post with top of mind security issues! TSD began as an internal newsletter that our Security Lead, Daniel Tobin, would circulate to the team each Tuesday. It proved to be a great resource for all of us so we thought, why not share it with all of you? Our hope is that it helps make you just a bit more secure.
Check back here every Tuesday for more TSD or sign up below to stay in the loop!
Hi Cyraloons and welcome to another week of TSD, your regular email / blog post with top of mind security issues, a few security tips for both work and home and at least 1 fun thing related to owls.
Please reach out to us directly, via security@cyral.com or on twitter at @dant24 if you have any questions, concerns, tips or anything else!
- Zoom is everywhere now. Zoom is everywhere because it is convenient and easy to use. They increased their usage from 10 million participants in February to over 200 million in March. With all of those added users, an immense amount of scrutiny came and as with all software with this level of scrutiny, many bugs were found. Zoom is still one of, if not the best, for schools, exercise classes and most likely your business as well. Zoom was not yet designed for use by high profile targets protecting against nation state attacks. Zoom will need to take additional steps to increase their end-to-end encryption as outlined here. They have since taken all of that feedback and been incredibly responsive and released fixes and a blog post to help you secure your meetings if you need help in doing so.
- If you are using Zoom, read Zoom’s blog post on how to secure your meetings including to password protect your meetings, make sure you update to the latest version and do not screenshot and share your calls with the meeting ID in them especially if you’re a prime minister. Read the full statement on the steps they have already taken and their focus on security and transparency going forward here.
- Up to 5.2 million Marriott Bonvoy program members may have had their personal information stolen. If you were affected you should have already received an email and had your password automatically changed. Marriott was hacked in 2018 as well resulting in a much more serious leak of personal information that included sensitive information of over 500 million guests who had stayed at Starwood resorts. More info at Wired.
- Since we’ve been mentioning ways to secure home networks, this post about how Caleb Sima did so is a good read. Caleb’s suggestions are also great if you want to level up your own startup network as well and may align closer to your budget there than at home. He does offer some open source options if you have the desire to hack some things together.
Owl fun and facts:
Although owls are great hunters, they have rarely been used in falconry. Many other birds are much quicker to train and are used to hunting during the day. The Eurasian eagle owl and the great horned owl have both been successfully trained in the past though.

A Shout Out:
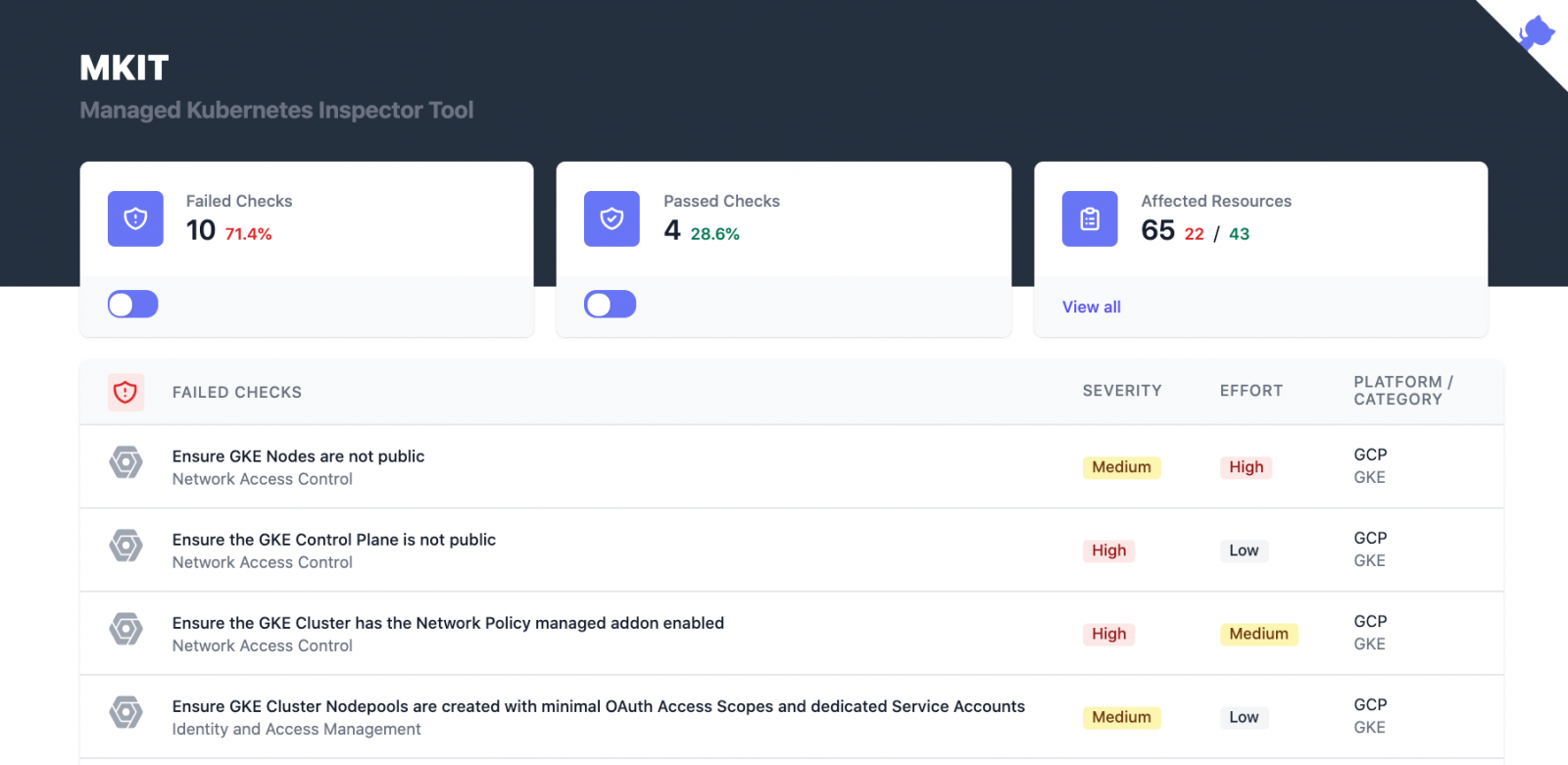
Darkbit.io has released MKIT, Managed Kubernetes Inspection Tool, to help you perform baseline assessments of your Kubernetes deployments. It has built in assessments of Amazon Elastic Kubernetes Service (EKS), Google Kubernetes Engine (GKE), Azure Kubernetes Service (AKS) and plain K8s. This tool is incredibly simple to run, and you should be able to perform an assessment on your infrastructure in a matter of minutes. You may have seen one of the cofounders of Darkbit.io, Brad Geesaman present with Ian Coldwater at RSA about using Kuberenetes as a command and control across multiple clusters. If not, check out their talk here.
That’s owl for now!


