At Cyral, we work with clients using the entire spectrum of cloud architectures: every database, data warehouse, and cloud provider you can think of. We’re also fanatical about making sure our product fits seamlessly into our clients’ existing infrastructure and workflows—it’s a core principle in what we do.
As such, it was important to us that we also embrace a multi-cloud strategy for our product. While we initially started developing our platform on another web service provider, we quickly initiated our foray into Google Cloud Platform (GCP), not only to keep building out the product but also to make sure we could best support the new customers we were bringing on who were already using GCP.
In our journey to monitor and secure GCP, we evaluated Forseti Security to automate security testing across our GCP footprint. We wanted to make sure that our projects were already secure by default and if not, notify us if they deviated from our high standards. Today, we wanted to share a bit more about what we learned using Forseti that we thought might be helpful to anyone else looking to secure GCP.
When we began with Forseti, we were floored by thoroughness of the potential configuration options. As of version 2.2, there were 139 inputs that could be configured. This sheer amount of options was both exciting and overwhelming at the same time. For the most part, there are sensible defaults, but as we went through, we distilled it down to a manageable set to get started with for a smaller deployment.
Forseti provides you with a multitude of options to choose how to deploy.
- Using a Cloud Shell walk through for Google Compute Engine (GCE)
- Deploying GCE with Terraform
- Using Helm to deploy on an existing Google Kubernetes Engine (GKE) cluster
- Using Terraform to deploy to GKE
At Cyral, everything is built using the Infrastructure as Code (IaC) model and wanted to take advantage of one of the key features of GCP, Google Kubernetes Engine.
Prerequisites
- To get started with our approach, you’ll need to make sure you have Terraform version 0.12 which can be downloaded from the Terraform website.
- You’ll also need to download and install gsutil. (Google’s Cloud Storage CLI tool)
- You’ll need GCP Org Admin privileges to be able to create the required service account.
- You’ll also need to get your GCP Org ID. Save this as you’ll need it in the next few steps.
- Finally, you’ll want to create a new GCP project dedicated to Forseti. Follow the instructions here to create your project. Take note of the Project ID that is created. For example, if you create a project named Forseti, the Project ID will be similar to
forseti-123123
Creating a Service Account
Instead of using your own credentials, it is a best practice to create a service account that Terraform will use to deploy and configure resources. This will be automatically setup by running the following commands.
Note: the current directions say to clone the branch modulerelease521, however, Google has since deprecated the version of Kubernetes it will try to use. Modulerelease521 points to 1.14.10-gke.17 while master at cf59de4 has been updated to use 1.15.11-gke.9. If you need to edit this in the future, simply edit this line in examples/on_gke_end_to_end/variables.tf
gcloud auth login
git clone https://github.com/forseti-security/terraform-google-forseti.git
cd terraform-google-forseti
. ./helpers/setup.sh -p PROJECT_ID -o ORG_ID -kIf the operation is successful, it will create a new service account called cloud-foundation-forseti-XXXX, assign it the necessary permissions, download credentials.json and show a screen similar to the below:
Deploy Forseti on GKE Using Terraform
While still in your local terraform-google-forseti directory, run the following commands:
mkdir gke-cluster
vi main.tfFor a new GKE cluster, you’ll want to create a main.tf file with the following variables:
source: This is the terraform definition from the provided example directory: “../examples/on_gke_end_to_end”domain: This is your GCP domaingsuite_admin_email: This is your admin email address associated with your GCP instanceorg_id: This is the GCP Org ID associated with your domain that you found aboveproject_id: This is the Project ID that was generated when you created the project aboveregion: Choose your region that you would like your resources in,us-central1,us-west1orus-east1are the cheapest US regionsconfig_validator_enabled: Set this to true to enable this option to be able to set policy guardrails for your setup
Copy and paste the definitions below for your file and replace with the values for your account.
module "forseti-on-gke" {
source = "../examples/on_gke_end_to_end"
domain = "mydomain.com"
gsuite_admin_email = "admin@mydomain.com"
org_id = "123456789012"
project_id = "forseti-123123"
region = "us-west1"
config_validator_enabled = "true"
}vi / vim Sidenote
Are you still in vi at this point? 2 options, power cycle your computer and use another editor, or, press the esc key / button and then :wq. Btw, if you ever vi a file and you can’t save because you need sudo, then :w !sudo tee %. You can sudo while writing the file and not have to exit and reopen it! You may also ask yourself, why did I say to use vi and not vim above.
Not only is vi the best editor, it only has 2 characters and on pretty much any system you probably use today it’s just a symlink to vim.
Notifications
Forseti supports multiple notification services.
- Slack
- Cloud Storage
- Cloud Security Command Center
You can specify the format of notification to be either.
- Human-readable data: CSV
- Structured data: JSON
For our purposes we will look at setting up email, slack and saving to Cloud Storage. If you are interested, follow this link to set up Cloud SCC Notifications.
Email Notifications
The quickest way to setup email notifications is by using Sendgrid (a third party email service). To do so, follow these steps:
- Create a SendGrid account
- Create a SendGrid API key
- We’ll use the configuration below to be able to send email later
Slack Notifications
If you are using Slack, you can also set Forseti to notify you there as well. Read Slack’s documentation to setup a webhook.
Modify the default configs
Now that we have the necessary Sendgrid and Slack configs, we are going to modify the configurations so that when we first deploy, notifications will be enabled. We will also modify the instance size to conserve costs and because our GCP footprint is not that large.
First modify examples/on_gke_end_to_end/variables.tf
- Edit the default node pool machine type. We changed it from
n1-standard-8ton1-standard-4 - Edit the Sendgrid API key and following stanzas for the email recipient and the email sender as determined by your Sendgrid configuration above
Next modify modules/on_gke/variables.tf b/modules/on_gke/variables.tf
- Edit the Slack webhook configuration, this will be where all of your alerts are sent to
- Edit the Cloudsql type configuration, we changed the default from
db-n1-standard-4todb-n1-standard-2
With these minor changes, we are all set to deploy.
Deploy using terraform
While still in your gke-cluster directory, you are now ready to run terraform and initialize the module.
terraform initYou can now apply the Terraform module. Note: since this is the first time running, it will plan and prompt you to apply.
terraform applyThe entire process will take about 5 – 10 minutes to run. If you encounter Error: Credentials not found in datasource, provider configuration or GOOGLE_APPLICATION_CREDENTIALS environment variable, you may have switched windows and will need to set the GOOGLE_APPLICATION_CREDENTIALS environment variable again.
export GOOGLE_APPLICATION_CREDENTIALS="../credentials.json"
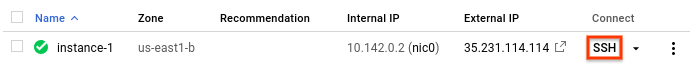
terraform applyOnce your cluster is up, you can now SSH to the Forseti client VM to start using the Forseti CLI. There are multiple ways to connect. For example with gcloud you can run the following command:
gcloud compute ssh --project [PROJECT_ID] --zone [ZONE] [INSTANCE_NAME]You can find the exact gcloud command to run to connect to your instance by opening up the console and navigating to the VM instances page and clicking on SSH.
Configuring your Forseti deployment
Now that Forseti is deployed, your configs will be read from your Storage bucket that was created by Terraform. You can further edit this to enable scanners, notifiers and more. You can edit the configs and then reupload them back to your bucket. When Forseti runs again, it will read the new config. You can also force a reload of the server via CLI.
gsutil cp gs://YOUR_FORSETI_SERVER_GCS_BUCKET/configs/forseti_conf_server.yaml .
gsutil cp forseti_conf_server.yaml gs://YOUR_FORSETI_SERVER_GCS_BUCKET/configs/forseti_conf_server.yamlNext steps
Forseti is an incredibly powerful tool and can be a bit intimidating to setup and manage. There are a ton of different options to configure and modify. Terraform makes the whole process so much simpler than the previous incarnations with the Python module. Further configurations that can be made include setting up Forseti Visualizer, Real Time Enforcer using Open Policy Agent (OPA) and setting up your own constraints for your environment using Config Validator.


