Data Privacy
Security Controls
for PII Data
Enterprises need to invest in controls to safeguard sensitive information and maintain compliance with data privacy regulations. It minimizes the risk of data breaches while allowing for safe and ethical data sharing, fostering trust with customers and partners.
Key Components of Data Privacy
-
Guiding framework for compliance with privacy laws
-
Promote consistent handling of sensitive data
-
Enable ongoing adaptation and improvement
-
Identify and categorize sensitive data based on risk
-
Enable focused and customized de-identification
-
Minimize the risk of overlooking critical data
-
Limit and manage access to sensitive data
-
Enforce use of raw data only when needed
-
Maximize business value of sensitive data
-
Obfuscate or remove PII from data sets
-
Safeguard integrity of sensitive data
-
Reduce the blast-radius of data breaches
-
Handle data erasure and rectification requests
-
Enforce policies for rights management
-
Build customer trust and market reputation
-
Demonstrate adherence to standards & regulations
-
Enable oversight and control of processes
-
Aid in risk assessment and process improvement
The Need for Automation
“Automation is crucial for data de-identification because there is nothing more dynamic than an organization’s data environment. Manual processes will almost never scale, and any application re-architecture tends to be ineffective because the requirements are too fluid. This is where Cyral’s solution shines.”

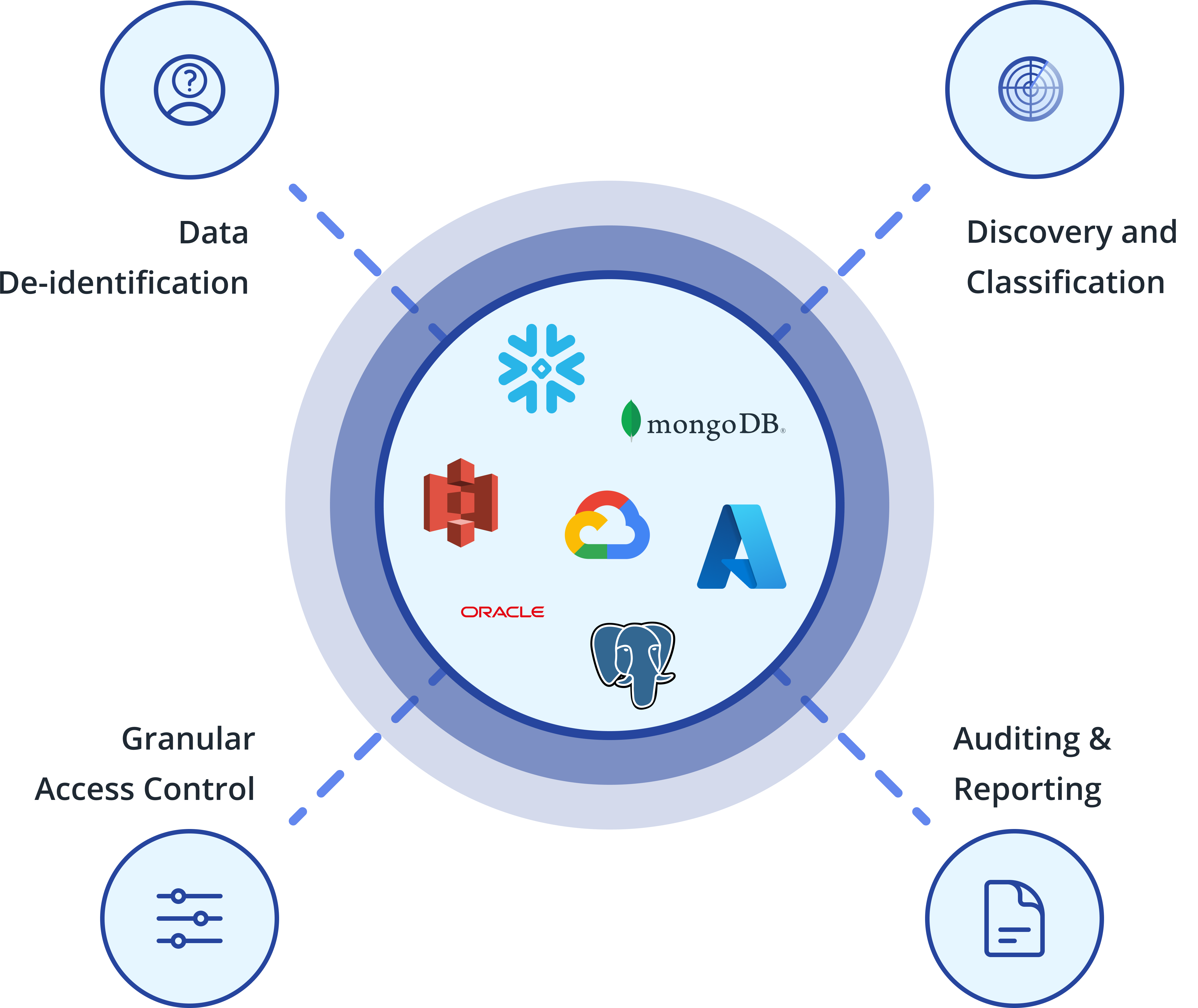
Cyral Automates Data Privacy End-to-End
Configurable Obfuscation
Granular Access Control
Discovery & Classification
Auditing and Reporting
Approval-based Access
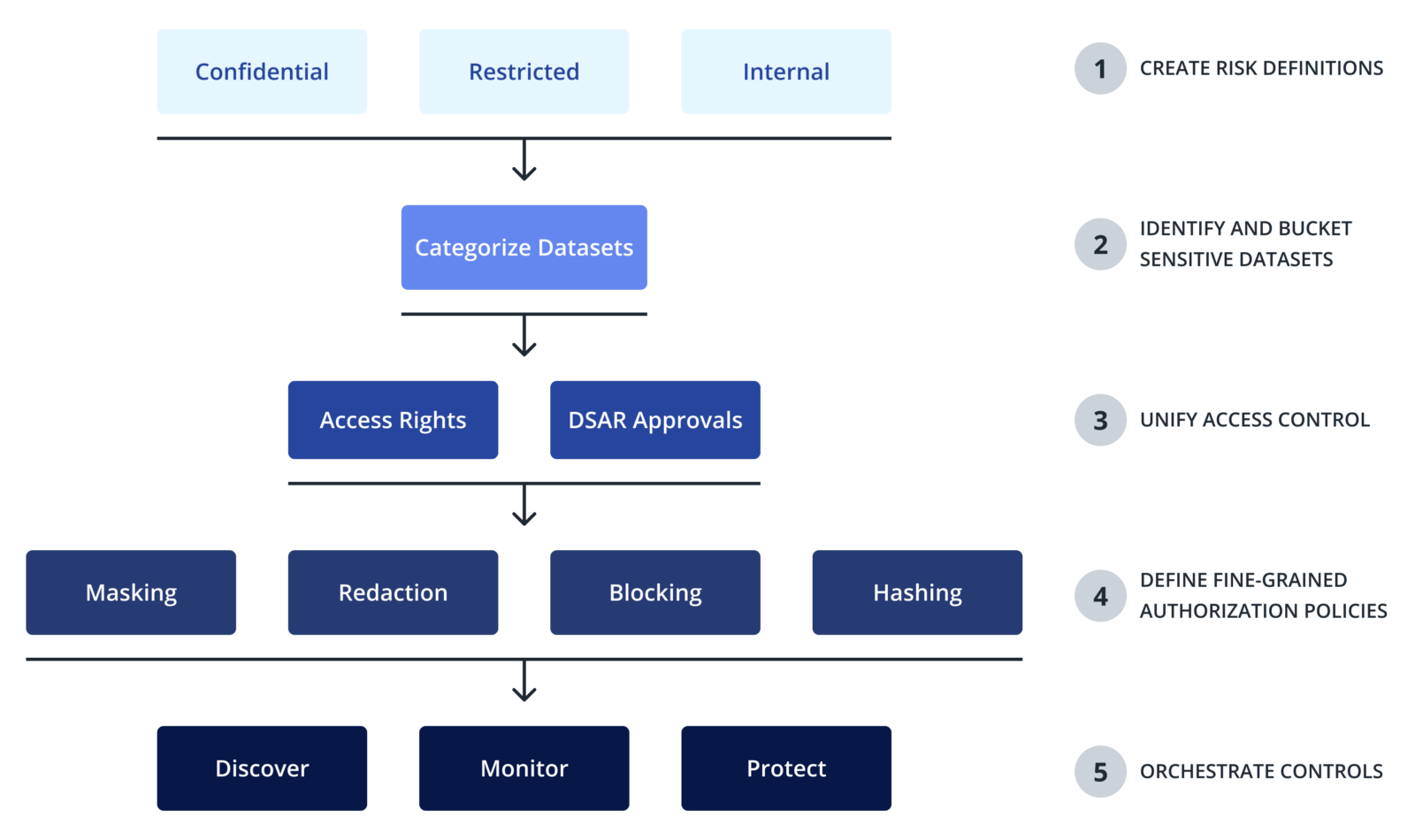
Read how Cyral enables data masking and row-level and column-level controls.
What People are Saying
“Anything that affects throughput matters to our business and what we like about Cyral is that it’s lightweight and runs in parallel with the data traffic, with no impact on performance.”

