Cloud Data Security
Discover, Control and Protect Your Data
Data-driven organizations must invest in data security to protect against data breaches and ensure the success of data democratization initiatives. By implementing robust data discovery & classification, fine-grained access controls & monitoring, and regular audits, they can securely share and leverage data while safeguarding sensitive information.
Key Components of Cloud Data Security
Discovery & Classification
Access Control
Data Protection
Data Masking & Obfuscation
Monitoring & Reporting

Navigating the Data Security Landscape
“ With the huge data sprawl and multitude of data security tools, many organizations feel overwhelmed with the complexity of selecting appropriate tools. For them to succeed, it is critical to take a risk based approach to data security, prioritizing the right kinds of controls based on where the most sensitive data is.”
-Gerhard Eschelbeck, CISO Kodak Robotics, former CISO Google
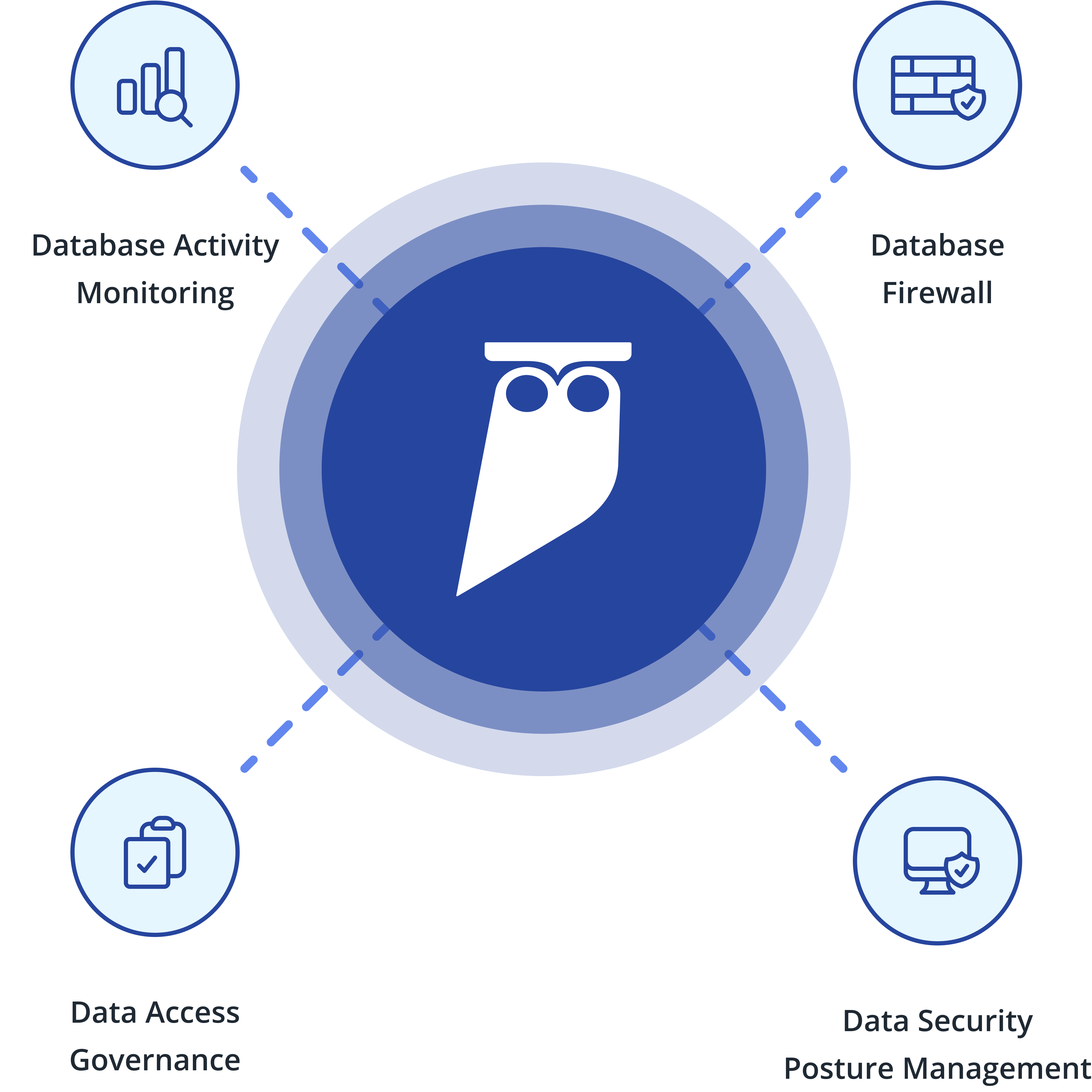
Cyral: An Integrated Approach to Cloud Data Security
Databases, data warehouses and data lakes are where the most sensitive data lives, but are typically the hardest to secure. Conventional IAM tools, for instance, long considered the cornerstone of corporate security do not provide adequate protection for data. They were built to control the usage of IT resources that are relatively finite, static and long-lived, such as a collection of SaaS applications or network connections. Data resources on the other hand are frequently ephemeral and rarely static.
Cyral provides a single platform that consolidates controls for discovery, access control, fine-grained authorization, reporting and monitoring.
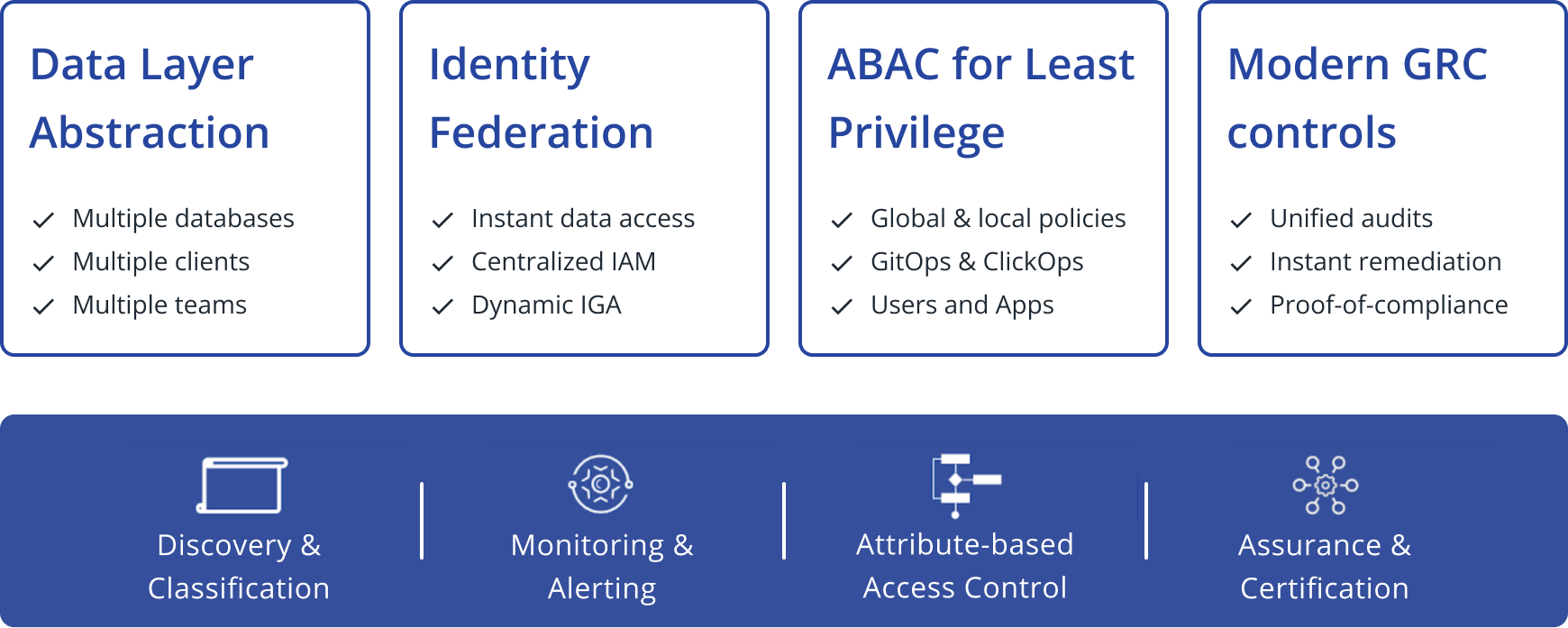
Data Layer Abstraction
Cyral offers a layer of abstraction over your data assets, enabling simple access control across diverse data stores, be it SQL, NoSQL, or hybrid setups. This abstraction eliminates the need to write different access control policies for each database, simplifying your workflow and making data access management more efficient.
Identity Federation
Our platform integrates with your existing Identity and Access Management (IAM) systems. This means you can centralize and reuse your existing entitlements, making access management less cumbersome and more secure. Furthermore, allowing data users to access databases using credentials they’re familiar with alleviates them of the burden of tracking various sets of database credentials.
ABAC for Least Privilege
Cyral enables teams to maintain powerful policies leveraging Attribute-Based Access Control (ABAC) to ensure the principle of Least Privilege. By using various attributes collected both at the time of connection and the moment the request is made, our platform enables fine-grained access policies that not only meet but exceed industry standards for database protection.
Modern GRC Controls
Navigating the intricate web of Governance, Risk, and Compliance (GRC) is simplified with Cyral. Our platform comes equipped with modern GRC controls that enable you to generate comprehensive reports on data access, user activity, and security incidents. This removes the need for database access reviews, simplifies compliance reporting, and demonstrates a strong governance
program to auditors and stakeholders.
Built upon these four pillars, Cyral’s platform represents a true end-to-end database security governance platform.




