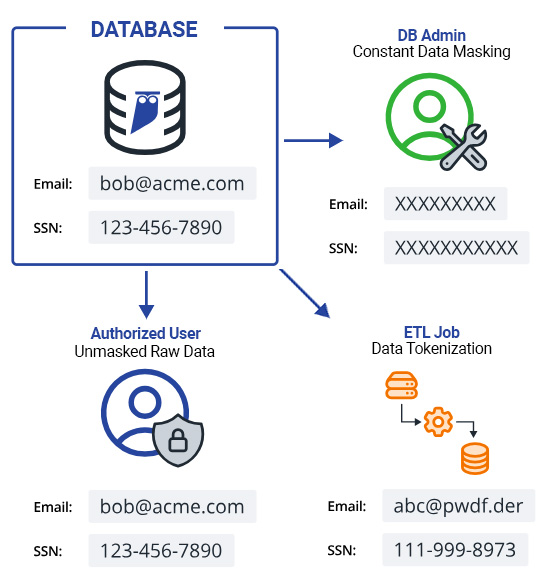
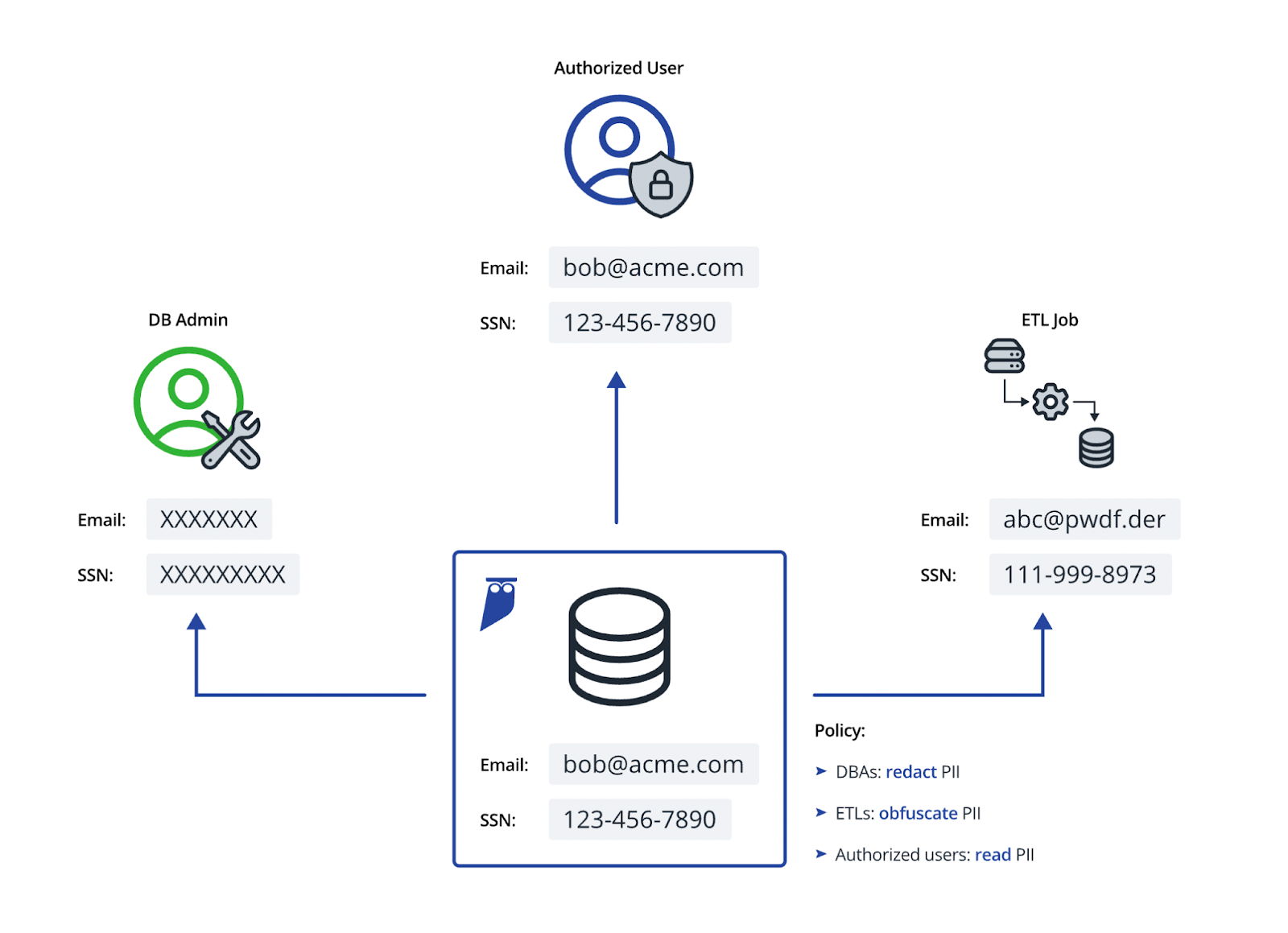
Data masking has emerged as a highly favored technique for devaluation due to its adaptability, effectiveness in preserving data usability, and its diverse application across various industries and data environments. It aligns with the requirements of numerous data privacy regulations, such as GDPR, HIPAA, and PCI DSS. It allows organizations to comply with these standards by obscuring sensitive details while ensuring data remains useful for legitimate purposes.
One of the unique advantages of masking is its adaptability data masking can be implemented in a variety of ways that helps provide an easier alternative to other forms of data devaluation and obfuscation. Common data masking techniques include:
Static Masking: Replaces original data with consistent, static values, such as replacing all occurrences of a specific data type with the same masked value.
Dynamic Masking: Involves generating masked data in real-time when it is queried, potentially even producing different masked outputs for each query or user, leaving the original data as-is.
Format-Preserving Masking: Modifies data while retaining its format, ensuring the length, structure, and data type of the masked information remain unchanged (could be dynamic or static).
Shuffling: Rearranges the order of data records, making it more challenging to identify specific information while preserving the dataset’s structure.
Character Masking: Alters specific characters within the data, such as replacing specific digits in credit card numbers or phone numbers, while retaining the data’s general format.
These techniques offer a choice between security and utility, making masking a popular choice for safeguarding sensitive information.