SSO with ForgeRock
With Cyral, you can authenticate users against your ForgeRock identity provider (IdP), and Cyral can read each user's group memberships from ForgeRock to determine the user's privileges. This integration uses ForgeRock as a SAML identity provider.
Follow these steps to use your ForgeRock to authenticate database users and Cyral administrators.
Overview
note
ForgeRock menu examples and screenshots in this document are based on ForgeRock AM version 7. Your setup might look different.
Integrating Cyral with ForgeRock for SSO involves the following main steps:
- Find the LDAP attributes used to store user email, last name, and first name, as well as the LDAP RDN type used to identify groups.
- Create a hosted identity provider ("hosted IdP") in ForgeRock, configuring request/response signing, name/ID value map, assertion processing (attribute maps), and then downloading your SAML metadata file from ForgeRock.
- Create the ForgeRock integration in Cyral, copying the required fields from the downloaded SAML metadata file, and customizing the integration as needed.
- Upload service provider metadata to the ForgeRock AM admin console. Create a remote entity provider, upload the Cyral service provider metadata, and configure request/response signing.
- Test the integration.
Create SAML IdP app in ForgeRock
Prerequisites
Setting up the integration requires some details from the identity store configured in your ForgeRock deployment. The Cyral integration supports only ForgeRock deployments that use an LDAP-based identity store. Before you start, find the LDAP attributes that hold the following values for users:
- first name
- last name
- group memberships
Create entity provider
First, create the identity provider integration (IdP) in ForgeRock. Follow these steps in the ForgeRock AM Management Console:
- Select the realm that you wish to integrate with Cyral
- Go to Applications → Federation → Entity Providers
- Click Add Entity Provider and select Hosted from the
drop down menu. This will create a new SAML identity provider
hosted by ForgeRock.
- Add an Entity ID.
- Add an Identity Provider Meta Alias.
- Click Create.
- Configure your new hosted identity provider as follows.
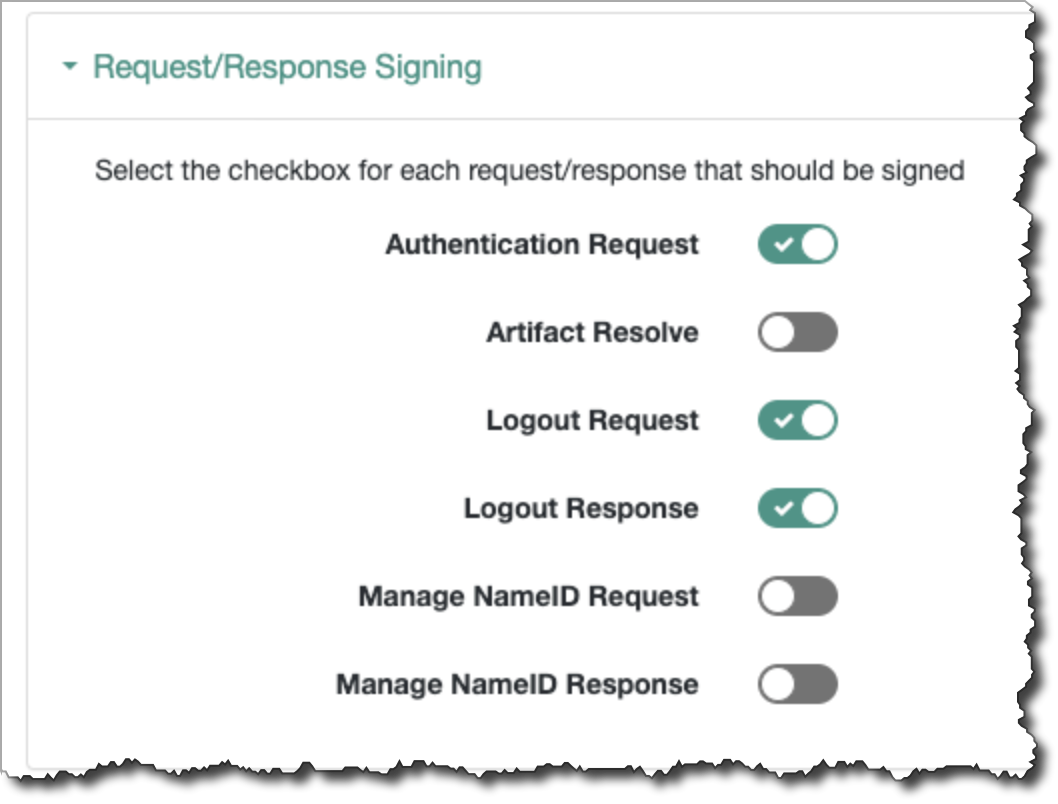
- Go to Assertion Content → Signing and Encryption → Request/Response Signing.
- If you don’t want SAML authentication requests (AuthnRequests) and Assertions
to be signed, leave all toggles switched to off/false. Otherwise, if you want
AuthnRequests and Assertions to be signed (the Cyral default,
recommended configuration), configure it as shown below, turning on
signing for authentication requests, logout requests, and
logout responses.
- If you don’t want SAML authentication requests (AuthnRequests) and Assertions
to be signed, leave all toggles switched to off/false. Otherwise, if you want
AuthnRequests and Assertions to be signed (the Cyral default,
recommended configuration), configure it as shown below, turning on
signing for authentication requests, logout requests, and
logout responses.
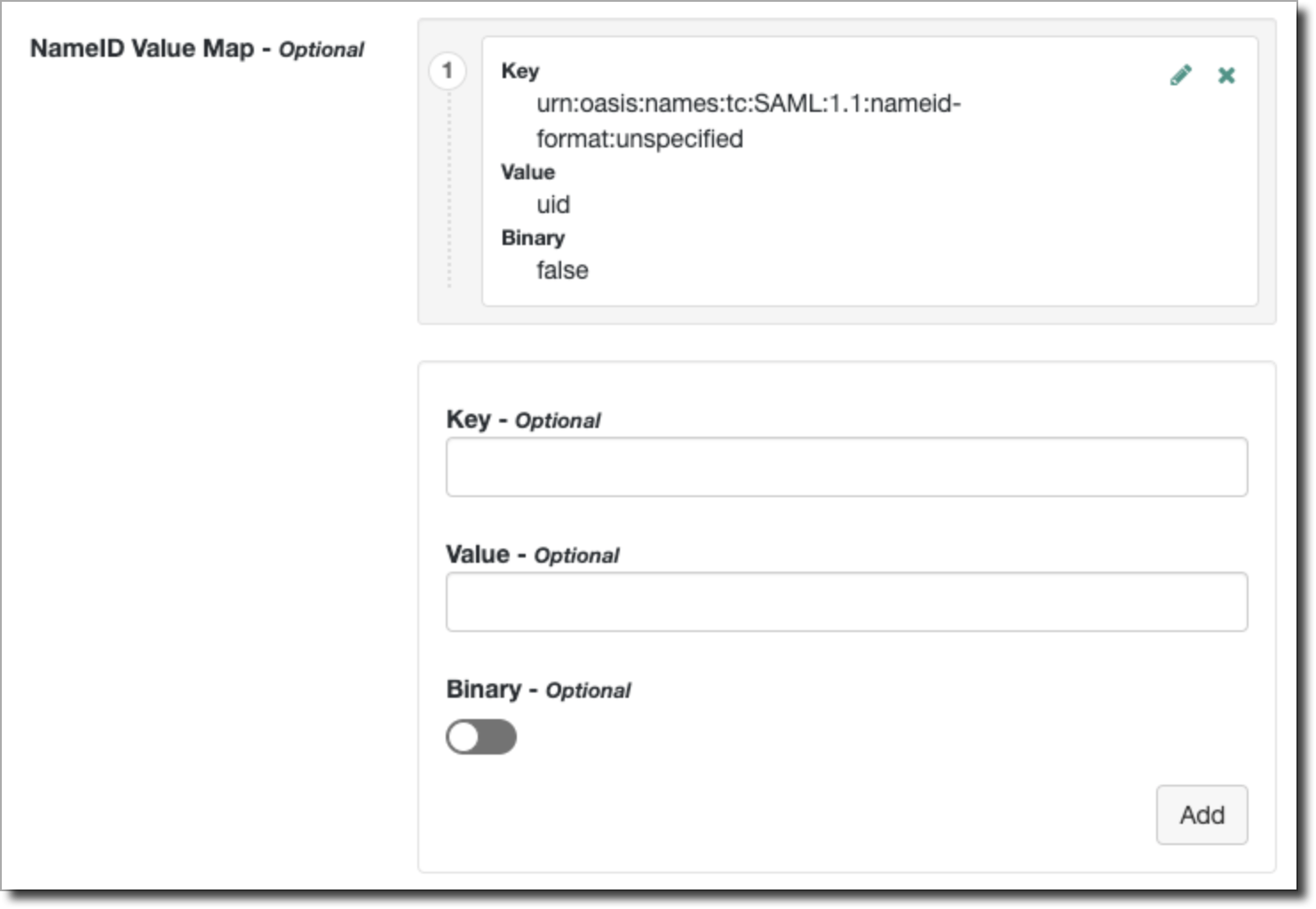
- Go to Assertion Content → NameID Format → NameID Value Map.
- Choose the LDAP attribute that will be used for the SSO username in Cyral.
To use the user's email address, leave the default setting; to use
the username from ForgeRock, configure it as shown below:
- Choose the LDAP attribute that will be used for the SSO username in Cyral.
To use the user's email address, leave the default setting; to use
the username from ForgeRock, configure it as shown below:
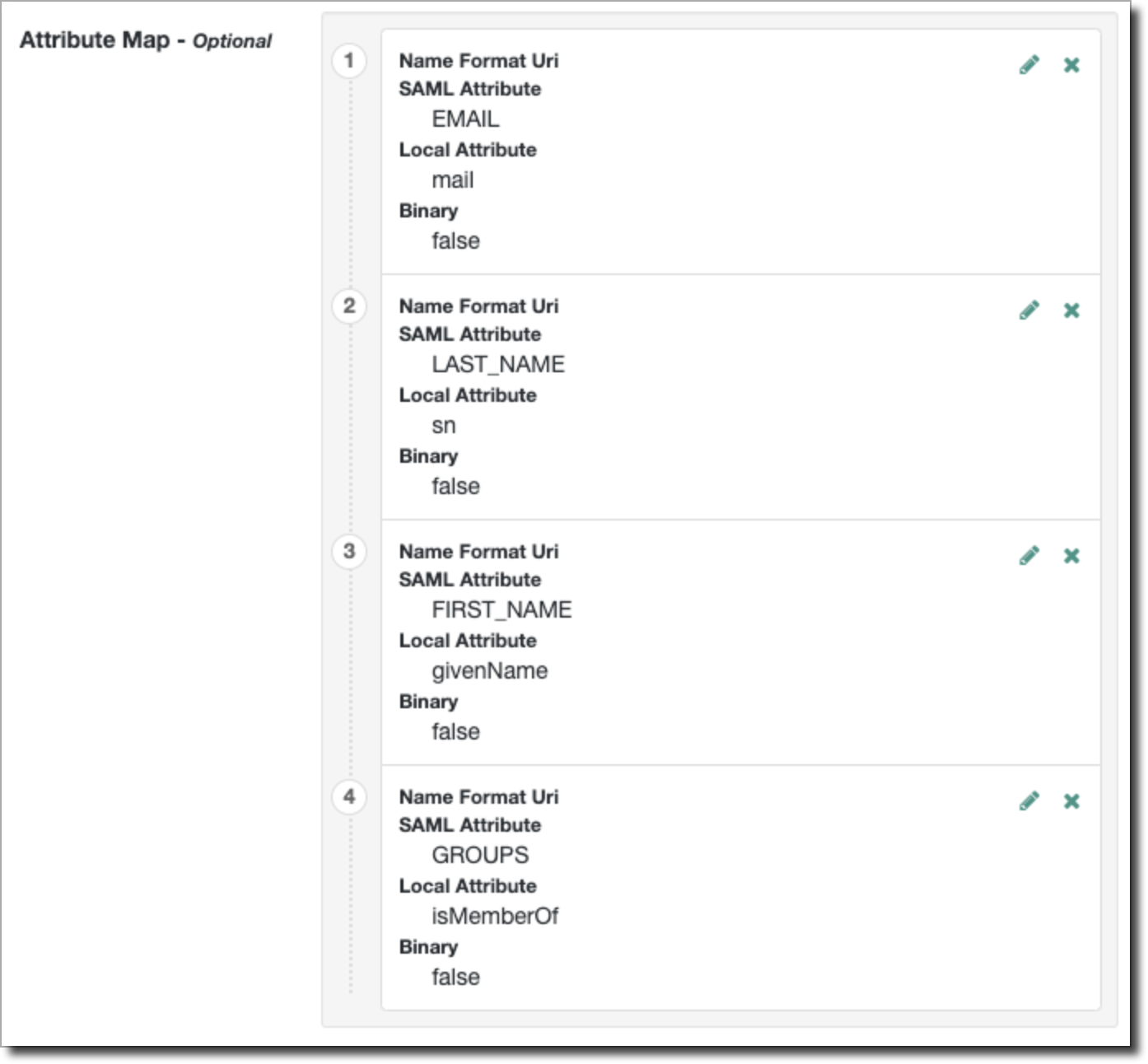
- Go to Assertion Processing → Attribute Mapper
- Create Attribute Maps from the local LDAP attributes used to identify a user’s email, first name, last name, and group membership. These values are labelled local attributes, and they may vary across ForgeRock deployments.
- The SAML Attribute values must match the screenshot exactly. These must be EMAIL, LAST_NAME, FIRST_NAME, and GROUPS.
- The following local attribute values are the defaults for OpenDJ in ForgeRock:
- Click Save Changes.
- Go to Assertion Content → Signing and Encryption → Request/Response Signing.
- From the sidebar on the left, go to Identity Stores and select the
identity store that is used for the integration.
- Go to User Configuration and add
isMemberOfto LDAP User Attributes, if it is not already there - Go to Group Configuration and copy down the value for LDAP Groups Search Attribute.
- Go to User Configuration and add
- After creating the new hosted identity provider, download the SAML metadata file from your ForgeRock instance. The easiest way to do this is explained in this ForgeRock support article, in the section, “Using your browser or curl.”
Add Forgerock IdP to Cyral
Next, add the ForgeRock IdP integration in Cyral:
In the Cyral management console, select Integrations.
On the ForgeRock tile, click Setup and click New Integration.
Provide an Integration Name for this SSO provider and click Add Integration. This is the name your users and administrators will see when they use or set up this SSO provider.
Fill out the fields using the SAML metadata file you downloaded from your ForgeRock instance.
- For Single Sign-on and Single Logout, make sure to choose the URLs that use
HTTP-POST.- The XML tag should say
Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST"
- The XML tag should say
- For the signing certificate, make sure to select the X509 Certificate that has the XML tag
use="signing". - The LDAP Group Attribute should be your identity store's value for the LDAP Groups Search Attribute.
- For Single Sign-on and Single Logout, make sure to choose the URLs that use
Modify the advanced configuration settings if needed.
Save the integration.
Click Export SP Metadata to download the service provider metadata. This is the Cyral SP Metadata document.
caution
The following ForgeRock features have not been tested with Cyral:
- HTTP-Redirect is untested and not guaranteed to work
- Back channel logout is untested and not guaranteed to work
- Wants assertions encrypted is untested and not guaranteed to work
ForgeRock settings
Standard settings
- Single Sign-On Service URL: The URL that must be used to send authentication requests (SAML AuthnRequest).
- Single Logout Service URL: The URL that must be used to send logout requests.
- LDAP Group Attribute: This parameter specifies which RDN type is
used to identity group membership. For example, if an LDAP DN sent
in a SAML assertion is
"cn=Everyone,ou=groups,dc=openam,dc=forgerock,dc=org,", and the LDAP Group RDN Type iscn, the mapper will interpretEveryoneas the group name. - Validate Signature: Whether the SP will validate digital
signatures from the IdP. Cyral recommends that you turn this on for
proper security. The default value is
true. - Signing X.509 Certificate: Required if Validate Signature is set to True. The certificate used to validate signatures.
Additional settings
- Display Name: The name used to identify the integration on the Cyral login page. This is seen by all users who login through the given integration, whereas the ‘name’ of the integration is only seen internally by administrators who manage SSO integrations. This is the name that will be seen in the Cyral UI.
- Backchannel Logout: Set this value to
false. - Wants AuthnRequests Unsigned: Indicates whether the identity
provider expects a signed AuthnRequest. Defaults to
false, meaning the IdP expects signed requests. - Wants Assertions Unsigned: Indicates whether this service provider
expects a signed Assertion. Defaults to
false, meaning the SP expects signed assertions. - Wants Assertions Encrypted: Set this value to
false(the default), meaning the SP does not expect assertions to be encrypted. - Disable Force Authentication: Indicates whether the identity
provider must authenticate the presenter directly rather than rely
on a previous security context. Defaults to
false. - Allowed Clock Skew : Clock skew in seconds that is tolerated when validating identity provider tokens. Default value is zero.
- SAML Binding Type: Set this value to HTTP-POST.
Set ForgeRock to recognize Cyral
Follow these steps in the ForgeRock AM Management Console:
- Go to Applications → Federation → Circles of Trust.
- Click Add Circle of Trust and name it.
- Add your hosted identity provider to the Entity Providers field.
- Save it.
- Go to Applications → Federation → Entity Providers
- Click Add Entity Provider and select Remote from the drop down menu. This creates a new SAML service provider.
- Upload the Cyral SP Metadata document.
- Select the Circle of Trust you just created.
- Click Create.
- Do one of the following, depending on your ForgeRock setup:
- If using unsigned SAML messages: If you switched the options
Wants AuthnRequests Unsigned and Wants Assertions Unsigned
to
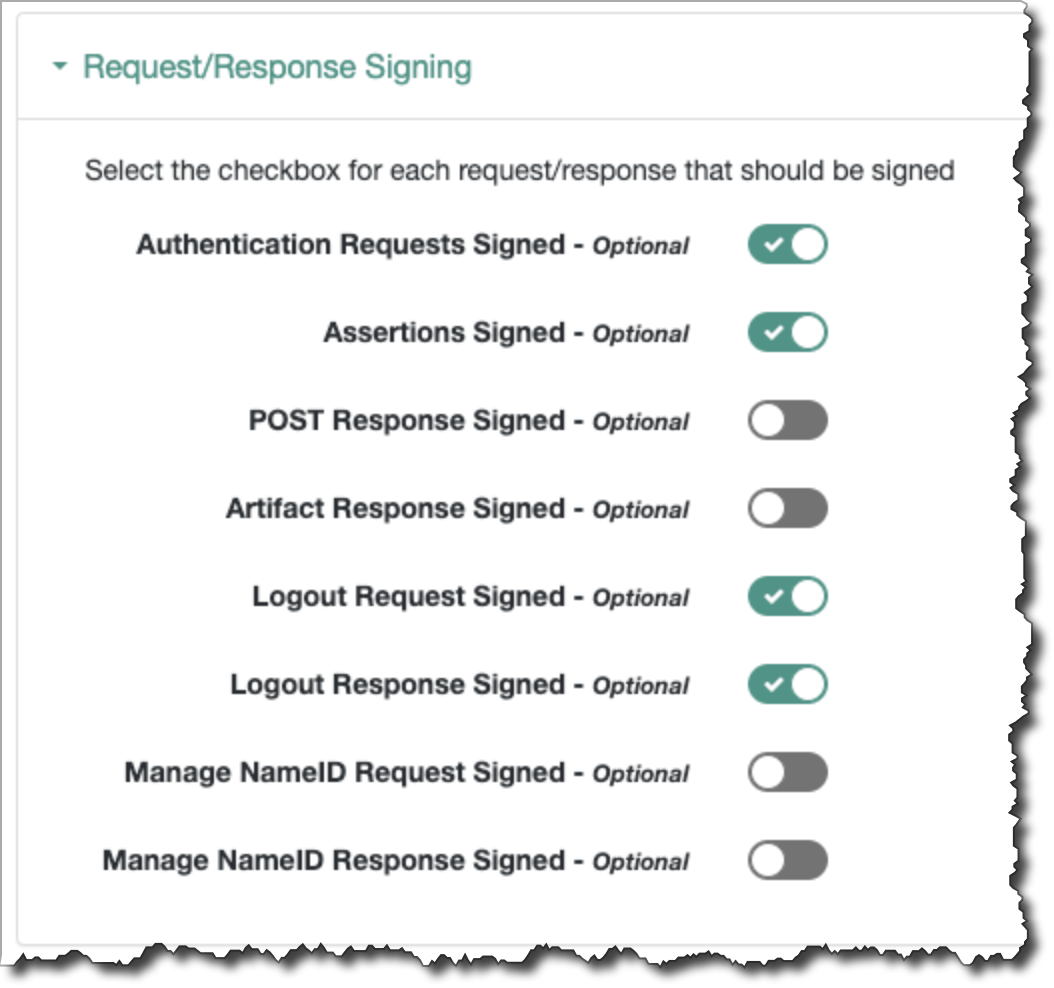
trueabove (meaning your ForgeRock installation will expect unsigned SAML AuthnRequests and Assertions), you are finished with the setup. - If using signed SAML messages: If you kept ForgeRock's
default settings for Wants AuthnRequests Unsigned and Wants
Assertions Unsigned (meaning your ForgeRock installation will
expect signed SAML AuthnRequests and Assertions) then you must
do the following: Go to Assertion Content → Signing and
Encryption → Request/Response Signing. You'll see that
Authentication Requests Signed and Assertions Signed
are toggled on. Leave them
on. Toggle the following valuesonas well: Logout Request Signed and Logout Response Signed.
- If using unsigned SAML messages: If you switched the options
Wants AuthnRequests Unsigned and Wants Assertions Unsigned
to
- Click Add Entity Provider and select Remote from the drop down menu. This creates a new SAML service provider.
Next step
See Set up SSO authentication for users for the steps to activate SSO authentication on each repository that will use it.