SSO with Okta
With Cyral, you can authenticate database users against your Okta identity provider. Optionally, Cyral can read each user's group memberships in Okta to set the user's data privileges and/or Cyral administrative role. This integration uses Okta as a SAML identity provider (IdP).
In this tutorial, we provide you two options to setup an Okta instance to authenticate database users and Cyral administrators: Terraform or manual configuration.
If you are a Terraform user, you can use our
Cyral IdP integration module for Okta
to setup both the Okta environment and Cyral control plane and get
the integration up and running in a few minutes using a single
terraform apply command.
If you don't use Terraform, you can follow the steps in this section.
In Cyral management console, create an Okta integration
- In the Cyral management console, select Integrations.
- On the Okta tile, click Setup and click New Integration.
- Provide an Integration Name for this SSO provider. This can be any user-friendly name that users will recognize. This is the name your users will see when they choose this Okta identity provider as their sign-on method.
- Click Add Integration, to create the integration draft.
- After that, you will be able to see the integration URLs fields, keep this tab open as you will need to copy these URLs and use them to configure your Okta App.
- Now, before continuing with the integration configuration, you will need to configure your Okta App first, by following the steps in the next section.
In Okta, create an app to represent Cyral
Go to https://login.okta.com/ and log in to your account as an Administrator.
Click on the Admin button on the top right side of the screen.
Click on Applications: Applications and click Create App Integration.
Choose SAML 2.0 as the sign on method, and click Next.
Give the app an App name (for example, "Cyral"), add the Cyral logo as the App logo, and click Next.
On the Configure SAML section, you will need to configure the SAML URLs for the Okta App. You can obtain these URLs from the integration draft you created in the Cyral management console. Follow the steps below to configure the SAML URLs:
- Single sign on URL: Copy the Single Sign-On URL from the integration draft and paste it
into the Okta App field Single sign on URL. This field is also known as the Assertion Consumer Service URL
and has the following format:
https://$CYRAL_CONTROL_PLANE_DOMAIN/auth/realms/default/broker/$IDP_INTEGRATION_ALIAS/endpoint/clients/$IDP_INTEGRATION_ALIAS-client - Requestable SSO URLs: Select the option Allow this app to request other SSO URLs, to allow adding
multiple Requestable SSO URLs. After that, copy the first URL of the Requestable SSO URLs from the
integration draft and paste it into the first URL field of the Okta App Requestable SSO URLs and
set its Index equal to 0. Next, click Add Another and add a second URL, by copying
the second URL of the Requestable SSO URLs from the integration draft and pasting it into the second
URL field of the Okta App Requestable SSO URLs, then set its Index equal to 1. The two
Requestable SSO URLs should have the respective formats:
https://$CYRAL_CONTROL_PLANE_DOMAIN/auth/realms/default/broker/$IDP_INTEGRATION_ALIAS/endpoint/clients/$IDP_INTEGRATION_ALIAS-clienthttps://$CYRAL_CONTROL_PLANE_DOMAIN/auth/realms/default/broker/$IDP_INTEGRATION_ALIAS/endpoint - Audience URI (SP Entity ID): Copy the Audience Restriction from the integration draft and paste it
into the Okta App field Audience URI (SP Entity ID). This field is also known as the
Service Provider Entity Id and has the following format:
https://$CYRAL_CONTROL_PLANE_DOMAIN/auth/realms/defaultinfo
The definition of the placeholders used in the URL formats above are:
$CYRAL_CONTROL_PLANE_DOMAINis the domain for your Cyral control plane.$IDP_INTEGRATION_ALIASis a unique alias that identifies the Okta integration, configured in the Cyral management console. It is prefixed byokta., followed by a unique ID number. For example:okta.abc86c17-44e2-434b-9f57-1721f1850b48.
- Single sign on URL: Copy the Single Sign-On URL from the integration draft and paste it
into the Okta App field Single sign on URL. This field is also known as the Assertion Consumer Service URL
and has the following format:
Map the Attribute Statements using the name/value mappings shown below. Set the Name format to
Basic.Name Name Format Value EMAIL Basic user.email FIRST_NAME Basic user.firstName LAST_NAME Basic user.lastName In the Group Attribute Statements section, specify the groups information that Okta will share with Cyral. Set the name of each entry to
groupsand the format toBasic. In the filter, specify regex that matches the groups you'll use. For example, if you wish to send group information for the groups named "Mathematicians" and "Scientists," you'll set the groups to Match the regex(Scientists)|(Mathematicians). If you want to send all groups, you can use the regex.*. Click Next once you've specified the needed groups.Name Name Format Value groups Basic Matches regex: .* In the next page, we suggest selecting the options:
- I’m an Okta customer adding an internal app
- This is an internal app that we have created
Click Finish and you'll be redirected to the page of your newly created Okta App.
On the Sign On section of your Okta App, go to the SAML Signing Certificates and locate an Active certificate. Then, click on the Actions button and click on View IdP metadata, as shown in the screenshot below:
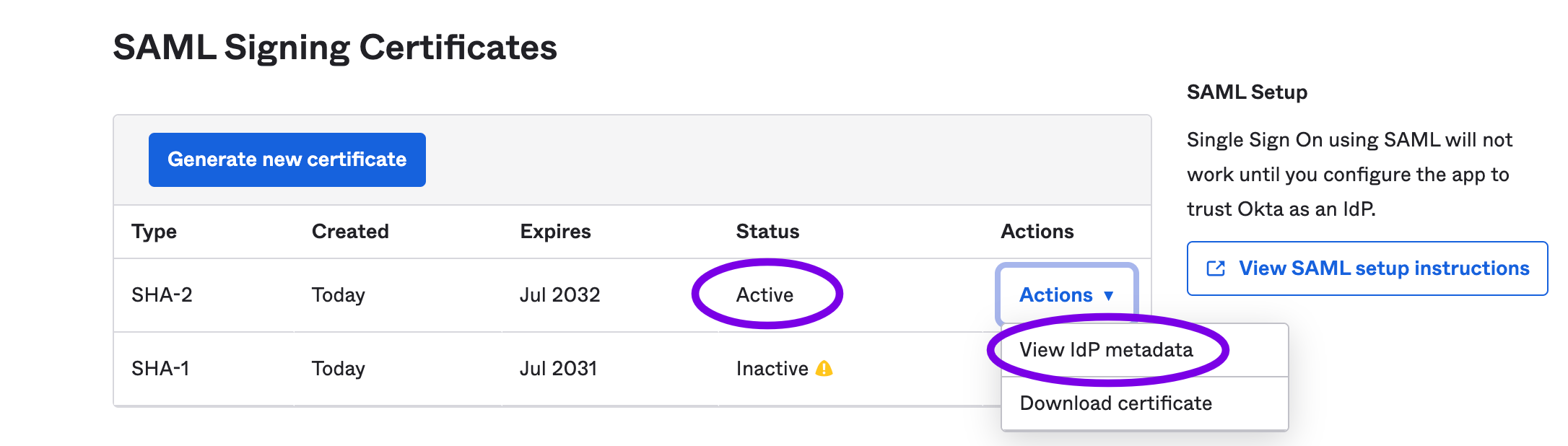
A new page will be opened with the SAML metadata. Copy the URL of this page and use it to finish the Okta integration configuration in the Cyral management console, by pasting the SAML metadata URL into the SAML Metadata URL field. After that, click Save to successfully create your Okta integration.
Add users and groups to the Okta app
In Okta, you must assign groups, users, or both to the Okta app that represents Cyral. Single sign-on via the Cyral/Okta integration is only available to users who are registered in this way, either individually or as a member of a registered group.
Go to Applications → Applications and click on the Okta app that represents Cyral.
In the app page, go to the Assignments section, click the Assign button and do one or both of the following:
- Click on Assign to People and select the users who can sign on via Cyral
- Click on Assign to Groups and select the groups whose members can sign on via Cyral.
Save the assignments by clicking in Done. This completes your SSO setup in Okta.
Next step
See Set up SSO authentication for users for the steps to activate SSO authentication on each repository that will use it.