Set up data access alert notifications in Microsoft Teams
When Cyral detects suspicious activity or a violation of your data policies, it can broadcast alert notifications via messaging and incident management platforms.
To set this up with Microsoft Teams, open the Cyral management console, click Integrations in the sidebar, and click Configure on the Microsoft Teams card.
Create the webhook
In Microsoft Teams, create a channel that will receive alerts from Cyral.
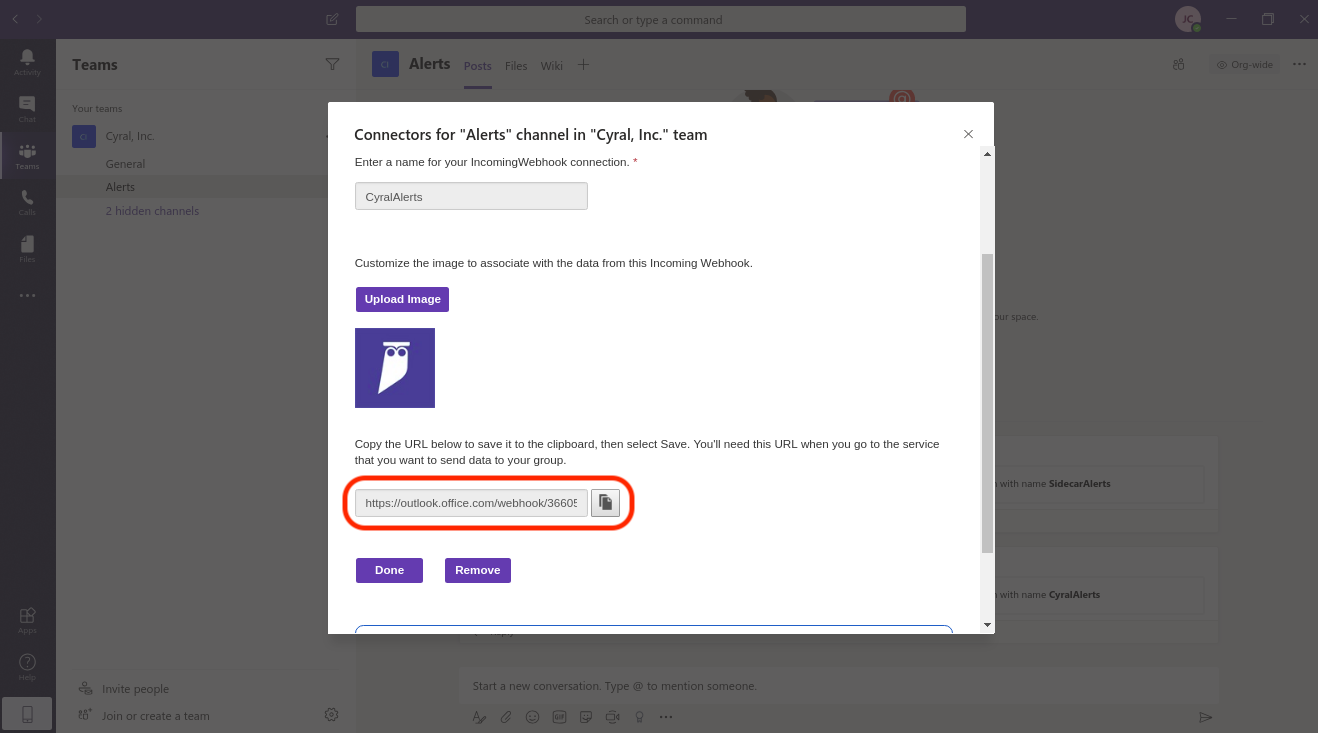
In Microsoft Teams, configure the connector by navigating to Apps: Connectors: Incoming Webhook.
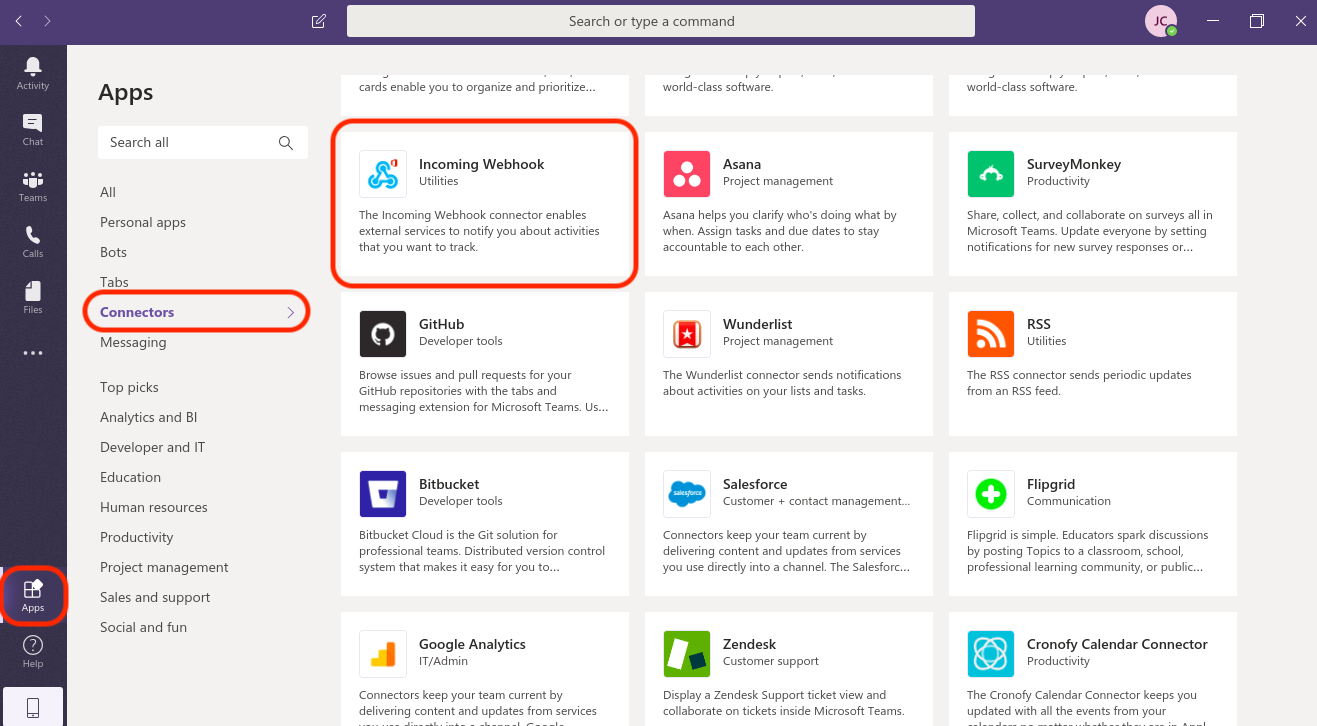
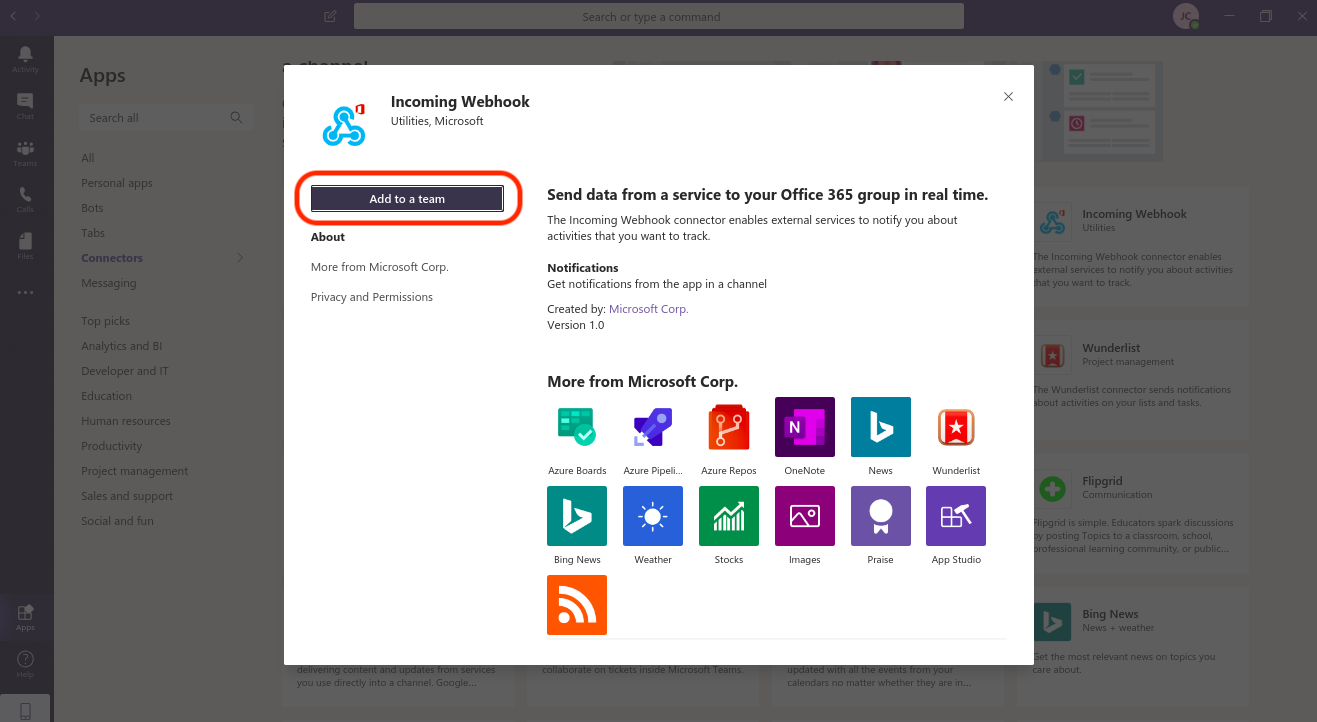
Click Add to a team, then associate the incoming webhook with the channel you created in step 1 and click Set up a connector.
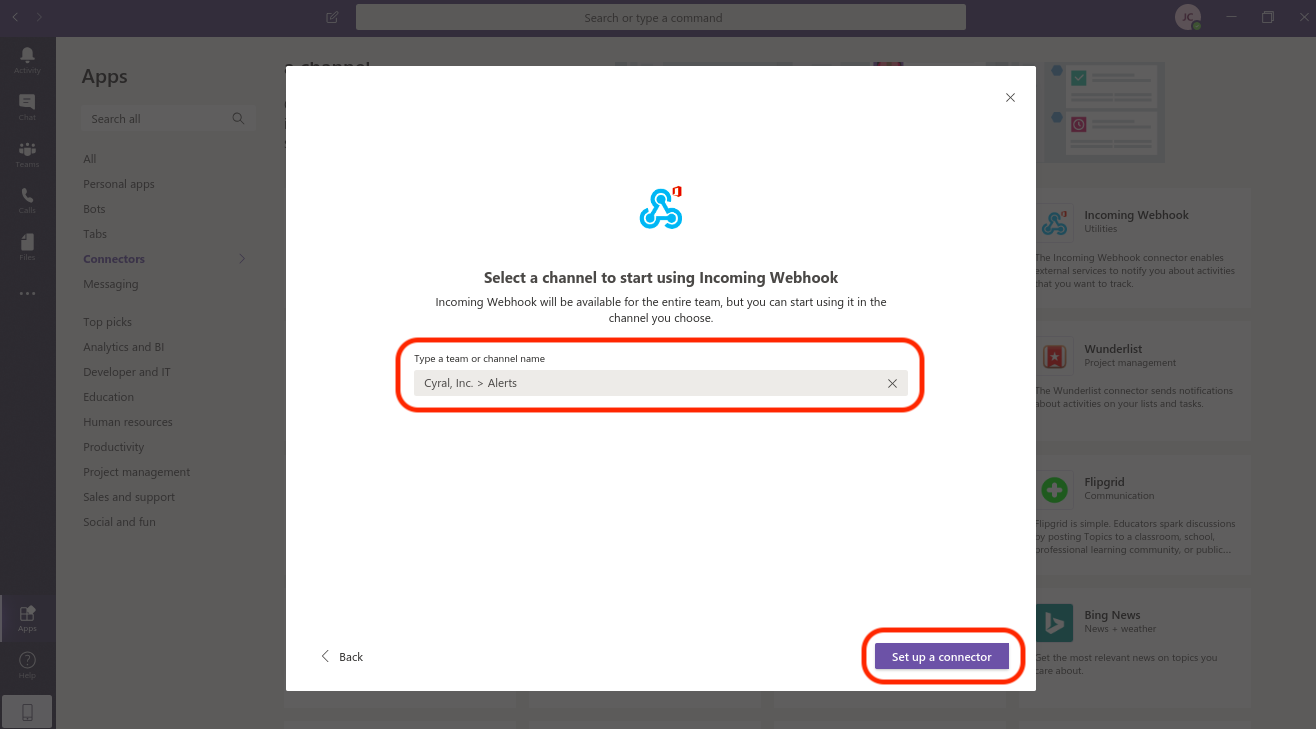
Now, give the webhook agent a name. Additionally, you can set our owl as the image for this agent. Finally, click Create.
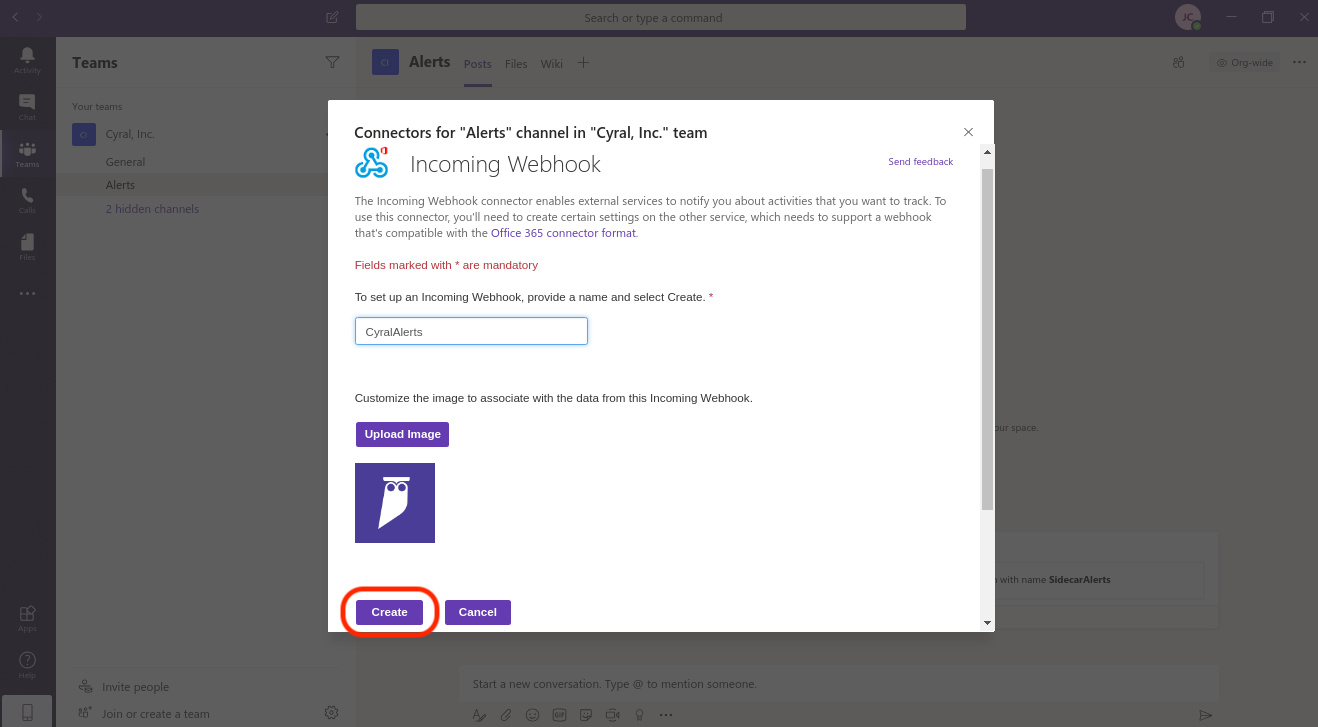
Once the webhook is created, you'll be able to copy the URL from the bottom of the same window.
Configure the sidecar with the webhook
Add the webhook retrieved in the previous steps. In the Cyral Management Console, click Integrations and click Configure on the Microsoft Teams card.
Configure the repo of interest to send alerts when accesses to it trigger a policy violation, replacing
$CYRAL_CONTROL_PLANE_DOMAINand$REPO_IDin the following Cyral API command:
curl -H "Content-Type: application/json" -X POST https://$CYRAL_CONTROL_PLANE_DOMAIN/v1/repos/$REPO_ID/conf/analysis -d '{"alertOnViolation":true}'