Advanced repo settings
To set advanced communications, logging, analysis, and alerting options for a repository, go to Data Repos, then find and click on the name of your repository, and click the Advanced tab.
Authentication
Specify how users will authenticate with this repository. Cyral supports identity providers, Multi-Factor Authentication, and authentication based on AWS IAM.
By default, no authentication mechanism is selected, so the None radio button will be
checked. This results in using the repository's native authentication (if
Allow native authentication for this database is selected).
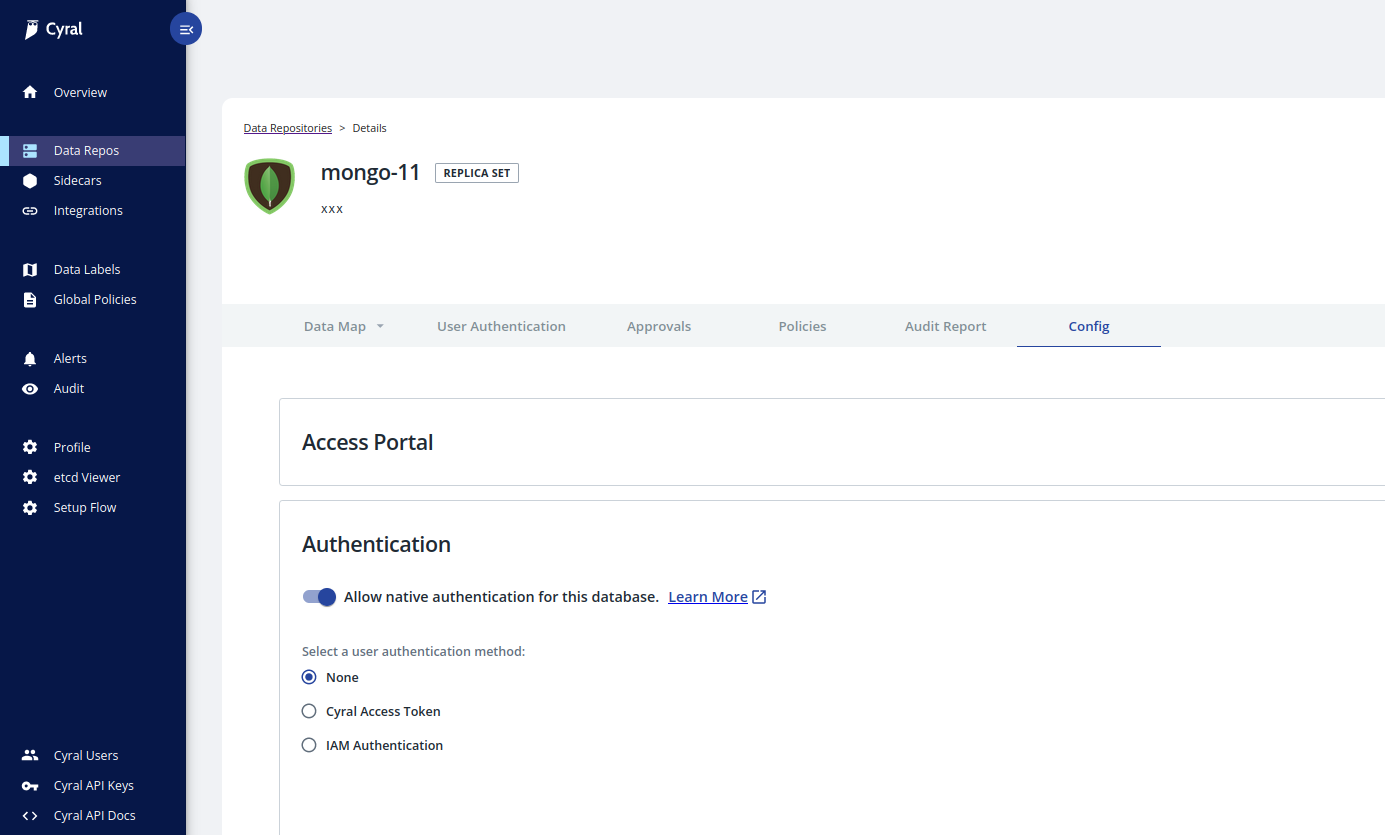
Identity Provider
The Cyral Access Token radio button allows you to select an identity provider
you have integrated with Cyral in order to enable SSO authentication to the repository.
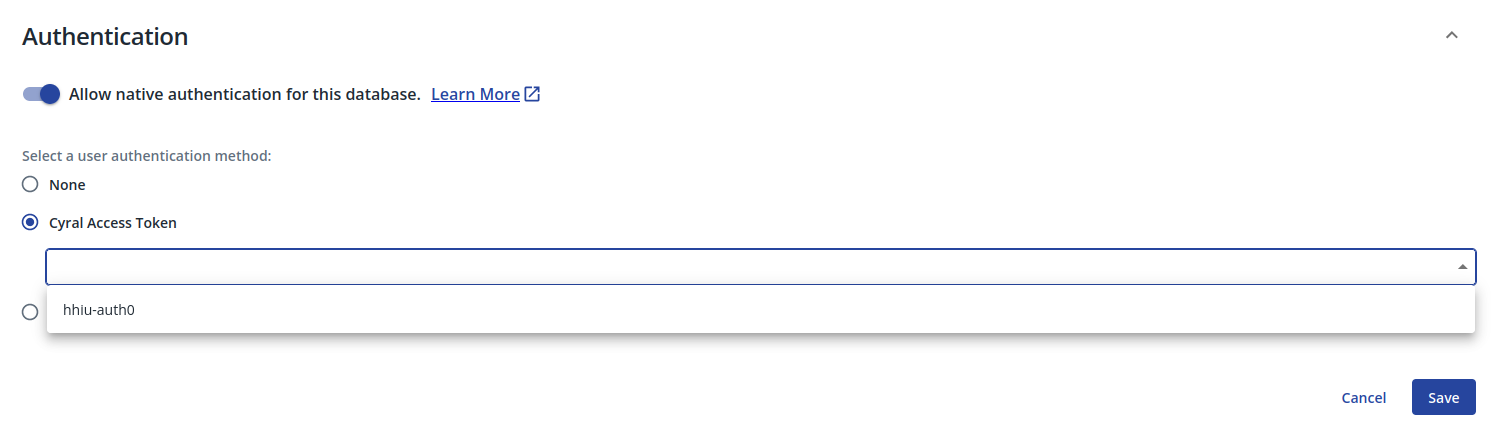
AWS IAM
The IAM Authentication option allows you to select an AWS IAM integration in order to
authenticate users.
note
AWS IAM for authentication is currently available only for MongoDB repositories
Client TLS
Specifies whether the sidecar will require TLS communication with clients.
- Disable: Do not require clients to use TLS
- Enable: Require clients to use TLS
Repository TLS
Specifies whether the sidecar will communicate with the repository using TLS.
- Disable: Do not use TLS with repo
- Enable: Use TLS with repo
- Enable and verify certificate: Use TLS with repo and verify the repo's certificate
Logs
Redact literal values
When checked, data that might reveal the contents of your database is
not included in the logs. For example, a log entry for a statement
with a WHERE clause will not include the literal values the user
provided in the WHERE clause. Each such value will be replaced with
the string, ${cyral-redact}.
Enhance database logs
When checked, Cyral inserts the user's session data as a comment in each query so that it appears in your native database logs.
This feature provides a database-native supplement to the more complete Cyral query logs you've configured in the Log Settings panel for the repository. With this feature active, the user's identifying information will appear as comments in each query. For the person who ran the query, this shows:
- username (usually the SSO username)
- email address
- group membership
- repository username (local or native account on the repository)
- repository role (user’s native role on the repository)
These values will also appear in the identity block of your Cyral
query logs, if this repository is set to log Data activity.
Optionally, you can add the contents of the repo, client, and/or
sidecar logging blocks as query comments, as well. To set this up,
use the Cyral API. See Logging additional data as comments on a query.
Alerts
Alert on policy violations
When an action violates a Cyral policy, an alert is sent via your configured messaging platform. This requires a Cyral policy. If you have no policies, use preconfigured alerts, instead.
Enable preconfigured alerts
Preconfigured alerts don't rely on Cyral policies. Instead, they're triggered by common DDL, and other significant actions on your data repository, such as; creating, modifying or deleting an object; creating user account or role; modifying a user account, authentication mechanism, object, or role; granting/revoking user or role privileges; modifying database-native audit and logging settings or configuration; or running a privileged command.
Analysis
Perform filter analysis
When a database query performs a filter on the requested data, usually using a WHERE clause, Cyral captures the filter being applied and emits this information in the query log, where it can be consumed by the Cyral policy evaluator, dashboards, and your team.
Policy enforcement
Cyral policy actions let you enforce the data access rules specified in your policies. Policy actions can include blocking access to data, rewriting datasets referenced by queries, and masking data.
To enable these actions on a repository, you must enable them in this
section and specify rules for them in your policy. Set the
Enable policy enforcements when data is violated toggle to
ON and turn on the applicable checkboxes, as described below.
See policy enforcement actions to understand how the different actions interact with one another and affect users and logs.
Enable block on violation
For a given session, Cyral blocks any attempted action that would violate your policy. After an action is blocked, the user’s session continues normally.
In the Cyral control plane UI click Data Repos ➡️ the name of your repository ➡️ Config
Open the Policy Enforcement section.
Turn on Enable policy enforcements when data is violated.
Turn on Block on violation
Set your policies to include your desired blocking logic.
Enable data masking
The data masking action obfuscates specific field values in each row returned, based on your policy rules.
In the Cyral control plane UI click Data Repos ➡️ the name of your repository ➡️ Config
Open the Policy Enforcement section.
Turn on Enable policy enforcements when data is violated.
Turn on Enable data masking
Set your policies to include contexted rules with your desired masking instructions.
Enable dataset rewrites
The dataset rewrite action rewrites table expressions in the user's query, replacing them with a substitute query that you have specified in the policy. The substitute query can be any valid query. The most common use case is to filter or limit the result set by introducing a WHERE or LIMIT clause.
In the Cyral control plane UI click Data Repos ➡️ the name of your repository ➡️ Config
Open the Policy Enforcement section.
Turn on Enable policy enforcements when data is violated.
Turn on Enable dataset rewrites
Set your policies to include contexted rules with your desired dataset rewriting instructions.
Tags
You can add one or more tags to a repository to make it easier to find in the Cyral control plane UI and the Cyral Access Portal.
- Click Data Repos ➡️ click your repo's name
- Click the ✏️ (pencil) icon in the upper right.
- In the Add Tags field, type the tag. Press
<Enter>or the spacebar to complete the entry of each tag, and add more tags as needed.- To make the tag visible in the Cyral Access Portal, make
sure the tag's name starts with
public:followed directly by the tag name, without spaces. For example, to show the tag ny-study-3 in the Access Portal, you would type the tag aspublic:ny-study-3. - To remove a tag, click its
xsymbol.
- To make the tag visible in the Cyral Access Portal, make
sure the tag's name starts with
- Click Save.
Learn more
To check and specify sidecar services for your repository, see Manage sidecar services for repositories.